Technique
Save Time By
Running automated checks to see if your firewall is working
Finding and plugging holes (before someone else plugs them for you)
Using common sense to increase your network security
I just got a call from an old friend who seems to frequently bump into very interesting security problems. My friend was helping a guy set up a home/small office network — and a good one. It had Windows XP on all the machines, XP Professional on the server, Internet Connection Sharing — the whole nine yards.
That evening, the guy’s adolescent daughter was startled to see a message pop up on her PC, filled with venomous, sexually explicit epithets, directed at her, personally. Whoever was responsible for the lessons in vulgar vernacular also transmitted a couple of compromising pictures.
On closer examination, we found that the pictures were fakes and that the attacker was probably known to the family and was hiding behind a newly created, virtually untraceable free e-mail account.
In a situation like this, do you need to check your security perimeter? Oh yes, indeed.
Approaching Your Security Perimeter
If you’ve followed the steps in Techniques 49 through 53, your computer is all ready for anything the world (or at least the Internet) can throw at it.
Right?
Well, yes and no.
The fact is that you’ll never be completely prepared for everything. New threats are surfacing every day. Some of them use old methods that your existing security settings should be able to withstand. Some of them come from out of the blue.
That’s why it’s important to check your PC and check the way that you run your network. It’s important not because you’ll be 100 percent certain that no intruder can ever appear, but because there’s a good chance you can do a better job with the tools at hand.
Running Steve Gibson’s ShieldsUp!
Steve Gibson (www.grc.com) has been protecting PCs since hard drives were powered by little fuzzy chipmunks running in circles. He used to stand next to banks of hard drives and yell, at periodic intervals, “Spin left! Spin right!”
Sorry. Couldn’t resist.
Steve’s ShieldsUp! is widely considered to be the granddaddy of all firewall tests. Yes, more probing tests are available. But none of them match the easy-to-use style and no-nonsense explanations of
ShieldsUp!.
Besides, it’s free.
You should run ShieldsUp! when you install a new firewall and every time you make a major change to your firewall.
To run ShieldsUp!
7. Start Internet Explorer and go to grc.com. Click the ShieldsUp! icon.
2, Scroll down the page a bit (Steve always has some interesting projects going), and click the ShieldsUp! link.
3, If you use a dial-up modem
► Download the Free IP Agent (see Figure 54-1).
► Double-click it and run it.
► Click Test My Shields, and skip to Step 5.
The IP Agent presents you with a dialog box like the one in Figure 54-2.
4, If you’re connected to the Internet via a DSL or cable modem, or using Internet Connection Sharing, scroll farther down the page (see Figure 54-3) and click the File Sharing button.
• Figure 54-1: Take Steve up on his offer to run the free IP Agent if you have a dial-up Internet connection.
• Figure 54-2: Use the IP Agent only if you’re connected to the Internet via a dial-up modem.
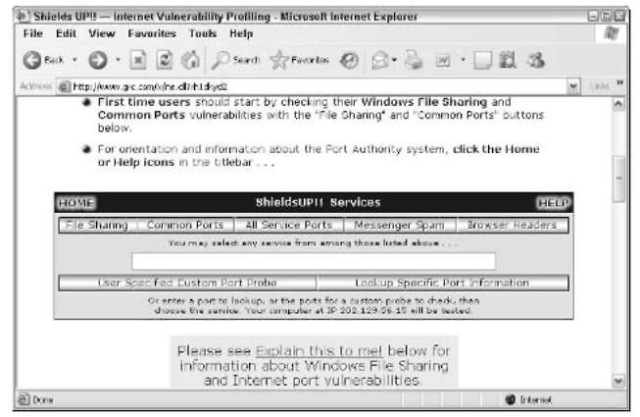
• Figure 54-3: Start by checking your File Sharing settings.
5, A report appears on your screen (see Figure 54-4). Heed it well.
6, Scroll further down the page and click the Common Ports button.
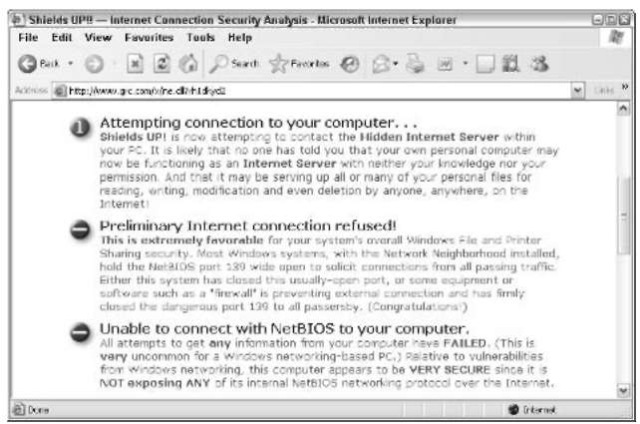
• Figure 54-4: A dean bill of health.
You get a second report that discusses port blocking (see Figure 54-5). If the Common Ports test tells you that an important port is open, you need to reconfigure your firewall to block it. The precise method varies depending on what kind of firewall you’re using. If you’re using Windows Firewall, from Service Pack 2, check Technique 50. If you have a hardware firewall (such as on a DSL router), you may have to dig into the guts of the box.
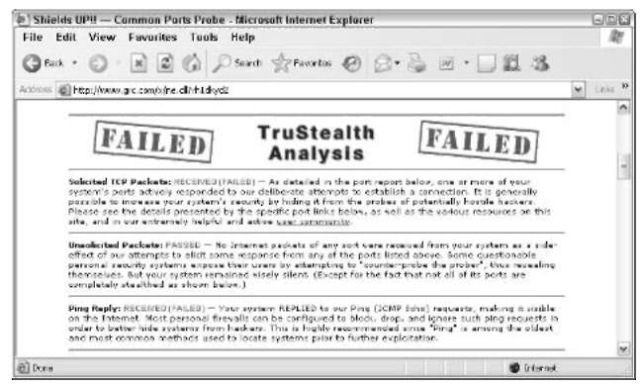
• Figure 54-5: If the prober can’t tell whether a program is “listening” to a specific port, that’s very good.
Few computers have all their ports blocked. In particular, experts disagree about the importance of port 80 being open.
Just a word or two about ports
At the risk of oversimplifying, a port is a lot like a telephone extension number. If you want to talk to somebody in a big office, you pick up the phone and dial the office’s main number. (That’s more-or-less analogous to the computer’s IP address; see Technique 45.) After you connect to the switchboard, you need to dial the person’s extension. Similarly, after you connect to a computer on the Internet, you have to connect to one of the programs inside the computer.
Each program listens to a specific port or group of ports. So if your PC connects to port 80 on the computer with an IP address of 208.215.179.139, you end up talking to the Web server.Any rogue cracker on the Internet who tries to get into your machine has to go through a port. The Common Ports test (refer to Figure 54-5) “calls” all 65,535 ports on your PC (or on your router, if you have one) and tells you whether any of them are vulnerable to an outside attack.
Running Microsoft’s Baseline Security Analyzer
Microsoft has a tool that examines your system to see if any important security patches are missing or if any obvious security exposures are hanging in the wind. Whereas Steve Gibson’s ShieldsUp! probes from the Internet in (see “Running Steve Gibson’s ShieldsUp!” earlier in this technique), the Microsoft Baseline Security Analyzer looks from the inside out.
The Baseline Security Analyzer goes through your Windows XP machine and checks most of its major components for missing security patches, gaping security holes, and little nit-picking things that you probably never knew existed (or didn’t exist, as the case may be).
To run the Baseline Security Analyzer
7. Start Internet Explorer and go to www. microsoft.com/technet/security/tools/ mbsahome.mspx.
Make sure that you get a version of the MBSA compatible with your version of Windows. In particular, if you have Windows XP Service Pack 2, you need version 1.2.1 or later.
2. Follow the instructions to download the MBSA file.
3. When the download is complete, double-click the icon and follow the wizard to install the program.
4. Double-click the icon to start MBSA.
You see the main screen shown in Figure 54-6.
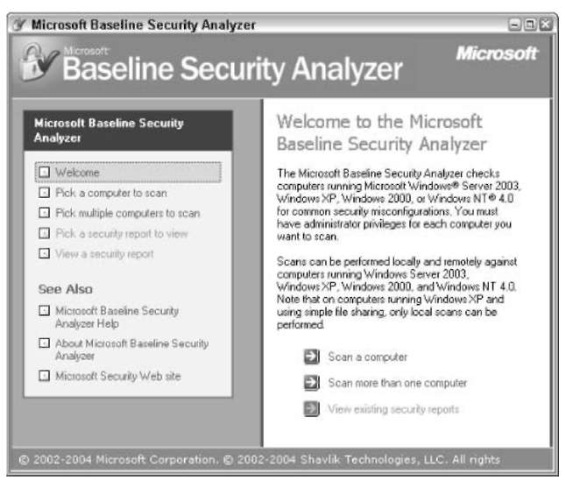
• Figure 54-6: Microsoft’s Baseline Security Analyzer starts here.
5. Click Scan a Computer and then click Start Scan.
MSBA produces a very detailed report of potential security exposures (see Figure 54-7).
6, Review the report for real vulnerabilities.
For example, the report for my production machine (see Figure 54-7) identified several vulnerabilities that I don’t consider to be problems: Having more than two administrators on an XP Home PC, for example, isn’t going to cause me any heartburn. And I don’t care to enable automatic updates, thank you very much (see Technique 55). Still, the report is worthwhile, and you should consider any exposures it identifies. If you need tips about the source of the problem or possible solutions, click the How To Correct This link.
MBSA leaves a lot to be desired because of its infuriatingly convoluted terminology. But it’s a powerful self-help utility that every Windows XP user should stick in his or her bag of tricks.
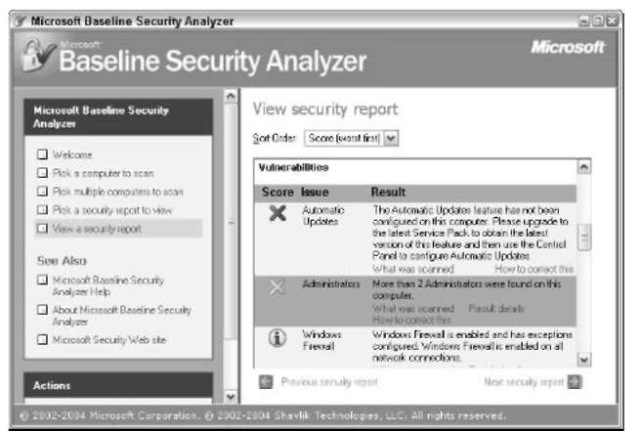
• Figure 54-7: The MBSA report gives you much insight — but may err on the side of too much security.
