Fraud: the Extent of the Problem
Payment card fraud is big business and hundreds of millions of dollars are lost every year to this criminal activity. The exact dollar amount of the losses depends upon the type of fraudulent activity and the country or region of the world where the fraud occurs. Since card programs – MasterCard,Visa,etc. – use different accounting methods to calculate losses,it is difficult to determine exactly how much the industry loses to fraud.
In economically developed countries,payment card fraud is more of a problem than in the European eastern block and other economically developing countries. In the developed countries,the use of payment cards represents a significant portion of each country’s payment system. With the increased usage of cards in these countries,there has also been an increase in payment card fraud.
Payment card fraud will increase in all countries as the card mix available to consumers expands,from credit cards to check cards,cash cards,debit cards, etc. In developing countries payment card fraud and the resulting losses associated with their use will be of increasing importance. If the dollar losses are significant enough,they could affect the economic health and prosperity of the people in the affected countries. The goal of the payment card industry is to see that this does not happen and to reduce the level of fraud in the economically developed countries.
Payment card programs spend millions of dollars each year on card security features,fraud prevention training,investigators,etc. As new card security features are developed and implemented,criminals immediately try to compromise them. A couple of examples will help illustrate this: the use of the hologram or optical variable device (OVD) and the encoded magnetic stripe. Shortly after cards with OVDs were issued to the public,criminals compromised them by using substitute OVD image foils on their counterfeit cards. In most instances the image foils they used had images that did not resemble a genuine image. Many of them were image foils on children’s stickers.
The criminal has only one question to answer when making a counterfeit card: will this card be a passable product,such that somebody will accept it and pay out cash or sell expensive goods because they think it is genuine? If the card is accepted at the point of sale, the criminal has succeeded.
In the 1980s organized criminal gangs in Southeast Asia had people who would supply them with holographically produced image foils with images closely resembling genuine image foils. The quality of the foils and the counterfeit cards they were on posed a significant threat to the payment card industry. Visual inspection of the card by the merchant was not sufficient.
The card payment system was in a transition period at this time,in part because of the quality of the Asian card. The magnetic stripe was becoming more important as a means of verifying the card and for payment authorization and reconciliation. Because the industry was becoming more dependent on the encoded magnetic stripe,new security methods and procedures were developed to insure its integrity.
The magnetic stripe is encoded with account information embossed on the card,and security information not embossed on the card. The magnetic stripe is discussed in more detail later in this article. It was not long after the magnetic stripe was introduced that criminals obtained magnetic stripe readers and encoders,and determined how the stripe,the information on it and the associated payment system worked. Electronic card fraud had begun and now magnetic stripe encoding,reencoding and skimming is a significant problem to the industry.
Criminals compromise card security features as soon as the features appear on issued cards. The card programs continue to research and develop new card security features to keep the products’ vulnerability to criminal activity as low as possible. It often seems like an endless succession of invent, implement,compromised,invent,implement,com-promised . . . The industry goal is to attempt to stay ahead of the criminals and to control losses resulting from their activities.
Types of Fraud
There are many types of payment card fraud. A few examples are:
• application fraud;
• unauthorized use of a card;
• use of another person’s identity to obtain credit or to make counterfeit identification documents;
• fraudulent bankruptcy schemes;
• counterfeit cards, white plastic and altered genuine cards;
• merchant bust-out and collusion fraud;
• magnetic stripe skimming and reencoding of card stripes.
• telephone and cell-phone card fraud;
• fraud schemes that use Internet web sites offering products or services, but requiring the buyer to give a credit history or credit card number first.
A detailed discussion of each of these is not the purpose of this article. However, where payment cards are widely accepted, in the United States and Canada, for example, the use of counterfeit and altered cards seems easier for the criminal. This is in spite of card program and issuer rules, neural network software systems and regulations governing merchant responsibility. The main issue for the industry is how to control losses.
Payment card fraud is cyclical. Counterfeit card use may be high for a few years and then drop off; application fraud may take over, only to be replaced by an increase in merchant fraud; skimming is currently the explosive area. Why this occurs is unclear.
Organized Efforts at Fraud
Payment card fraud is a worldwide problem perpetrated by criminals acting alone or in organized groups. The organized criminal gangs are usually international in scope. They have sources to supply them with materials to make counterfeit cards, security features like OVDs and special embosser punch and die sets, and a distribution network for completed or partially completed cards. There is also a network of people to use the cards wherever shipped, and to funnel money back to the criminal leadership for use in other criminal enterprises.
In the early 1990s Detective Chief Inspector John Newton of the Metropolitan Police, London, carried out a worldwide study of organized Southeast Asian groups active in payment card fraud at that time. One of his conclusions was: ‘Despite its undoubted success the card payment system does have weaknesses, which are exploited by organized criminals. Counterfeiters, in particular, rely upon the almost universal acceptability of payment cards to make their criminal enterprises extremely profitable. However, the industry and law enforcement agencies are not standing still and allowing criminals to plunder the system without fear of disruption and arrest.’ Newton found that counterfeit payment cards made in Southeast Asia were being distributed to, and used in, the United States, Canada, Europe and many other countries around the world. He also learned that many of the people arrested in one region of the world were re-arrested in other regions, or they were in some way connected. The cards they were arrested with were often linked together forensically, showing that the card components had common source characteristics.
Some of the activities engaged in by these organized groups are:
• counterfeiting of cards and card security features;
• false identification documents;
• the use of payment card fraud to fund other criminal activities.
The information to make cards and the equipment and items needed for counterfeiting them are available from many different sources. The Internet is one such source of information. Some Internet sites contain programs to generate possible active account numbers and information on how to encode a stripe and what information is encoded on it. Magnetic stripe readers and encoders, embossers, etc. can be purchased from catalogs, over the Internet, value-added distributors, and even as second-hand office equipment. Frequently, equipment purchased in one part of the world is small enough to be hand-carried or shipped to another part of the world, where it is used to personalize cards.
It is not necessary to have the card to commit fraud: having only the account information is sufficient. Some gangs have members who just obtain account information that is used on their counterfeit and altered cards. The account information necessary to carry out a transaction is called an ‘access device’. When a criminal has the access device, he or she has access to the full line of credit or services available up to the limit on that account. Access device fraud is prosecuted in the United States under local and state criminal statutes, and Federal Statute 1029, which makes it a Federal crime as well.
Genuine Cards
Payment cards are made in secure, authorized manufacturing facilities. Each manufacturer has some proprietary procedures or equipment they use in making their cards, but the result is nearly the same. How is a genuine card made? The following general discussion covers most manufacturers:
• The card issuer receives permission from the card program to issue cards. Only banks are authorized to issue payment cards. Cards can be cobranded, where a nonissuer like Shell Oil Company can issue a card in conjunction with Chase Manhattan Bank.
• The issuer creates artwork for the card or creates the artwork in conjunction with the card manufacturer’s graphic arts section. The card program has very specific specifications concerning card real estate and how much of it can be used by the issuer and how much by the program. The issuer and manufacturer must conform to these standards.
• As the artwork is prepared, the printing process(es) for each component part of the card is determined. It is doubtful that the whole card will be printed using only one printing process. Genuine cards are usually printed using a combination of screen and offset printing.
• The printing plates for each phase of the printing process are made from the artwork.
• The inks are selected, mixed and color tested.
• The card is not printed as a single card but as one of a number of cards on a large sheet of plastic. In some printing plants, printing as many as 80 card images on one sheet of plastic is a common practice.
• After printing, the sheet of card images is laminated to protect the printed material from damage during card usage.
• The magnetic stripe is applied to the card as part of the lamination process.
• The individual cards are die cut from the sheet, and the signature panel and OVD are attached to the individual card.
• The card is then personalized, embossed, encoded and sent to the cardholder.
The Card in Greater Detail
A payment card is a sandwich of plastic. It has a white core, covered by a translucent overlay on the front and back (Fig. 1A). The white core plastic contains the printed material, program and issuer names, logos, ownership information on the back of the card, etc., which is covered by the overlay for protection. The OVD is hot stamped to the overlay on the front of the card (Fig. IB). Not all card programs use an OVD, so the presence of this feature is dependent upon the card program and issuer. The back of the card contains a magnetic stripe and signature panel (Fig. 1C). The encoded information on the magnetic stripe is for payment authorization and reconciliation process, and the signature panel is for the cardholder to sign his or her name after receiving the card.
A card is a combination of numerous parts and technologies. The following discussion explains how the card should be viewed and something about each part.
The plastic
The plastic is polyvinyl chloride (PVC). The nominal size of the card is 3.370 inches (85.60mm) wide, 2.125 inches (53.98 mm) in height, 0.030 ± 0.003 inches (0.76 + 0.076 mm) thick, and the corners are rounded with a radius of 0.125 + 0.012 inches (3.175 + 0.305 mm). The card is die cut from a larger sheet. Depending upon the card manufacturer, the core may be a solid sheet of white PVC or two thin sheets sandwiched together which are sealed during lamination. Typically, the core is 0.027 inches (0.686 mm) thick and the thickness of each overlay sheet is 0.0015 inches (0.0381 mm). This size card is described as an ID-1 card by International Standards Organization (ISO) Standard 7810.
Not all PVC is the same. For example, two PVC plastic manufacturers may use the same compounds in their plastic, but the printability characteristics and whiteness can be very different. Since the core is a vital part of the package, because all of the printing is done on its surfaces, printability is very important.
The composition of the translucent PVC overlay material can also be different. The UV characteristics of the overlay are very critical because of UV fluorescent ink images printed on the core. The overlay must allow the UV light to pass through it and react with the UV printed ink image so it will fluoresce.
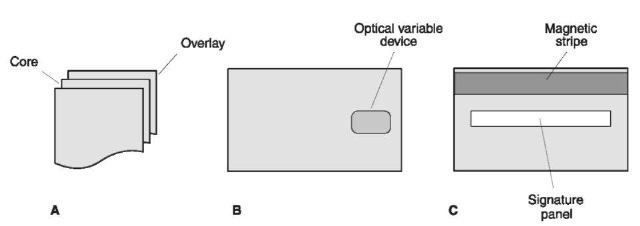
Figure 1 (A) A payment card is a sandwich of polyvinyl chloride. The core is white and is covered by translucent overlays. (B) Some card programs use an optical variable device (OVD) on their cards as a security feature. (C) The back of the card has a magnetic stripe and a signature panel. See text for details.
Ink
Both offset and screen inks are used to print on cards. UV curing inks or drying agents are added to the ink to expedite the drying process. In either case, it is critical that ink surfaces are dry before they make contact with another sheet of plastic.
A color shift occurs in the ink during lamination. To compensate for this color shift, a test is conducted to insure that the ink color after lamination is correct. The final ink color required is the one after lamination.
Signature panel
The signature panels are as varied as the card programs and issuers. Some are plain, offering little or no security, others are sensitive to solvents, or have complex printed backgrounds or other high security features. The signature panel may be one of the following:
• A preprinted hot stamp panel attached to the card.
• Several layers of screen-printed ink applied to the card, consisting of a base layer with printed information over it identifying the card program.
• Special paper or printed material and inks sensitive to solvents that will react with the stripe if an attempt is made to alter the written signature.
• A high security printed panel with a variety of printing traps to prevent duplication by using a scanner.
The panel may contain the account number indent printed within it.
Magnetic stripe
A magnetic stripe payment card can have three encoded tracks of information, depending upon the width of the magnetic medium. If the stripe width is approximately 7/16 inches (11.11mm), three tracks of information can be encoded, and when the stripe width is approximately 5/16 inches (7.94 mm), two tracks of information can be encoded. Other technologies, such as watermark magnetic, etc., are beyond the scope of this article.
Encoding consists of a series of zeros and ones, a binary format, where each number, letter or character is a unique combination of ’0′ and ’1′. ISO Standard 7811-2 and 7811-4 establishes the number of bits per character. The standard also requires an odd parity for each character bit set, regardless of the character, so included in the character bit set is a parity bit to insure an odd parity for the set. Odd parity is achieved by adding a one or zero to a bit set, insuring it has more ones than zeros.
The following is a brief description of the characteristics of a magnetic stripe data format based on ISO standards.
Track 1 This is known as the International Air Transportation Association (IATI) track. The character configuration is seven bits per character, including the parity bit, and the maximum information content is 79 alphanumeric characters, which includes the start sentinel, end sentinel and longitudinal redundancy check character (LRC) at a recording density of 210 bits/25.4 mm per inch. The card magnetic stripe data format for track 1 is illustrated in Fig. 2 and described below. The encoded information is subdivided into fields read from right to left, as if the reader were looking at the back of the card.
A. Starting clocking bits Before data is encoded a string of clocking bits is encoded and each bit equals zero. Clocking bits provide a timing mechanism for starting the reader synchronization process before the read head gets to the start sentinel.
B. Start sentinel The start sentinel (%) is a defined number of bits informing the magnetic stripe reader that the following encoded information will be data.
C. Format code The format code consists of two digits telling the magnetic stripe reader how to interpret the data encoded in the data field. ISO established a standard of F2F (frequency-double frequency) for payment card magnetic stripes.
D. Primary account number (PAN) The PAN field is the first data field read by the magnetic stripe reader and can have a maximum of 19 digits. The card program and issuer establish the PAN and its format in the data field. The format of the PAN is not the same in this field for all tracks on all payment cards.
E. Field separator Following the PAN is a field separator ({). Its purpose is to notify the magnetic stripe reader that all encoded data called for in the preceding field is encoded and a different information field is about to begin. On track 1, it signals the end of a numeric data field, the PAN, and the beginning of an alpha data field, the name of the card owner. On tracks 2 and 3, it signals the end of the PAN and the beginning of the next, numeric data field. The PAN field is frequently less than the allotted 19 digits. If the encoded number is 16 digits, the issuer or program may still require the use of the full 19-digit field by leaving the unused digits blank.
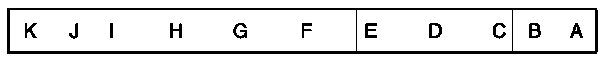
Figure 2 The IATA track or track 1.
F. Cardholder name The next field on track 1 is the cardholder name, and its allotted size is a maximum of 26 alpha characters. How much of this field is used and the order in which the name is encoded (last name first, first name second, initials third, etc.) are established by the card program and/or issuer.
G. Field separator A field separator follows the card owner’s name. Its function is the same as described in ‘E’ above.
H. Additional data and discretionary data field The next field is a numeric field containing encoded information, the expiration date, service code, pin offset, ‘Card Verification Value’, etc. It is in this field that the VISA, Card Verification Value (CVV) and MasterCard, Card Verification Character (CVC) are located. The CVV and CVC numbers are security features established by the programs to insure the integrity of the encoded data on the stripe. Each card program and/or issuer can dictate the information encoded in this field. The ISO Standard establishes the number of characters allotted to each specific entry. For example: the expiration date, four digits; the restriction or type, three digits; the pin offset or parameter – optional – five digits, etc. Some issuers require the expiration date and ‘member since’ or ‘valid from’ date. In this situation, the date field will be eight digits rather than four digits. To do this the program obtains a variance from the standard. The card program and issuer establish what numeric information is encoded in this field, what it means, and how it is used.
I. End sentinel The end sentinel (?) is encoded after the discretionary data field. The end sentinel informs the magnetic stripe reader that the data fields of the stripe are now encoded and no further data is encoded.
J. Longitudinal redundancy check character (LRC) The encoding of an F2F format for payment cards call for an odd parity on each track. Each character has its own parity bit already; the LCR insures that the string of bits also has an odd parity.
K. Ending clocking bits After the LRC there is another series of clocking bits to verify the timing of the synchronization process.
Track 2 This was developed by the American Bankers Association (ABA) for the automation of financial transactions and its encoded information is numeric only, limited to 40 characters, including the start sentinel, end sentinel and LRC. The character configuration is five bits per character, including the parity bit, at a recording density of 75 bits/25.4 mm per inch.
Track 2 is located below track one on the magnetic stripe (Fig. 3). There is a small separation between the two encoded tracks to prevent magnetic field interference during encoding and reading. Since a detailed description of each field for track 1 is given above, and the explanation is the same for track 2, only the function for each field is given:
A clocking bits;
B start sentinel – HEX B;
C primary account number (PAN);
D field separator – HEX D;
Eadditional data or discretionary data field;
F end sentinel - HEX F;
G longitudinal redundancy check character (LRC); H ending clocking bits.
The hexadecimal (HEX) is a numeric system based on powers of 16. Valid hex digits range from 0 to 9 and A to F, where A is 10, B is 11,… Fis 15. In the above, HEX-B would be the encoded binary equivalent of ’11′, HEX-D is the binary equivalent of ’13′, etc.
Track 3 This was developed by the thrift industry and is a numeric data-only track with 107 characters, which includes the start sentinel, end sentinel and LRC (Fig. 4). The encoded density of track 3 is 210/ 25.4 mm bits per inch with five bits per character. The information encoded in the use and security data and additional data fields is updated after each transaction, allowing a card encoded on track 3 to be used in online and offline systems. Since a detailed description of each field for track 1 is given above, only the function will be given for each field in track 3, as they, too, overlap:
A clocking bits;
B start sentinel – HEX B;
C format code;
D primary account number (PAN); Efield separator – HEX D;
F use and security data, and additional data field; G end sentinel – HEX F;
H longitudinal redundancy check character (LRC); I ending clocking bits.
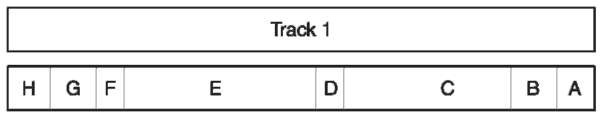
Figure 3 The ABA track or track 2.
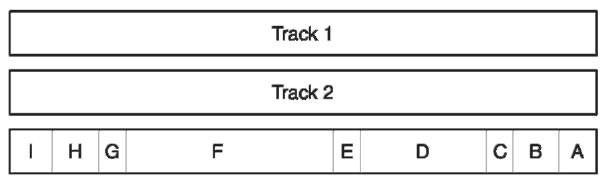
Figure 4 Track 3 was developed by the thrift industry and contains information that is read and updated after the transaction has occurred.
Optical variable device (OVD)
Holograms have been used on payment cards for many years. The OVD foil is hot stamped on top of the front overlay of the card. Some European cards also have OVD foils hot stamped on the back of the card. Not all card programs require the use of holograms. The most popular ones requiring an OVD are MasterCard, Visa, JCB, Novus, and Europay, etc.
A hologram is traditionally defined as a three-dimensional image foil. However, not all holograms are three-dimensional. There are two-dimensional and three-dimensional foils. Some companies have trademark names for their OVD products, such as Gyro-gram, Optoseal, Keingram, Exelgram, etc. Although there are these and many others, they all have one thing in common: a passable product of these OVDs can be used in their place on counterfeit documents.
Probably the best topic on OVDs as a security device is Optical Document Security (see Further Reading). Having a copy of this resource in a technical library on questioned documents is essential. The reader is referred to this text for a more comprehensive study of OVDs and optical document security.
Embossing
Embossing is the production of the three-dimensional characters rising above the front surface, and recessed in the back of, the card. There are many different type/ styles available for embossing cards. The ISO Standard 7811-1 mandates the type/style for the account number as a Farrington 7B OCR type. The remaining material, alphanumeric, on the card can be any type design as long as its size conforms to that allocated by the ISO standard. Some of the designs used over the years are Standard Goth, Simplex, Bradma, etc.
Embossers and embossing have unique characteristics that make them identifiable. The examination of embosser type is a three-dimensional study: in Fig. 5, the ‘X’ coordinate is the width of the typeface;the ‘Y’ coordinate its height, and ‘Z’ is the depth of the impression in the plastic.
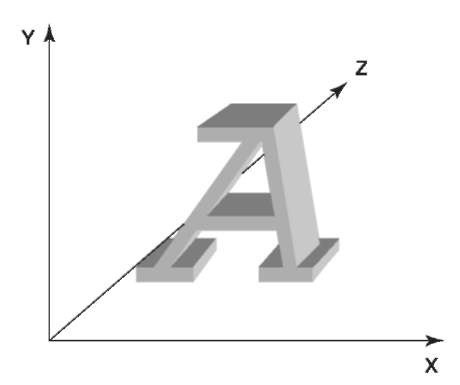
Figure 5 The examination of embosser type is a three-dimensional study.
Figures 6 and 7 show an embossing punch and die describing each of its surfaces. Each surface shown can leave a record of its presence on the plastic overlay surface of the card. These defects, together with the class characteristics of the punch and dies, and the machine collectively, are what make embossing identifiable.
When the card is examined, it is important to observe the presence of any defects on the overlay of the card Fig. 8.
Printed material on the core plastic, such as the text or planchettes added to the background printing, make it difficult to focus on the top of the overlay. The interference caused by this background material is referred to as optical noise. Since the overlay is only about 0.0015 inches (0.031 mm) thick, it is difficult to focus on its top surface and ignore the optical noise under it on the core.
To illuminate the top surface properly, the angle of the light must be very small, as shown in Fig. 9. Use of a stereomicroscope and fiberoptic light source is best for this examination. Varying the angle of the card and light to the objective in small increments allows the examiner to see the greatest overlay surface detail possible. The purpose of this examination is to reflect light off the surface of the overlay, because this is the surface where the striations and defects are located. The use of a comparison microscope is essential when comparing the striations on separate cards or a card with the punch and die from a suspected embossing machine.
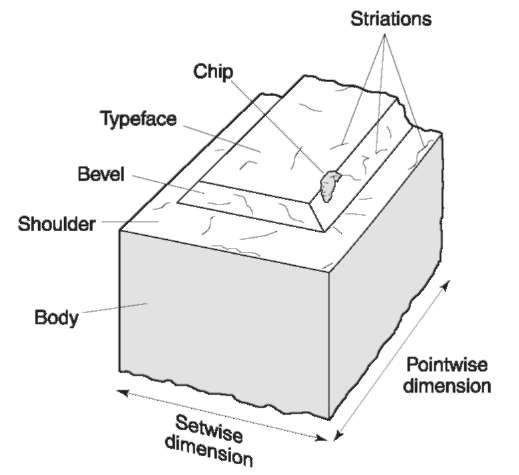
Figure 6 The parts of the embossing punch. This punch has a chip in the typeface and bevel, and striations on the typeface, bevel and shoulder. These individual characteristic defects are recorded on the surface of the plastic during the embossing process.
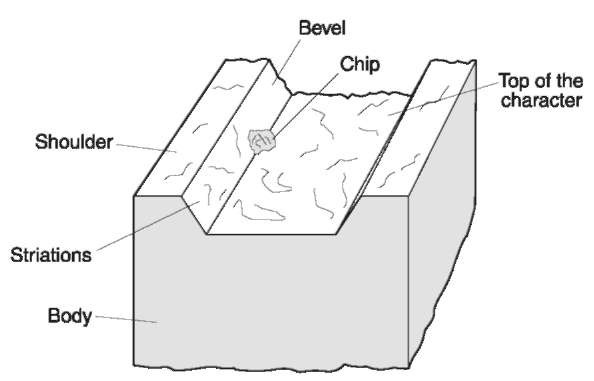
Figure 7 Defects (a chip and striations) in an embossing die.
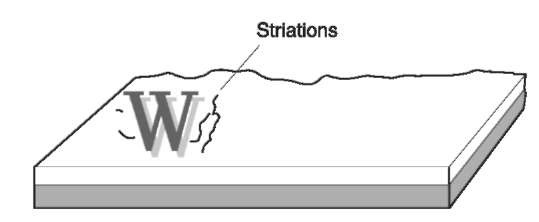
Figure 8 Surface defects on the overlay of an embossed ‘W’. These defects may be found on the front and back of the card, either on or near the embossed character or inside it.
Two other methods used to assist in the examination of the card overlay surface are the vacuum deposition of a thin, opaque, layer of metal over the surface of the card where the embossing is located. The evaporation of this thin film is applied to the card surface before the embosser examination begins. This thin metallic film covers the surface of the overlay where the embossing is located and acts as a first surface mirror, highlighting the defects. Because this thin film is opaque, the problem of optical noise caused by the background on the core is overcome. A second method is the use of Mikrosil casting material. While this is a good material to show chips and larger defects in the plastic overlay surface, it does not seem to work as well for very fine microscopic detail defects.
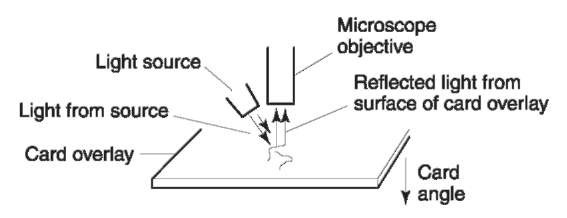
Figure 9 The relative angle of the light source to the card and the microscope objective for an examination of the overlay surface.
Counterfeit Cards
The counterfeiter has one objective: to produce a passable product. To be successful, the product only needs to pass the first line of inspection, the point of sale. Counterfeit currency must look and feel like genuine currency, while payment cards and identification documents must only look as if they are real.
When counterfeiting currency, it is important to have a piece of genuine currency from which to model the counterfeit. Since most people are familiar with currency, it is also important for the counterfeiter to copy its characteristics with attention to detail. Counterfeit currency is made using standard printing methods – offset, screen, intaglio and typographic – or a genuine piece of currency is copied on a color copier. Currency is not as complex a document for forensic examination as a payment card. The pictorial appearance and tactile qualities of genuine currency are well established and rarely changed. People know what a $20.00 US Federal Reserve note looks and feels like.
Counterfeit payment cards are more complex and varied than counterfeit currency, so the card counterfeiter has more of a challenge. There are hundreds of card programs and tens of thousands of issuers, and each one issues a number of different cards. Except for the program logo, the balance of the card real estate is very different for each card, often even from the same issuer. It is no wonder that merchants and point of sale personnel are not sure whether a payment card is genuine.
The number of printing processes available to the card counterfeiter is more numerous than those used by currency counterfeiters. Some of the processes used to print counterfeit cards are: offset, rainbow, screen, hot stamping, typographic or letterpress, thermal mass transfer, thermal dye diffusion, computer printers using transparencies that are then bonded to a plastic card, laser engraving, etc. Frequently, multiple printing processes are used to make a single counterfeit card. Linkage of cards based on the printing process used to print each area of the card is critical. Counterfeiters can, and do, share negatives and computer image software. They can, and do, make changes in the images they acquire, or they use a different combination of images and different printing process to print those images. That is why it is critical to determine the printing processes used to print each card. Effective card linkage is based on common information on the counterfeit cards, the printing processes used, the common characteristics of the OVD and signature panel, and the fabrication techniques used to make the card and its component parts.
Further, the card OVD can be any of the following types: two-dimensional and three dimensional holograms, hot stamped images on diffraction foils, computer generated images using commercially available silver and gold paper, etc. Image analysis and linkage of OVDs is critical to establishing a common source of these devices. When examining hot stamped images on diffraction foil, it should be remembered that two similar images might have been made using different hot stamp dies. The details of the images must be examined carefully and be in complete agreement before concluding that two or more of them have a common source. The same basic principle also applies to the other card components. If all of the components of two cards agree, then it can be safely said that the cards come from a common source. If one component differs, then it can only be said that all of the components of the card agree except that one which has a different source from its counterpart on the other card(s).
The type of signature panel, or the printing methods used to make it, are very important in linking cards. The method of printing the panel or applying it to the card must be determined.
The fabrication techniques used to make the counterfeit card must be determined, in addition to the encoding of the magnetic stripe. It is not just what information is encoded on the stripe but an analysis of that encoding to determine something about the characteristics of the encoder that is used that is important. It is the combination of the different technologies used to make a counterfeit card and their forensic examination that make it a more complex document to examine than a piece of counterfeit currency.
Because there are so many different issuers of payment cards, it is impossible for a merchant or bank teller to know what each issued card is supposed to look like. A single issuer can issue several different cards authorized by more than one card program. For example, the issuing bank may issue gold and platinum cards, individual and corporate or company cards, cobranded and executive cards, etc. as separate product lines. The only common characteristic these cards share are those features mandated by the card program(s) authorizing the issuance of a card with their logo, signature panel, OVD, etc.
Counterfeiters can take many more liberties with the balance of the material on the card. They can use the same issuer name and logo, front plate details and back plate details for both a MasterCard and VISA card. Genuine MasterCards and VISA cards will not have the same information on the front and back of the card. In fact, the issuer’s name that counterfeiters choose does not even have to exist. Counterfeiters can design a MasterCard using their logo and the name of a fictitious bank. They can create a logo for the bank and use an account number from another bank that does exist. As long as the merchant takes the card, because it is a passable product, the fraud is committed. Further more, counterfeiters are not obliged to adhere to the same quality and physical standards of a genuine card manufacturer. The card manufacturer must make a product that will last for years; the counterfeiter’s card need only last for a couple of passes.
The linking of counterfeit cards is critical to an investigation. The Forensic Document Examiner plays a major role in this area because of unique skills developed over years of examining documents. A card is another form of a document and is forensically linked with other cards, as outlined below.
Fabrication techniques
Counterfeiters fabricate counterfeit cards using the same general techniques and similar equipment as a genuine manufacturer. The differences between the two are in the way they make the cards. For example, the Southeast Asian cards referred to above were fabricated as individual cards, not a part of a large sheet of cards. The printing was on the front and back of the white core and the card. The individual card was covered front and back with a precut card size overlay, and the package of overlays and core were placed in a mold, where heat and pressure were applied to seal the overlay to the core. While the card was still warm, small pickers were used to remove the card from the mold. The fabrication techniques were the same for different card program cards. Although the printed material on the cards had nothing else in common, these cards were linked by the common characteristics resulting from their fabrication.
Embossing
Cards fabricated in different counterfeiting plants may be linked by common embosser characteristics. The techniques for examining and identifying embossed characteristics have been discussed above. The author has linked together cards, by their embossing, which were obtained in Hong Kong, the United States and Europe. Linking cards by the embosser or punch and die used to emboss material on the card is very effective.
One word of caution, not all of the embossed material on a card has to have been embossed on the same embosser or with punch and dies on the same machine. An example will illustrate this point. In the Hong Kong case, cards were shipped with embossed security logos and no other embossing on the card. The other embossed information was being added to the cards at their final destination. The embossed logos were linked to each other even if the remaining embossed information was done on different machines and could not be linked.
Printing on the card
The card must be broken up into its component printed parts to properly link them together by printing. For example, a MasterCard logo has at least four parts: the line that defines the area around the logo and OVD; the left part of the globe; the right part of the globe; and the word ‘MasterCard’. Each of these component parts of the logo can be made with different source images that are interchangeable. It has been the author’s experience after examining thousands of counterfeit cards that these parts of the logo are frequently made by mixing and matching interchangeable images that may come from different sources. Therefore, any linking system must consider this possibility.
The same is true for the balance of the printed material on the front and back of the card. A subgroup of experts developed the Interpol Forensic Classification System for Payment Cards, which is the most comprehensive forensic system for linking cards based on their components. Printing is one of the major areas of the Interpol classification system. The group did not address linkage of embossing. It was felt that such linkage was best left to the local laboratory forensic document examiner, as embossers were portable, and based on collective experience, international linkage of card embossing was rare. The system is designed to link cards from the same and different programs, different kinds of cards, printed material on card stock, OVDs and signature panels.
Magnetic stripe
It is not as yet possible to say with certainty that two cards were encoded on the same encoder. In certain instances it is possible to determine that two encoded magnetic stripes were encoded on different encoders, based on the characteristics of the encoder as recorded on the card’s magnetic stripe. A special encoder analyzer is needed to perform this examination.
If the encoded information on the stripe of two different cards is the same, a linkage by encoded information is possible. This does not occur very frequently.
Optical variable device
Cards can be linked by their OVD. An image analysis of the OVD for common characteristics can reveal image features that can be used to link the image foils. Not all image foils have two- or three-dimensional images. Many counterfeit cards have reflective foils that are hot stamped to the card using a hot stamp die, and then using another hot stamp die with an image resembling a card program’s genuine image. Sometimes the hot stamp image die and the foil are used as a single hot stamping, not a multiple hot stamping operation. Again, this demonstrates the importance of the fabrication technique of a card component. Linking OVDs is a significant part of the Interpol Forensic Classification System.
Where are Payment Cards Headed?
Payment cards are becoming even more complex. Chip cards are becoming more popular as the payment card system moves in that direction. Individual card security will depend more on cryptography, biometrics, digital systems and neural networks to insure the cardholder and the card in his or her possession go together, and to protect the card payment system.
Summary
Payment card fraud is an international problem. Organized gangs manufacture, distribute and use counterfeit cards around the world. Their cards are made using many of the same technologies as genuine cards. The forensic examination of counterfeit payment cards is performed by forensic document examiners because they have the unique skills to perform the required examinations involving printing processes, embosser identification and card linkage.
Cards are complex items and consist of components that have different common sources. Linking different components forensically assists investigators in suppressing the source of each component. One of the more important functions of the forensic document examiner is the linkage of counterfeit cards based on their common characteristics. Finding that counterfeit cards are linked by a single component does not mean that every other component on the cards are also linked; it only means that the one component has a common source. Linking each individual card component and the fabrication technique is necessary to reach the conclusion that the cards and their components come from common sources. The Interpol Payment Card Classification System is based on this concept, and it is designed to link forensically individual card components, cards and fabrication techniques.
Payment card design by card programs is moving in new directions. Chip cards, cryptography, biometrics and neural networking are being used now, and will be used to a greater extent in the future to protect the payment card system. As card technology develops, the forensic examinations required will have to be further developed to keep up with an ever-changing payment card.
