abstract
The reference model presented in this article encourages the breakdown of M-Health systems into the following five key dimensions: (1) Communication Infrastructure: a description of mobile telecommunication technologies and networks; (2) Device Type: the type of device being used, such as PDA, sensor, or tablet PC; (3) Data Display: describes how the data will be displayed to the user and transmitted, such as images, email, and textual data; (4) Application Purpose: identification of the objective for the M-Health system; (5) Application Domain: definition ofthe area in which the system will be implemented. Healthcare stakeholders and system implementer can use the reference model presented in this article to understand the security implications of the proposed system and to identify the technological infrastructure, business requirements, and operational needs of the M-Health systems being implemented. A reference model that encapsulates the emerging M-Health field is needed for cumulative progress in this field. Currently, the M-Health field is disjointed, and it is often unclear what constitutes an M-Health system. In the future, M-Health applications will take advantage of technological advances such as device miniaturizations, device convergence, high-speed mobile networks, and improved medical sensors. This will lead to the increased diffusion of clinical M-Health systems, which will require better understanding of the components that constitute the M-Health system.
introduction
M-Health is defined as “mobile computing, medical sensor, and communications technologies for healthcare” (Istepanian, Jovanov, & Zhang, 2004, p. 405). The first occurrence ofthe term M-Health in the literature was in the “Unwired E-Med” special issue on Wireless Telemedicine Systems (Istepanian & Laxminaryan, 2000). Since then, there has been an increased use of the term, encapsulating various types of healthcare systems. The use of the M-Health terminology relates to applications and systems such as telemedicine (Istepanian & Wang, 2003), telehealth (Istepanian & Lacal, 2003), and biomedical sensing system (Budinger, 2003). Until now, there have been considerable confusion and overlap with the use of these terms (Tulu & Chatterjee, 2005).
Rapid advances in Information Communication Technology (ICT) (Godoe, 2000), nanotech-nology, biomonitoring (Budinger, 2003), mobile networks (Olla, 2005a), pervasive computing (Akyildiz & Rudin, 2001), wearable systems, and drug delivery approaches (Amy et al., 2004) are transforming the healthcare sector. The insur-gence of innovative technology into the healthcare practice not only is blurring the boundaries of the various technologies and fields but also is causing a paradigm shift that is blurring the boundaries among public health, acute care, and preventative health (Hatcher & Heetebry, 2004). These developments not only have had a significant impact on current e-health and telemedical systems (Istepanian, Jovanov, & Zhang, 2004), but they also are leading to the creation of a new generation of M-Health systems with a convergence of devices, technologies, and networks at the forefront of the innovation.
This article proposes the use of a five-dimensional reference model in order to assist system implementers and business stakeholders in understanding the various components of an M-Health system. The approach used by the this article focuses on identifying different dimensions of a Mobile Healthcare Delivery System (MHDS) (Wickramasinghe & Misra, 2005), which then can be used to identify user security requirements for different categories in an organized manner.
These dimensions were driven from our literature review (Bashshur, 2002; Bashshur, Reardon, & Shannon, 2000; Raskovic & Jovanov, 2004; Iste-panian, Laxminaryan, & Pattichis, 2006; Jovanov, Milenkovic, Otto, & Groen, 2005; Field, 1996; Moore, 2002; Olla & Patel, 2003), and the model reflects a combination of various classification schemes proposed in earlier studies in order to classify telemedicine and telehealth systems.
Based on the previous definition, M-Health is a broad area that transcends multiple disciplines and utilizes a broad range of technologies. There is a variety of applications, devices, and communication technologies that are emerging in the M-Health arena and that can be combined to create the M-Health system. The dimensions consist of the following:
1. Communication Infrastructure. Description of the mobile telecommunication technologies that will be used, such as Bluetooth, wireless local area networks, or third-generation technologies (Olla, 2005a).
2. Device Type. Relates to the type of device being used to collect the medical data, such as Personal Digital Assistance (PDA), sensor, or tablet PC (Parmanto, Saptono, Fer-rydiansyah, & Sugiantara, 2005).
3. Data Display. Describes how the data will be displayed and transmitted to the user through images, e-mail, textual data, and other types of data presentation languages (Tulu & Chatterjee, 2005).
4. Application Purpose. Identification of the objective for the M-Health system (Field, 1996).
5. Application Domain. Definition of the area in which the system will be implemented, such as clinical (e.g., dermatology, radiology, etc.) or non-clinical (e.g., billing, maintenance, etc.) domains (Bashshur et al., 2000).
Selecting different alternatives in the five dimensions will have implications on the functionality of the system; however, the key focus of this discussion will be the emphasis on how the security and integrity of the M-Health system is maintained, based on the dimension choices.
The rest of the article is organized as follows. “Background of M-Health” features a brief background of the evolution of M-Health. “Mobile Healthcare Delivery System Networks” provides an overview of existing and new mobile technologies suitable for the healthcare sector. “The M-Health Reference Model” introduces the five dimensions of the M-Health reference model. The penultimate section uses the reference model to decompose a real-life mobile health delivery system in order to illustrate the security concerns. This is followed by the conclusion.
background OF M-Health
The phenomenon of providing care remotely using ICT can be placed into a number of areas, such as M-Health, telemedicine, and e-health, but, as summed up by R. L. Bashur, President Emeritus of the American Telemedicine Association, the terminology is not the important aspect. “It does not really matter what we call it or where we draw boundaries____collective and collaborative efforts from various fields of science, including what we call now telemedicine is necessary” (Bashshur, 2002, p. 7). Emphasis on the various components and objectives of the various types of systems should be the priority, as this will increase the chances of implementing efficient and effective systems, of generating viable business models, and of creating secure systems that meet the needs of the stakeholders (Olla & Patel, 2003). Over the evolution of telemedicine, new terminologies have been created as new health applications and delivery options became available and as application areas extended to most healthcare domains. This resulted in confusion and identification of what falls under telemedicine, and what falls under telehealth or e-health became more complicated as the field advanced. New concepts such as Pervasive Health and M-Health also are adding to this confusion. Before understanding the scope and components of M-Health, it is important to mention briefly the history of telemedicine and the advancements of mobile networks, which are collectively the foundation of M-Health. The evolution and growth of telemedicine is correlated highly with ICT advancements and software development. Telemedicine advancements can be categorized into three eras (Tulu & Chatterjee, 2005; Bashshur et al., 2000).
The first era of telemedicine focused solely on medical care as the only function of telemedicine. This era can be named as the telecommunications era of the 1970s. The applications in this era were dependent on broadcast and television technologies, in which telemedicine applications were not integrated with any other clinical data. The second era of telemedicine, a result of digitalization in telecommunications, grew during 1990s. The transmission of data was supported by various communication mediums ranging from telephone lines to Integrated Service Digital Network (ISDN) lines. During this period, there were high costs attached to the communication mediums that provided higher bandwidth. The bandwidth issue became a significant bottleneck for telemedicine in this era. Resolving the bandwidth constraints has been a critical research challenge for the past decade, with new approaches and opportunities created by the Internet revolution. Now, more complex and ubiquitous networks are supporting telemedicine. The third era of telemedicine was supported by a networking technology that was cheaper and more accessible to an increasing user population. The improved speed and quality offered by Internet is providing new opportunities in telemedicine. In this new era of telemedicine, the focus shifted from a technology assessment to a deeper appreciation of the functional relationships between telemedicine technology and the outcomes of cost, quality, and access.
This article proposes a fourth era that is characterized by the use of Internet Protocol (IP) technologies, ubiquitous networks, and mobile/wireless networking capabilities, which can be observed by the proliferation of M-Health applications that perform both clinical and non-clinical functions. Since the proliferation of mobile networks, telemedicine has attracted a lot more interest from both academic researchers and industry (Tachakra, Istepanian, Wang, & Song, 2003). This has resulted in many mobile/wireless telemedicine applications being developed and implemented (Budinger, 2003; Istepanian & Laxminaryan, 2000; Jovanov, Lords, Raskovic, Cox, Adhami, & Andrasik, 2003; Pattichis et al., 2002; Istepanian & Lacal, 2003; Webb, 2004). Critical healthcare information regularly travels with patients and clinicians, and therefore, the need for information to become securely and accurately available over mobile telecommunication networks is key to reliable patient care and reliable medical systems.
Health organizations are required by the Health Insurance Portability and Accountability Act of 1996 (HIPAA) to maintain the privacy of protected health information and to provide individuals with notice of its legal duties and privacy policies with respect to this information (HIPPA, 2005). Specifically, the law requires the following:
• Any medical information that identifies a person must be kept private.
• Notice of legal duties and privacy practices with respect to protected health information must be made available.
• The organization must abide by the terms of its notices currently in effect.
HIPAA also requires:
• Computers and data containing protected health information (PHI) must be protected from compromise or loss.
• Audit trails of access to PHI must be kept.
• Electronic transmissions of PHI must be authenticated and protected from observation or change.
Failure to comply with these requirements (for both HIPAA privacy and security) can result in civil and criminal penalties ranging from fines of $100 to $250,000 and up to 10 years in prison. Medical information always has been considered sensitive and never more so than now due to the security issues created by mobility. Many countries have imposed strict regulations with heavy penalties in order to ensure the confidentiality and authorized distribution of personal medical information. Following the lead of European Union Directive 95/46/EC that protects both medical and financial personal information, the United States and Canada passed important legislation (HIPAA and PIPED, respectively) that imposes substantial penalties, both civil and criminal, for negligent or intentional exposure of personal medical information to unauthorized parties.
The telecommunication industry has progressed significantly over the last decade. There has been significant innovation in digital mobile technologies. The mobile telecommunication industry has advances through three generations of systems and is currently on the verge of designing the fourth generation of systems (Olla, 2005b). The recent developments in digital mobile technologies are reflected in the fast-growing commercial domain of mobile telemedical services (Istepanian et al., 2006). Specific examples include mobile ECG transmissions, video images and teleradiology, wireless ambulance services to predict emergency and stroke morbidity, and other integrated mobile telemedical monitoring systems (Istepanian, Jovanov, & Zhang, 2004; Future trends: Convergence is all, 2005; Warren, 2003). There is no doubt that mobile networks can introduce additional security concerns to the healthcare sector.
Implementing a mobile trust model will ensure that a mobile transaction safely navigates multiple technologies and devices without compromising the data or the healthcare systems. M-Health transactions can be made secure by adopting practices that extend beyond the security of the wireless network used and by implementing a trusted model for secure end-to-end mobile transactions. The mobile trust model proposed by Wickramasinghe and Misra (2005) utilizes both technology and adequate operational practices in order to achieve a secure end-to-end mobile transaction. The first level highlights the application of technologies in order to secure elements of a mobile transaction. The next level of the model shows the operational policies and procedures needed in order to complement technologies used. No additional activity is proposed for the mobile network infrastructure, since this element is not within the control of the provider or the hospital.
The next section will discuss the mobile network technologies and infrastructure, which is a key component of any M-Health system. The network infrastructure acts as a channel for data transmission and is subject to the same vulnerabilities, such as sniffing, as in the case of fixed network transaction. The mobile networks discussed in the next section are creating the growth and increased adoption of M-Health applications in the healthcare sector.
mobile healthcare delivery system networks
The implementation of an M-Health application in the healthcare environment leads to the creation of a Mobile Healthcare Delivery System (MHDS), which can be defined as the carrying out of healthcare-related activities using mobile devices such as a wireless tablet computer, Personal Digital Assistant (PDA), or a wireless-enabled computer. An activity occurs when authorized healthcare personnel access the clinical or administrative systems of a healthcare institution using a mobile device (Wickramasinghe & Misra, 2005). The transaction is said to be complete when medical personnel decide to access medical records (patient or administrative) via a mobile network either to browse or to update the record.
Over the past decade, there has been an increase in the use of new mobile technologies in healthcare, such as Bluetooth and Wireless Local Area Networks (WLAN) that use protocols different than the standard digital mobile technologies such as 2G, 2.5, and 3G. A summary of these technologies is presented next, and a precis of the speeds and range is presented in Table 1.
These mobile networks are being deployed in order to allow physicians and nurses easy access to patient records while on rounds, to add observations to the central databases, to check on medications, as well as to perform a growing number of other functions. The ease of access that wireless networks offer is matched by the security and privacy challenges presented by the networks. This serious issue requires further investigation and research in order to identify the real threats for the various types of networks in the healthcare domain.
second Generation systems (2G /2.5G)
The second-generation cellular systems (2G) were the first to apply digital transmission technologies such as Time Division Multiple Access (TDMA) for voice and data communication. The data transfer rate was on the order of tens of kbits/s. Other examples of technologies in 2G systems include Frequency Division Multiple Access (FDMA) and Code Division Multiple Access (CDMA).
The 2G networks deliver high quality and secure mobile voice and basic data services, such as fax and text messaging, along with full roaming capabilities around the world. Second-generation technology is in use by more than 10% of the world’s population, and it is estimated that 1.3 billion customers in more than 200 countries and territories around the world use this technology (GSM_Home, 2005). The later advanced technological applications are called 2.5G technologies and include networks such as General Packet Radio Service (GPRS) and Enhanced Data rates for GSM Evolution (EDGE). GPRS-enabled networks provide functionality such as always-on, higher capacity, Internet-based content and packet-based data services enabling services such as color Internet browsing, e-mail on the move, visual communications, multimedia messages and location-based services. Another complimentary 2.5G service is EDGE, which offers similar capabilities to the GPRS network.
Table 1. Comparison of mobile networks based on range and speed
|
Networks |
Speed |
Range and Coverage |
Main Issues for M-Health |
|
2nd Generation GSM |
9.6 kilobits per second (KBPS) |
World wide coverage, dependent on network operators roaming agreements. |
Bandwidth limitation, Interference. |
|
High Speed Circuit Switched Data (HSCSD) |
Between 28.8 KBPS and 57.6 KBPS. |
Not global, only supported by service providers network. |
Not widely available, scarcity of devices. |
|
General Packet Radio Service (GPRS) |
171.2 KBPS |
Not global, only supported by service providers network. |
Not widely available. |
|
EDGE |
384 KBPS |
Not global, only supported by service providers network. |
Not widely available, scarcity of devices |
|
UMTS |
144 KBPS-2 MBPS depending on mobility |
When fully implemented should offer interoperability between networks, global coverage. |
Device battery life, operational costs. |
|
Wireless Local Area |
54 MBPS |
30-50 m indoors and 100-500 m outdoors. Must be in the vicinity of hot spot. |
Privacy, security. |
|
Personal Area Networks-Bluetooth |
400 KBPS symmetrically 150-700 KBPS asymmetrically |
10-100m |
Privacy, security, low bandwidth. |
|
Personal Area Networks-Zigbee |
20 kb/s-250 KBPS depending on band |
30m |
Security, privacy, low bandwidth. |
|
WiMAX |
Up to 70MBPS |
Approx. 40m from base station. |
Currently no devices and networks cards. |
|
RFID |
100 KBPS |
1 m Non line-of-sight and contact less transfer of data between a tag and Reader. |
Security, privacy. |
|
Satellite Networks |
400 to 512 KBPS new satellites have potential of 155MBPS. |
Global coverage. |
Data costs, shortage of devices with roaming capabilities. Bandwidth limitations. |
Third-Generation systems (3G)
The most promising period is the advent of 3G networks, which also are referred to as the Universal Mobile Telecommunications Systems (UMTS). A significant feature of 3G technology is its ability to unify existing cellular standards, such as code-division multiple-access (CDMA), global system for mobile communications (GSM_Home, 2005), and time-division multiple-access (TDMA), under one umbrella (Istepanian, Jovanov, & Zhang, 2004). More than 85% of the world’s network operators have chosen 3G as the underlying technology platform to deliver their third-generation services (GSM-Information, 2004). Efforts are underway to integrate the many diverse mobile environments and to blur the distinction between the fixed and mobile networks. The continual rollout of advanced wireless communication and mobile network technologies will be the major driving force for future developments in M-Health systems (Istepanian, Jovanov, & Zhang, 2004). Currently, the GSM version of 3G alone saw the addition of more than 13.5 million users, representing an annual growth rate of more than 500% in 2004. As of December 2004, 60 operators in 30 countries were offering 3GSM services. The global 3GSM customer base is approaching 20 million and already has been launched commercially in Africa, the Americas, Asia Pacific, Europe, and the Middle East (GSM_Home, 2005), thus making this technology ideal for developing affordable global M-Health systems.
Fourth Generation (4G)
The benefits of the fourth-generation network technology (Istepanian et al., 2006; Olla, 2005a; Qiu, Zhu, & Zhang, 2002) include voice-data integration, support for mobile and fixed networking, and enhanced services through the use of simple networks with intelligent terminal devices. 4G also incorporates a flexible method of payment for network connectivity that will support a large number of network operators in a highly competitive environment. Over the last decade, the Internet has been dominated by non-real-time, person-to-machine communications (UMTS-Forum-Report14, 2002). The current developments in progress will incorporate real-time, person-to-person communications, including high-quality voice and video telecommunications along with extensive use of machine-to-machine interactions in order to simplify and to enhance the user experience.
Currently, the Internet is used solely to interconnect computer networks. IP compatibility is being added to many types of devices such as set-top boxes to automotive and home electronics.
The large-scale deployment of IP-based networks will reduce the acquisition costs of the associated devices. The future vision is to integrate mobile voice communications and Internet technologies, bringing the control and multiplicity of Internet application services to mobile users (Olla, 2005b). 4G advances will provide both mobile patients and citizens with the choices that will fit their lifestyle and make it easier for them to interactively get the medical attention and advice they need when and where it is required and how they want it, regardless of any geographical barriers or mobility constraints.
Worldwide Interoperability for Microwave Access (WiMAX)
WiMAX is considered to be the next generation of Wireless Fidelity (WiFi /Wireless networking technology that will connect you to the Internet at faster speeds and from much longer ranges than current wireless technology allows (http:// wimcxxed.com/). WiMax has been undergoing testing and is expected to launch commercially by 2007. Research firm Allied Business Research predicts that by 2009, sales of WiMax accessories will top $1 billion (Kendall & Christopher, 2005), and Strategy Analytics predicts a market of more than 20 million WiMAX subscriber terminals and base stations per year by 2009 (ABI Research, 2005).
The technology holds a lot of potential for M-Health applications and has the capabilities to provide data rates up to 70 mbps over distances up to 50 km. The benefits to both developing and developed nations are immense. There has been a gradual increase in the popularity of this technology. Intel recently announced plans to mass produce and release processors aimed to power WiMax-enabled devices (WiMax, 2005). Other technology organizations that are investing in the further advancement of this technology include Qwest, British Telecom, Siemens, and Texas Instruments. They aim to get the prices of the devices powered by WiMax to affordable levels so that the public can adopt them in large numbers, making it the next global wireless standard. There are already Internet Service Providers in metropolitan areas that are offering pre-WiMAX services to enterprises in a number of cities, including New York, Boston, and Los Angeles (WiMax, 2005).
Wireless Local Area Networks
Wireless Local Area Networks (WLAN) use radio or infrared waves and spread spectrum technology in order to enable communication between devices in a limited area. WLAN allows users to access a data network at high speeds of up to 54 Mb/s, as long as users are located within a relatively short range (typically 30-50m indoors and 100-500m outdoors) of a WLAN base station (or antenna. Devices may roam freely within the coverage areas created by wireless access points, the receivers, and transmitters connected to the enterprise network. WLANs are a good solution for healthcare today; in addition, they are significantly less expensive to operate than wireless WAN solutions such as 3G (Daou-Systems, 2001).
Personal Area Networks
A wireless personal area network (WPAN) (Personal area network, n.d.; Istepanian, Jovanov, & Zhang, 2004) is the interconnection of information technology devices within the range of an individual person, typically within a range of 10 meters. For example, a person traveling with a laptop, a personal digital assistant (PDA), and a portable printer could interconnect wirelessly all the devices using some form of wireless technology. WPANs are defined by IEEE standard 802.15 (IEEE 802.15 Working Group for WPAN, n.d.). The most relevant enabling technologies for M-Health systems are Bluetooth (n.d.) and ZigBee Alliance (n.d.). ZigBee is a set of high-level communication protocols designed to use small, low-power digital radios based on the IEEE 802.15.4 standard for wireless personal area networks. ZigBee is aimed at applications with low data rates and low power consumption. ZigBee’s current focus is to define a general-purpose, inexpensive, self-organizing network that can be shared by industrial controls, medical devices, smoke and intruder alarms, building automation, and home automation. The network is designed to use very small amounts of power so that individual devices might run for a year or two with a single alkaline battery, which is ideal for use in small medical devices and sensors. The Bluetooth specification was first developed by Ericsson and later formalized by the Bluetooth Special Interest Group established by Sony, Ericsson, IBM, Intel, Toshiba, and Nokia and later joined by many other companies. A Bluetooth WPAN is also called a piconet and is composed of up to eight active devices in a master-slave relationship. A piconet typically has a range of 10 meters, although ranges of up to 100 meters can be reached under ideal circumstances. Implementations with Bluetooth versions 1.1 and 1.2 reach speeds of 723.1 kbit/s. Version 2.0 implementations feature Bluetooth Enhanced Data Rate (EDR) and thus reach 2.1 Mbit/s (Bluetooth, n.d.; Wikipedia, n.d.).
Radio Frequency Identification (RFID)
RFID systems consist of two key elements: a tag and a reader/writer unit capable of transferring data to and from the tag. An antenna linked to each element allows power to be transferred between the reader/writer and a remotely sited tag through inductive coupling. Since this is a bi-directional process, modulation of the tag antenna will be reflected back to the reader’s /writer’s antenna, allowing data to be transferred in both directions. Some of the advantages of RFID that make this technology appealing to the healthcare sector are as follows:
• No line of sight required between tag and reader.
• Non-contact transfer of data between tag and reader.
• Tags are passive, which means no power source is required for the tag component.
• Data transfer range of up to one meter is possible.
• Rapid data transfer rates of up to 100 Kbits/ sec.
The use of RFID in the healthcare environment is set to rise and is currently being used for drug tracking. RFID technology is expected to decrease counterfeit medicines and to make obtaining drugs all the more difficult for addicts (Weil, 2005). There are also applications that allow tagging of patients, beds, and expensive hospital equipment.
Satellite Technologies
Satellite broadband uses a satellite to connect customers to the Internet. Two-way satellite broadband uses a satellite link both to send and to receive data. Typical download speeds are 400 to 512 kbps, while upload speeds on two-way services are typically 64 to 128 kbps. Various organizations (Inmarsat announces availability of the 64 kbit/s mobile office in the sky, 2000) have been investigating the development of an ultra-high-data-rate Internet test satellite for making a high-speed Internet society a reality (JAXA, 2005). Satellite-based telemedicine service will allow real-time transmission of electronic medical records and medical information anywhere on earth. This will make it possible for doctors to diagnose emergency patients even from remote areas and also will increase the chances of saving lives by receiving early information, as ambulance data rates of 155 mbps are expected. One considerable drawback associated with using this technology is cost (Olla, 2004).
This section has summarized the various mobile network technologies that are being used in the healthcare sector. The mobile technologies described have a significant impact on the ability to deploy M-Healthcare application and systems; however, there are combinations of other important factors described in the next section. The next section will present a five-layered model that uses mobile network technologies along with device type, data display, application purpose, and application domain to categorize M-Health systems.
THE M-HEALTH REFERENCE MODEL
The financial cost of delivering quality healthcare is increasing exponentially not only in North America but also around the world. To satisfy increasing healthcare challenges, organizations in the healthcare sector are investing innovative technological solutions in order to meet the higher expectations placed on practice management (Wickramasinghe & Misra, 2005; Wickramasinghe & Silvers, 2002). The evolution of M-Health solutions, such as the use of wireless networks to access patient records and other healthcare services such as billing and prescription, are becoming popular, especially in the U.S. and Canada (Goldberg & Wickramasinghe, 2002) and in many European countries (Sorby, 2002). However, these wireless solutions also bring with them their own challenges, with security being one of the most important issues in M-Health. This is because M-Health systems transmit highly sensitive information such as patient data over cyberspace, and there is a need for high-level, end-to-end security, confidentiality, and privacy.
This section presents a reference model to describe each M-Health system in order to address the security challenges. Specifically, we present a reference model and show how our model can facilitate a higher level of end-to-end security in a wireless or mobile healthcare environment. Despite the advancements of wireless technologies, the use of wireless security in healthcare is in its infancy, and a robust mobile healthcare model needs to be developed in order to allow further innovation of M-Health applications and services that will fulfill the growing needs of the healthcare sector.
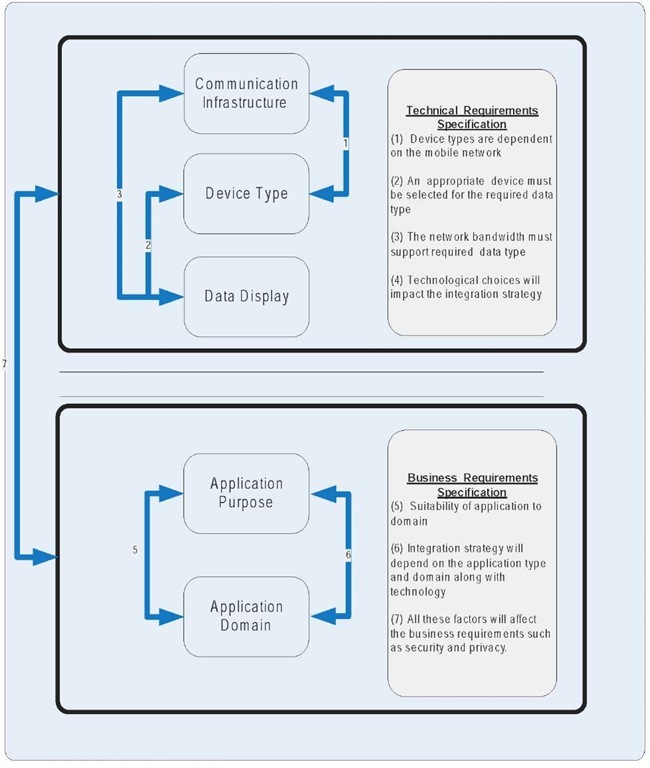
This section presents a reference model that can be utilized to classify M-Health systems by identifying the system components for a specific M-Health system. As previously indicated, the approach used to develop the reference model concentrated on identifying different dimensions of a Mobile Healthcare Delivery System (MHDS), which provides the capability to identify user security requirements for different categories in an organized manner. The reference model was formulated by reviewing the literature, and the model reflects an amalgamation of various classification schemes proposed by previous experts to categorize telemedicine and telehealth systems. The following subsections will provide a description of these five domains for the M-Health reference model illustrated in Figure 1. These domains include communication infrastructure, device type, data display, application purpose, and application domain.
Mobile communication Infrastructure
The first dimension defines the mobile infrastructure used to transmit, encode, and receive data. There are numerous wireless infrastructures available from which healthcare providers can choose. Examples of networks that provide personal area networks include Bluetooth and Zigbee. Mobile networks that provide connectivity within buildings include Wireless Local Area Networks (WLAN), which use different protocols from the standard digital mobile technologies such as 2G, 2.5, and 3G, which provide wide area connectivity. A summary of these technologies was provided in “Mobile Healthcare Delivery System Networks.”
Device Type
The second section is referred to as Device Type. Due to the advances in medical sensor technologies and handheld computers, M-Health has the potential to deliver services beyond the scope of mobile telemedicine discussed in the previous section. The integration of medical sensors with ICT allows physicians to diagnose, monitor, and treat patients remotely without compromising standards of care. Advances of new materials and signal processing research is allowing the design of smart medical sensors that utilize real-time data recording and processing of multi-physiological signals.
There is a multiplicity of sensors that are available commercially, such as piezo-electrical materials for pressure measurements, infrared sensors for body temperature estimation, and optoelectronic sensors that monitor heart rate and blood pressure. These sensors are being embedded into wearable items and accessories such as sunglasses and rings that can be carried easily. With the continual improvements to the sensors and the miniaturization of computing devices, these wearable devices for monitoring, diagnosing, and treating illnesses are becoming more readily available. Hitachi has developed a wristwatch that can measure the wearer’s health conditions such as pulse, moves, and body temperature. The monitoring wristwatch can send data wirelessly via the Internet to remote monitoring services. Hitachi aims to launch the wireless wristwatch commercially within three years (Hitachi’s wireless health monitoring wristwatch, 2005), targeting the healthcare service industry for elderly people. The benefit of wearable sensors for physiological data collection is that they can be used to monitor human health constantly without unsettling the patient’s day-to-day activities. Examples include rings, vests, watches, wearable intelligent sensors, and systems for e-medicine (Winters, Wang, & Winters, 2003). Wireless communication such as WAN is used for transmitting information and accessing healthcare databases wherever appropriate in order to allow free movement of the user (Jovanov et al., 2005).
Figure 1. M-health reference model for identifying components of healthcare delivery systems
Personal Digital Assistants (PDAs) have been popular among healthcare practitioners in the last few years. PDA penetration among physicians is at 25%, much higher than the 4% penetration for the general population (Fischer et al., 2003; Holmes, Brown, & Twist, 2001; Harris-Interactive, 2001; Parmanto et al., 2005). Studies have shown that the integration of PDAs into clinical practice has led to decreased medication error rates (Grasso et al., 2002) and the improvement in physicians’ adherences to clinical practice guidelines (Shiff-man, 1999, 2000).
Although the PDA has great potential to support evidence-based medicine, there are some considerable drawbacks (Parmanto et al., 2005). The small screen is a poor match for information resources designed for full-sized desktop computers. Presenting vast amounts of information in the limited space of the PDA display is a significant technical barrier to the realization of the PDA’s potential (Fischer et al., 2003; Larkin, 2001; Peterson, 2002). Other technical PDA drawbacks include low resolution, limited memory, slow processor, and problematic data input. An alternative for the PDA is a tablet PC. These are being adopted in the healthcare sector for information capture at the patient’s bedside.
Data Display
This key dimension describes how the information from the M-Health application is to be processed and transmitted. The chosen delivery options can have an important effect on the final quality of the telemedicine event and the outcome. Delivery options in telemedicine can be categorized under two main groups, according to Tulu and Chatterjee (2005): (1) synchronous and (2) asynchronous. Information transactions that occur between two or more participants simultaneously are called synchronous communications. In asynchronous communications, these transactions occur at different points in time. The data displays for both synchronous and asynchronous presentations can be grouped into the following categories: text, data, video, and multimedia (combination).
Application Purpose
The fourth dimension is the Application Purpose. This domain describes the intended use of the application. Field (1996) categorized this field into two main groups: clinical and non-clinical systems.
In 1996, the Committee on Evaluating Clinical Applications of Telemedicine (1996) grouped clinical applications into five categories:
1. Initial urgent evaluation
2. Supervision of primary care
3. Provision of specialty care
4. Consultation
5. Monitoring
Due to rapid advances in the M-Health field, three additional categories were added by Tulu and Chatterjee (2005):
6. Use of remote information and decision analysis resources to support or guide care for specific patients
7. Diagnostic
8. Treatment (surgical and non-surgical)
In addition to these groups, two additional categories have been added by the authors in order to reflect future trends of M-Health systems:
9. Drug delivery
10. Patient identification
The use of M-Health systems for non-clinical purposes includes medical education and administrative duties that do not involve decisions about care for particular patients. Some examples of M-Health non-clinical applications include:
1. Mobile access to the latest drug reference database
2. Bedside access to patient records (increase efficiency by reducing demand for paper records)
3. ePrescribing (mobile prescription writing and verification of drug interactions)
4. Prescription formulary reference (electronically identify most economic pharmaceuticals for a patient)
5. Electronic billing for in-home healthcare workers
6. Patient/drug verification (scan patient and drug bar codes to help to ensure that the appropriate medicine is being administered to the correct patient)
7. Delivery applications (healthcare supply delivery, tracking, and billing)
8. Patient encounter data capture
Application Area
The final dimension is called Application Area. This dimension describes the medical field implementing the M-Health technology. The application area also can be subdivided into clinical and non-clinical use. Clinical use relates to medical departments such as emergency, ophthalmology, pediatrics, and surgery. Non-clinical use relates to maintenance areas such as, charge capture, billing, and administration. The importance of this domain is to highlight the differences in the environments and to identify procedures that are specific to a particular healthcare domain.
In summary, the reference model highlights some of the important elements of an M-Health system. It is important to understand all of the dimensions of the reference model for each mobile healthcare system. Using the previous dimensions to describe an application will allow an M-Health system to be broken down into meaningful components.
The next section presents a case that features the use of an M-health application that uses a PDA to collect private medical data in remote African communities. The case in the next section illustrates how the reference model can be used to derive the components of an M-Health system, which allows issues such as security, privacy, hosting requirements, interference of devices, and integration to be investigated simultaneously.
OVERVIEW OF BLOOD DONOR
recruitment (bdr) project
As an increased number of healthcare industry professionals adopt mobile-enabled handheld devices to collect, store, and retrieve critical medical information, the need for security has become a top-priority IT challenge. These mobile benefits come with immense corporate and regulatory risk. PDA devices left unsecured while electronic health information is being hotsynced to a PC can become a primary source for the intentional malicious interception of confidential information. Furthermore, the recent adoption of the Patient Privacy and Federal Health Insurance Portability and Accountability Act (HIPPA) is a strong reason not to have protected health information on any unsecured devices, especially a PDA. This section will provide an example of how the reference model described in the previous sections can be used to describe a project initiated by the Red Cross.
The medical informatics data analyst/IT manager of the Uganda Red Cross Society identified a potential weakness in the use of mobile devices in the community health field. One of the authors was consulted to assist in developing a model that addressed data security in order to ensure the main IT security goals: confidentiality, integrity, and availability. Mobile devices were used in Blood Donor Recruitment (BDR) activities to register blood donors’ details. The medical history was stored for blood screening purposes. The data are very confidential because some of the blood donors’ results are positive for HIV, hepatitis, or syphilis. The system specifications are as follows:
Palm M125 with the following software:
• Palm Desktop software for Windows v. 4.0
• Pendragon form 3.2
• Pendragon Distribution Toolkit 2.0
• Windows XP on the PC
• Microsoft Access 2000
• The volume of data is about 10mb records on the PDA
This information is transferred to the computer server either by wired synchronization (HotSynced) or by wireless network. The hotsync option requires the user to be in the confines ofthe hospital or office, because it involves the use of the wired cradle. The other alternative that is being considered is the use of a wireless network such as WiFi or GSM to transfer data to the computer. Once the data are stored on the computer, they are manipulated with various software tools.
Using the M-Health reference model described in the previous section, the BDR system was broken down into the various components, as highlighted in Tables 2a and 2b. The following general recommendations were suggested to the client.
1. Upgrade memory on mobile device.
2. Formulate an enforceable end-to-end security policy.
3. Evaluate encryption software that can run both on the PDA and on the PC
4. Implement a solution that ensures that captured data on the PDA can be encrypted before being hotsynced on the PC.
5. Try out software prior to purchase.
There are various software solutions that can be used in order to secure the health system described previously. These solutions vary by encryption method, price, and device compatibility; however, there is no single solution to securing a system. It is important that each scenario be addressed differently, irrespective of how similar they seem.
A software solution that would fulfill the requirements for the scenarios described in Tables 2a and 2b, the PDASecure™by Trust Digital software, provides six different selectable encryption algorithms. Additional protection features include strong password protection to prevent unauthorized synchronizing or beaming of data, unauthorized deletion of files due to viruses or malicious code, and user authentication to devices before data can be decrypted. IT administrators can control who can access data and networks with wireless handheld devices, encrypt 100% of the data, and password-protect devices so that they are useless if stolen or compromised.
Using mobile networks allows data to travel over the open air. When data transmission is wireless, there is a possibility of interception of the radio transmission as well as unauthorized access to the hospital system. Poorly designed WiFi local area networks can be leaky and accessible beyond the intended boundary of use. If an unauthorized access of any kind occurs, it not only could lead to the loss of a patient’s privacy but also could lead to other potential consequences.
In Table 2a, the wireless network is not used, and the mobile device must be colocated with the computer system and server in order to transfer and copy data. This option also presents a different set of security problems. Due to the storage capacities of the mobile devices and the growing trend of today’s mobile workforce, every port, external disk drive, or JumpDrive can become a security risk. In the corporate environment, IT experts have turned to soldering and gluing USB ports in order to prevent intrusion; they also have installed titanium chastity belts around computers. USB ports and PDA cradles can be used for a variety of functions from input devices as inconspicuous as iPODs, which now are capable of downloading more than 30 gigabits of data.
In summary, using the reference model presented in this article to decompose a Red Cross blood donor system ensured that the security issues were identified and appropriately addressed. The model also was valuable for discovering technical specifications of the system and for understanding what upgrades were required in order to reduce the vulnerabilities of the system. In the future, this model can be improved by the creation of a set of guidelines and standards that are appropriate for a particular type of M-Health system. This will be valuable for governments and private vendors that implement innovative healthcare systems. The model also aids the healthcare stakeholders to identify the technological infrastructure, business requirements, and operational needs for the different types of M-Health systems.
Table 2a. Using the reference model to describe the blood donor system using a cradle solution
|
System |
Purpose |
Data |
Network |
Device |
Application Area |
|
Blood Donor Roprdiimoni (BDR) |
Blood donor data capture and transfer |
Textual data |
Fixed cable |
Palm PDA |
Rural community health |
|
Security Model • Data sent from the PDA and to the PDA must be secured with encryption. • User and server authentication must be in place. • Access to data in the server from a computer or PDA different from where the server runs must be secured with encryption and user / server authentication. • Advances authentication methods such as biometrics will provide added security features. |
|||||
Table 2b. Using the reference model to describe the blood donor system using a wireless solution
|
System |
Purpose |
Data |
Network |
Device |
Application Area |
|
Blood Donor Recruitment (BDR) |
Blood donor data capture and transfer |
Textual data |
WIFI/ GPRS |
Palm PDA |
Rural community health |
|
Security Model • Data sent to/from the PDA must be secured with encryption. • User and server authentication must be in place. • No data storage in network operator environment (GPRS/UMTS Operator) • WiFi network must be secured. |
|||||
conclusion
In the clinical domain, considerable leaps in the fields of biomedical telemetry, nanotechnology, ICT, and drug delivery techniques will encourage M-Health applications to evolve rapidly over the next decade. These new M-Health applications will take advantage of technological advances, such as device miniaturizations, device convergence, high-speed mobile networks, reduction in power consumption, and improved medical sensors. This will lead to the increased diffusion of clinical M-Health systems, which will impact the reshaping of the healthcare sector.
The non-clinical use of M-Health enterprise systems also will see an increased rate of adoption due to the potential benefits of the mobile solutions. Potential quality improvements may be achieved by implementing platforms that contain functionality that allows organizations to perform clinical results viewing, e-Prescribing, medication administration, specimen collection, charge capture, and physician dictation capture. These systems help to reduce errors by making the patient’s medical record and appropriate medical knowledge available at the point of care and at the point of decision.
The reference model presented in this article aids in the breakdown of M-Health systems into the following five key dimensions:
(1) Communication Infrastructure — describes mobile telecommunication technologies and networks;
(2) Device Type — relates to the type of device being used, such as PDA, sensor, or tablet PC;
(3) Data Display — describes how data will be displayed to the user and transmitted, such as images, e-mail, or textual data; (4) Application Purpose — identification of the objective for the M-Health system; and (5) Application Domain — definition of the area in which the system will be implemented.
The reference model described in this article encapsulates the emerging M-Health field and is needed to assist in clarifying the rapid progress in this field. Currently, the M-Health field is disjointed, and it is often unclear what component constitutes an M-Health system. This is addressed by the reference model. Further work is needed in order to identify the appropriate standards and guidelines for implementing the various types of M-Health systems. This would benefit vendors and system implementers by allowing them to understand the various conditions that may apply to a system that uses a specific set of the M-Health reference model variables. The reference model also would benefit from further work that defines how the choice of dimensions can impact the business models and the security policy for the implementation of the system.