abstract
When dealing with human lives, the need to utilize and apply the latest technology to help in saving and maintaining patients’ lives is quite important and requires accurate, near-real-time data acquisition and evaluation. At the same time, the delivery of a patient’s medical data needs to be as fast and as secure as possible. One possible way to achieve this is to use a wireless framework based on radio-frequency identification (RFID). This framework can integrate wireless networks for fast data acquisition and transmission while maintaining the privacy issue. This topic discusses the development of an agent framework in which RFID can be used for patient data collection. The topic presents a framework for the knowledge acquisition of patient and doctor profiling in a hospital. The acquisition of profile data is assisted by a profiling agent that is responsible for processing the raw data obtained through RFID and a database of doctors and patients.
introduction
The use and deployment of radio-frequency identification (RFID) is a relatively new area and it has been shown to be a promising technology (Glover & Bhatt, 2006; Lahiri, 2005; Shepard, 2004). This technology has the capability to penetrate and add value to nearly every field, lowering costs while improving service to individuals and businesses. Although many organizations are developing and testing the deployment of RFIDs, the real value of RFID implementation is achieved in conjunction with the use of intelligent systems and intelligent agents. The real issue is how intelligent-agent technologies can be integrated with RFID to be used to achieve the best outcome in business and services areas.
In this research, a new method for integrating intelligent-agent technologies with RFIDs in managing patients’ healthcare data in a hospital environment is given. Knowledge acquisition and profiling of patients and doctors in a hospital are assisted by a profiling agent that is responsible for processing the raw data obtained through RFID data that are stored in a hospital database. There are several perspectives for profiling that could be used in a healthcare and hospital environment.
An intelligent agent can assist in profiling patients based on their illness and ongoing diagnostics as reported by the RFIDs. There are certain data and knowledge about each patient in the hospital. This knowledge could be the description of what the patient’s symptoms are, monitoring status, and why the patient was admitted to the hospital. Using this information, an evolving profile of each patient can be built.
This data and knowledge can assist in deciding what kind of care he or she requires, the effects of ongoing care, and how to best care for this patient using available resources (doctors, nurses, beds, etc.). The intelligent agent will build a profile of each patient. Along with a profile of each patient, a profile for each doctor can also be developed. Then the patient and doctor profiles can be correlated to find the best doctor to suit the patient.
The patient-doctor profiling can be useful in several situations:
• Providing personalized services to a particular patient, for example, by identifying the services that a patient requires and hence speeding his or her recovery progress in or even out of the hospital.
• Disambiguating a patient’s diagnostic based on the patient profile and matching this profile to the available doctor’s profile. This may help in matching doctors with the suitable specialization to a patient.
• Providing speedy, reliable reentry of patients into the hospital by having the patients allocated to visit the relevant doctors.
• Presenting information in a way suitable to the doctor’s needs, for example, presenting the information about the patients on a continuous basis for the doctors.
• Providing tailored and appropriate care to assist in cost reduction.
Personalization, user modeling, and profiling have been used for many e-commerce applications by IBM, ATG Dynamo, BroadVision, Amazon, and Garden. However, the use of such systems in hospital and personal care and profiling has not been reported. It should be noted that the definitions of personalization, user modeling, and profiling that these companies discuss are not quite the same as our intended meanings.
Many user models try to predict the user’s preference in a narrow and specific domain. This works well as long as that domain remains relatively static and as such the results may be limited.
One of the main aims of profiling and user modeling is to provide users with correct and timely responses for their needs. This entails an evolving profile to ensure that as the dynamics of the user and real world change, the profile and user model reflects these changes.
A patient’s visit to the hospital can simply be classified as a regular visit, an emergency visit, or an ad hoc appointment (on a need basis). In each of these situations, the needs of the patients are different. During a regular visit, the patient visits the hospital at a regular interval and usually a doctor is assigned to that patient. The patient’s profile can assist the patient in a situation where the assigned doctor suddenly becomes unavailable. In this situation, the profile of the patient can be matched with the available doctors with suitable specializations for the needs of the patient. The patient-doctor assignment here is a kind of timetabling problem as we know the profile of the patient and doctors as well as the available doctors. Timetabling of doctors is out of the scope of this research study.
However, in an emergency visit, there is no assigned doctor for such a patient. The doctor in the emergency section of the hospital will provide information about a patient after examination, and a patient profile then can be created. In this case, the intelligent agent can assist the patient by matching the profile of the patient with the doctors suitable for the needs of the patient. Also, the doctors can be contacted in a speedier manner as they are identified and their availability is known.
An appointment visit is very similar to a regular visit, but it may happen only once and therefore the advantages mentioned for regular patients apply here.
We will endeavor to describe several of these, but will expand on one particular potential use of RFIDs in managing patient health data. First some background on RFIDs will be presented in this topic including some definitions. We will discuss the environment that RFIDs operate in and their relationship to other available wireless technologies such as the IEEE (Institute of Electrical and Electronics Engineers) 802.11b, IEEE 802.11g, and so forth in order to fulfill their requirements effectively and efficiently.
This research is divided into five main sections. The following is based on the patient-doctor profiling and intelligent agents. Then the topic gives an RFID background that will provide a good description of RFIDs and their components. This section discusses several practical cases of RFID technology in and around hospitals. It lists three possible applicable cases assisting in managing patients’ medical data. Next we discuss the important issue of maintaining patients’ data security and integrity, and relate that to RFIDs. Finally, the conclusion and further research directions are given.
patient-doctor profiling
A profile represents the extent to which something exhibits various characteristics. These characteristics are used to develop a linear model based on the consensus of multiple sets of data, generally over some period of time. A patient or doctor profile is a collection of information about a person based on the characteristics of that person. This information can be used in a decision situation between the doctor, domain environment, and patient. The model can be used to provide meaningful information for useful and strategic actions. The profile can be static or dynamic. The static profile is kept in prefixed data fields where the period between data-field updates is long, such as months or years. The dynamic profile is constantly updated as per evaluation of the situation. The updates may be performed manually or automated. The automated user-profile building is especially important in real-time decision-making systems. Real-time systems are dynamic. These systems often contain data that are critical to the user’s decision-making process. Manually updated profiles are at the need and discursions of the relevant decision maker.
The profiling of patients and doctors is based on the patient-doctor information:
• The categories and subcategories of doctor specialization and categorization. These categories will assist in information processing and patient-doctor matching.
• Part of the patient’s profile is based on symptoms (past history problems, dietary restrictions, etc.) and can assist in the prediction of the patient’s needs specifically.
• The patient’s profile can be matched with the available doctor profiles to provide doctors with information about the arrival of patients as well as presentation of the patient’s profile to a suitable available doctor.
A value denoting the degree of association can be created from the above evaluation of the doctor-patient profile. The intelligent-agent based on the denoting degrees can identify (and allocate) an appropriate available doctor to the patient.
In the patient-doctor profiling, the intelligent agent will make distinctions in attribute values of the profiles and match the profiles with the highest value. It should be noted that the intelligent agent creates the patient and doctor profiles based on data obtained from the doctors and patient using the following:
• Explicit profiling based on the data entered by hospital staff about a patient.
• Implicit profiling by filling that gap for the missing data by acquiring knowledge about the patient from his or her past visit or other relevant databases if any, and then combining all these data to fill in the missing data. Using legacy data for complementing and updating the user profile seems to be a better choice than implicit profiling. This approach capitalizes on the user’s personal history (previous data from previous visits to the doctor or hospital).
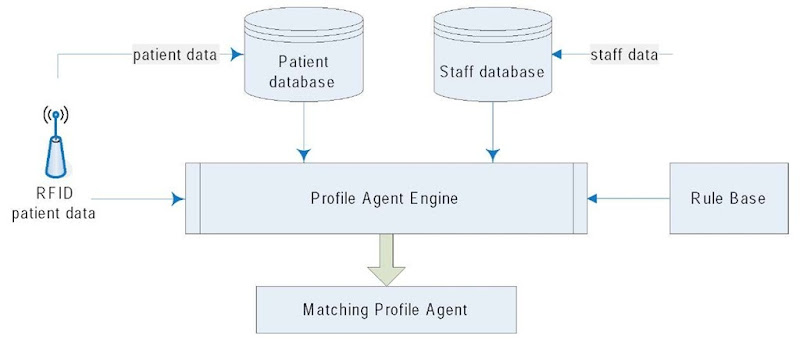
The proposed intelligent-agent system architecture allows user profiling and matching in such a time-intensive and important application. The architecture of the intelligent-agent profiling system using RFID is given in Figure 1.
INTEGRATION OF INTELLIGENT AGENTs, RFID TECHNOLOGIEs, AND PROFILE MATCHING
Intelligent agents have been used in order to provide the needed transformation of RIFD passive data collection into an active organizational knowledge assistant. An intelligent agent should be able to act on new data and already stored profile knowledge and thereafter examine its current actions based on certain assumptions. It then inferentially plans its activities. Furthermore, intelligent agents must be able to interact with other agents if required (Bigus & Bigus, 1998; Watson, 1997; Wooldridge & Jennings, 1995) and be able to substitute for a range of human activities in a situated context. In our case, the activities are medical patient assignment and the context is a hospital environment. The integration of RFID capabilities and intelligent-agent techniques provides promising development in the areas of performance improvements in RFID data collection, inference and knowledge acquisition, and profiling operations.
Profile matching is based on a vector of weighted attributes. To get this vector, a rule-based system can be used to match the patient’s attributes (stored in the patient’s profile) against a doctor’s attributes (stored in the doctor’s profile). If there is a partial or full match between them, then the doctor will be informed based on his or her availability from the hospital doctor database. The matching is done through the rule-based system by examining the attributes of the patient profile and matching them using the rules already created to the doctor’s profile based on the availability of doctors. Figure 1 displays the integration of intelligent agents, RFID technologies, and the profile-matching module.
Figure 1. Intelligent-agents profiling model using RFID
RFID Description
RFID is a progressive technology that has been said to be easy to use and is well suited for collaboration with intelligent agents. Basically, an RFID can be read only, volatile read and write, or write once and read many (WORM) times. RFIDs are non-contact and non-line-of-sight operations. Being non-contact and non-line-of-sight will make RFIDs able to function under a variety of environmental conditions while still providing a high level of data integrity (Glover & Bhatt, 2006; Lahiri, 2005; Shepard, 2004). A basic RFID system consists of four components. These are the RFID tag (sometimes referred to as the transponder), a coiled antenna, a radio-frequency transceiver, and some type of reader for the data collection.
The RFID tag (transponder) emits radio waves in ranges of anywhere from 2.54 centimeters to 33 meters. Depending upon the reader’s power output and the radio frequency used, and if a booster is added, that distance can be somewhat increased. When RFID tags pass through a specifically created electromagnetic zone, they detect the reader’s activation signal. Transponders can be online or off line and electronically programmed with unique information for a specific application or purpose. A reader decodes the data encoded on the tag’s integrated circuit and passes the data to a server for data storage or further processing.
RFID tags can be categorized as active, semi-active, or passive. Each has and is being used in a variety of inventory-management and data-collection applications today. The condition of the application, place, and use determines the required tag type.
Active RFID tags are powered by an internal battery and are typically read-write. Tag data can be rewritten and/or modified as the need dictates. An active tag’s memory size varies according to manufacturing specifications and application requirements; some tags operate with up to 5 megabytes of memory. For a typical read-write RFID work-in-process system, a tag might give a machine a set of instructions, and the machine would then report its performance to the tag. This encoded data would then become part of the tagged part’s history. The battery-supplied power of an active tag generally gives it a longer read range. The trade-off is greater size, greater cost, and a limited operational life that has been estimated to be a maximum of 10 years, depending upon operating temperatures and battery type.
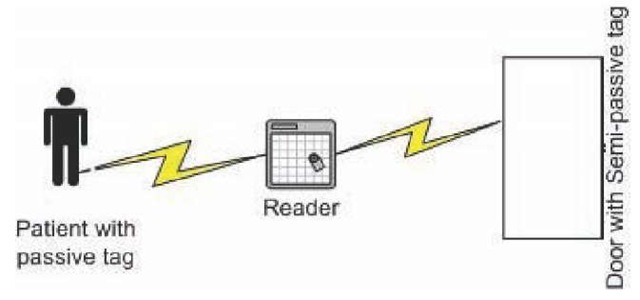
Figure 2. Semi-passive tag
The semi-active tag comes with a battery. The battery is used to power the tag’s circuitry and not to communicate with the reader. This makes the semi-active tag more independent than the passive tag, and it can operate in more adverse conditions. The semi-active tag also has a longer range and more capabilities than a passive tag. Linear bar codes that reference a database to get product specifications and pricing are also data devices that act in a very similar way. Semi-passive tags are preprogrammed, but can allow for slight modifications of their instructions via the reader or interrogator. However, they are bigger, weigh more, and are more complete than passive tags. A reader is still needed for data collection.
Passive RFID tags operate without a separate external power source and obtain operating power generated from the reader. Passive tags have no power source embedded in them and are consequently much lighter than active tags, less expensive, and offer a virtually unlimited operational lifetime. However, the trade-off is that they have shorter read ranges than active tags, and require a higher powered reader. Read-only tags are typically passive and are programmed with a unique set of data (usually 32 to 128 bits) that cannot be modified.
RFID systems can be distinguished by their deployment and frequency range. RFID tags generally operate in two different types of frequencies that make them adaptable for nearly any application. These frequency ranges are as follows.
Low-frequency (30 KHz to 500 KHz) systems have short reading ranges and lower system costs. They are most commonly used in security access, asset tracking, and animal-identification applications.
High-frequency (850 MHz to 950 MHz, or in industry, science, and medical applications, 2.4 GHz to 2.5 GHz) systems offer longer reading ranges (greater than 33 meters) and high reading speeds. These systems are generally used for such applications as railroad-car tracking, container dock and transport management, and automated toll collection. However, the higher performance of high-frequency RFID systems incurs higher system-operating costs.
The coiled antenna is used to emit radio signals to activate the tag and read or write data to it. Antennas are the conduits between the tag and the transceiver that controls the system’s data acquisition and communication. RFID antennas are available in many shapes and sizes. They can be built into a door frame, mounted on a tollbooth, or embedded into a manufactured item such as a shaver or software case so that the receiver tags the data from things passing through its zone. Often, the antenna is packaged with the transceiver and decoder to become a reader. The decoder device can be configured either as a handheld or a fixed-mounted device. In large, complex, often chaotic environments, portable or handheld transceivers would prove valuable.
RFID for Hospital Environment
In hospitals, systems need to use rules and domain knowledge that is appropriate to the situation. One of the more promising capabilities of intelligent agents is their ability to coordinate information between the various resources.
In a hospital environment, in order to manage patient medical data, there is a need for both types: fixed and handheld transceivers. Transceivers can be assembled in ceilings, walls, or door frames to collect and disseminate data. Hospitals have become large complex environments.
Nurses and physicians can retrieve the patient’s medical data stored in transponders (RFID tags) before they enter a ward or patient’s room.
Given the descriptions of the two types of RFID tags and their potential use in hospital patient data management, we suggest the following:
• It would be most useful to embed a passive RFID transponder into a patient’s hospital wristband.
• It would be most useful to embed a passive RFID transponder into a patient’s medical file.
• Doctors should have PDAs (personal digital assistants) equipped with RFID or some type of personal area network device. Either would enable them to retrieve some patient information whenever they are near the patient instead of waitieg until the medical data is pushed to them through the hospital server.
• Active RFID tags are more appropriate for the contmuous collection of patient medical data since the patient’s medical data need to be coetinuousiy recorded to an active RFID tag and an associated reader heeds ho be employed. Using an aeteve RFID means that the iag will be a bit bulky because od the needed aattery for the write process, and there is a concern about radio-frequency emissions. Thus, it is felt thai eh active tag would nolo °>e a good candidate for the patient wristband. However, if the patient’s condition is to be continuously monitored, the collection of the data at the source is essential. The inclusion of the tag in the wristband is the only way to record the medical datn on a rehl-tlme basis using the RFID technology. AOs more organizations get into the business of manueanturing RFIDs and the life and size of batteries decrease, the tag size will decrease and th°s maye ba a real possible us e.
• Passive RFID tags can be used as well. These passive tags can be embedded in the doctors PDA, which is needed for determining their locations whenever the medical staff requires them. Also, passive tags can be used in patients’ wristbands for storage of limited amount of data on an oOd-line basis, fof example, informatien such as the date of hospital admission, medical record number ( M RN),a ed sofort h.
Low-frequency-range tags are suitable for the patients’ wristband RFID tags since it is expected that the patients’ bed will not be too far from an RFID reader. The reahar might be fixed over the patifnt’s bed, in the bed itself, or over the door frame. The doctor using his or her PDA would be aiming to read the patient’s data directly and within a relatively short distance. High-frequency-range tags are suitablr for the physician’s tag implanted in the PDA. As physlcians move from one location tf another in the hospital’ data on their patients could be continuously being updated.
Finally, the transceivers and interrogators can differ quite considerably in anmplexity, de-penfing upen the type of tags being supported and tie application. ‘The ovfrall fonction of the applicaeion is to provide tFe means of com-municeting with the tags aid facilitating data transfer. Functions performed by the; reader may incur quite sophisticated signal conditioning and parity error checking and correction. Once the signal from a transponder has been correctly received and decoded, algorithms may be applied to decide whether the signal is a repeat transmission, and may then instruct the transponder to cease transmitting or temporarily cease asking for data from the transponder. This is known as the command-response protocol and is used to circumvent the problem of reading multiple tags over a short time frame. Using interrogators in this way is sometimes referred to as hands-down polling. An alternative, more secure but slower tag polling technique is called hands-up polling. This involves the transceiver looking for tags with specific identities, and interrogating them in turn. A further approach may use multiple transceivers multiplexed into one interrogator.
Figure 3. Patient and outpatient
Hospital patient data management deals with sensitive and critical information (patients’ medical data). Hands-down polling techniques in conjunction with multiple transceivers that are multiplexed with each other form a wireless network. The reason behind this choice is that there is a need for high-speed transfer of medical data from medical equipment to or from the RFID wristband tag to the nearest RFID reader and then through a wireless network or a network of RFID transceivers or LANs (local area networks) to the hospital server. From there it is a short distance to be transmitted to the doctor’s PDA, a laptop, or a desktop through a WLAN (wireless LAN) IEEE 802.11b or 803.11g, or a wired LAN, which operates at the 5.2 GHz band with a maximum data transfer rate of 54 Mbps.
The hand-down polling techniques, as previously described, provide the ability to detect all detectable RFID tags at once (i.e., in parallel), preventing any unwanted delay in transmitting medical data corresponding to each RF tagged patient.
Transponder programmers are the means by which data are delivered to WORM and read-write tags. Programming can be carried out off line or online. For some systems, re-programming may be carried out online, particularly if it is being used as an interactive portable data file within a production environment, for example. Data may need to be recorded during each process. Removing the transponder at the end of each process to read the previous process data and to program the new data would naturally increase process time and would detract substantially from the intended flexibility of the application. By combining the functions of a transceiver and a programmer, data may be appended or altered in the transponder as required without compromising the production line.
Practical cases using RFID Technology
This section explains in detail three possible applications of the RFID technology in three applicable cases. Each case is discussed step by step and then represented by a flowchart. These cases cover issues of the acquisition of a patient’s medical data, locating the nearest available doctor to the patient’s location, and how doctors stimulate the patient’s active RFID tag using their PDAs in order to acquire the medical data stored in it.
Case 1: Acquisition of Patient’s Medical Data
Case 1 will represent the method of acquisition and transmission of medical data. This process can be described in the following points as follows:
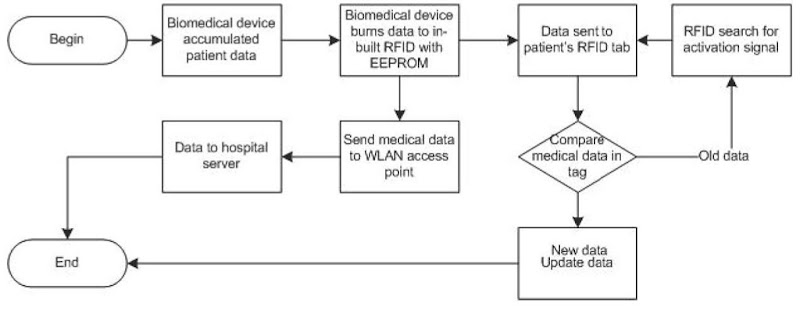
• A biomedical device equipped with an embedded RFID transceiver and programmer will detect and measure the biological state of a patient. This medical data can be an ECG (electrocardiogram), EEG (electroencephalogram), BP (blood pressure), sugar level, temperature, or any other biomedical reading.
• After the acquisition of the required medical data, the biomedical device will write this data to the RFID transceiver’s EEPROM (electronically erasable programmable read-only memory) using the built-in RFID programmer. Then the RFID transceiver with its antenna will be used to transmit the stored medical data in the EEPROM to the EEPROM in the patient’s transponder (tag) that is around his or her wrist. The data received will be updated periodically once new fresh readings are available by the biomedical device. Hence, the newly sent data by the RFID transceiver will be accumulated with the old data in the tag. The purpose of the data stored in the patient’s tag is to make it easy for the doctor to obtain medical information regarding the patient directly via the doctor’s PDA, tablet PC (personal computer), or laptop.
Figure 4. Acquisition of patient data
• Similarly, the biomedical device will also transfer the measured medical data wirelessly to the nearest WLAN access point. Since a high data-transfer rate is crucial in transferring medical data, IEEE 802.11b is recommended for the transmission purpose.
• The wirelessly sent data will then be routed to the hospital’s main server to be sent (pushed) to the following:
Other doctors available throughout the hospital so they can be notified of any newly received medical data. o An online patient-monitoring unit or a nurse’s workstation within the hospital.
An expert (intelligent) software system running on the hospital server to be then compared with other previously stored abnormal patterns of medical data and to raise an alarm if any abnormality is discovered.
• Another option could be using the embedded RFID transceiver in the biomedical device to send the acquired medical data wirelessly to the nearest RFID transceiver in the room. Then the data will travel simultaneously in a network of RFID transceivers until reaching the hospital server.
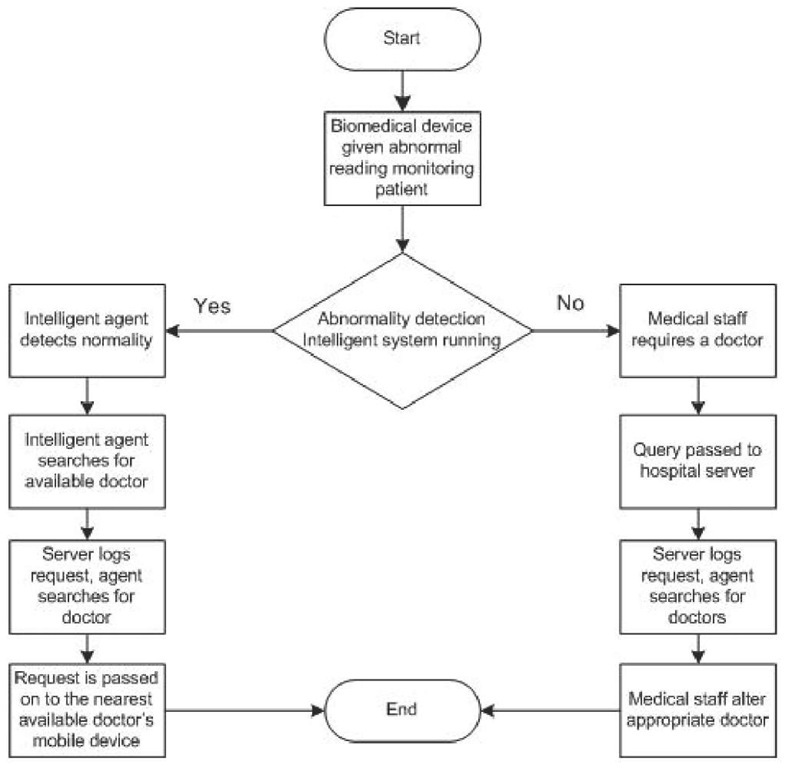
Case 2: Locating the Nearest Available Doctor to the Patient’s Location
This case will explain how to locate the nearest doctor, who is needed urgently, to attend an emergency medical situation. This case can be explained as follows:
• If a specific surgeon or physician is needed in a specific hospital department, the medical staff in the monitoring unit (e.g., nurses) can query the hospital server for the nearest available doctor to the patient’s location. In our framework, an intelligent agent can perform this task.
Figure 5. Locating nearest doctor
• The hospital server traces all doctors’ locations in the hospital through detecting the presence of their wireless mobile device, for example, PDA, tablet PC, or laptop in the WLAN range.
• Another method that the hospital’s server can use to locate the physicians is making use of the RFID transceivers built into the doctor’s wireless mobile device. Similar to the access points used in WLAN, RFID transceivers can assist in serving a similar role of locating a doctor’s location. This can be described in three steps.
The fixed RFID transceivers throughout the hospital will send a stimulation signal to detect other free RFID transceivers, which are in the doctors’ PDAs, tablets, laptops, and so forth. o All free RFID transceivers will receive the stimulation signal and respond back with an acknowledgement signal to the nearest fixed RFID transceiver. o Finally, each free RFID transceiver cell position would be determined by locating to which fixed RFID transceiver range it belongs to or currently is operating with.
• After the hospital server locates the positions of all available doctors, the RFID determines the nearest requested (condition evaluation) physican (pediatries, neuologist, etc…) to the patient’s location.
• Once the required physician is located, an alert message will be sent to his or her PDA, tablet PC, or laptop indicating the location to be reached immediately. This alert message would show the following.
Case profile over application period
The building, floor, and room of the patient (e.g., 3C109). o The patient’s case (e.g., heart stroke, arrhythmia, etc.). o A brief summary description of the patient’s case.
• If the hospital is running an intelligent agent on its server as described in our proposed framework, the process of locating and sending an alert message can be automated. This is done through comparing the collected medical data with previously stored abnormal patterns of medical data, then sending an automated message describing the situation. This system could be used in the patient-monitoring unit or the nurse’s workstation, who observe and then send an alert message manually.
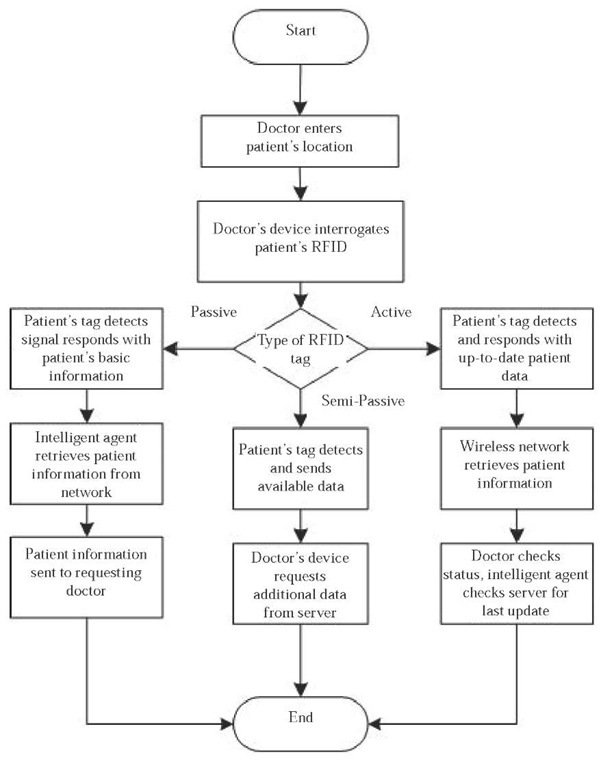
Case 3: Doctors Stimulate a Patient’s Active RFID Tag using Their PDAs in Order to Acquire the Medical Data Stored in It
This method can be used in order to get rid of medical files and records placed in front of the patient’s bed. Additionally, it could help in preventing medical errors (reading the wrong file for the wrong patient) and could be considered an important step toward a paperless hospital.
This case can be described in the following steps:
• The doctor enters the patient’s room or ward. The doctor wants to check the medical status of a certain patient. Instead of picking up the hard-copy paper medical file, the doctor interrogates the patient’s RFID wrist tag with his or her RFID transceiver equipped in a PDA, tablet PC, laptop, or so forth.
• The patient’s RFID wrist tag detects the signal of the doctor’s RFID transceiver coming from his or her wireless mobile device and replies back with the patient’s information and medical data.
• If there was more than one patient in the ward possessing RFID wrist tags, all tags can respond in parallel using hands-down polling techniques back to the doctor’s wireless mobile device.
• Another option could be that the doctor retrieves only the patient’s number from the passive RFID wrist tag. Then, through the WLAN, the doctor could access the patient’s medical record from the hospital’s main server.
RFID technology has many potential important applications in hospitals, and the three cases discussed are real practical examples. Two important issues can be concluded from this section. WLAN is preferred for data transfer given that IEEE’s wireless networks have much faster speed and greater coverage area as compared to RFID transceiver and transponder technology. Yet, RFID technology is the best for data storage and locating positions of medical staff and patients as well.
Here there is a need for the RFID transceiver and programmer to be embedded in biomedical devices for data acquisition and dissemination. A RFID transceiver embedded in a doctor’s wireless mobile device enables the doctor to obtain medical data. With the progress of the RFID technology, it could become a standard as other wireless technologies (Bluetooth, for example) and eventually manufacturers will be building them in electronic devices, or biomedical devices, in our case.
Maintaining Patients’ Data security and Integrity
Once data are transmitted wirelessly, security becomes a crucial issue. Unlike in wired transmission, wirelessly transmitted data can be easily sniffed out, leaving the transmitted data vulnerable to many types of attacks. For example, wireless data could be easily eavesdropped on using any mobile device equipped with a wireless card. In worst cases, wirelessly transmitted data could be intercepted and then possibly tampered with, or in best cases, the patient’s security and privacy F be compromised. Hence emerges the need for data to be initially encrypted from the source.
This section of the topic discusses how we could apply encryption to the designed wireless framework that was explained in the previous section, suggesting exactly where data need to be encrypted and\or decrypted depending on the case that is being examined.
Next, a definition of the type of encryption that would be used in the design of the security (encryption or decryption) framework will be discussed, and this will be followed by a flowchart demonstrating the framework in a step-by-step process. There are two layers of encryption that are recommended to be used.
• Physical: (hardware) layer encryption means encrypting all collected medical data at the source or hardware level before transmitting them. This ensures that the patient’s medical data would not be compromised once exposed to the outer world on its way to its destination. Even if a person with a malicious intent and also possessing a wireless mobile device steps into the coverage range of the hospitals’ WLAN, this intruder will gain actually nothing since all medical data are encrypted, making all intercepted data worthless.
• Application: (software) layer encryption means encrypting all collected medical data at the destination or application level once receiving it. Application-level encryption runs on the doctor’s wireless mobile device (e.g., PDA, tablet PC, or laptop) and on the hospital server. Once the medical data are received, they will be protected by a secret password (encryption or decryption key) created by the doctor who possesses this device. This type of encryption would prevent any person from accessing the patient’s medical data if the doctor’s wireless mobile device gets lost, or even if a hacker hacks into the hospital server via the Internet, intranet, or some other means.
Framework of Encrypting a Patient’s Medical Data
The previous section (practical cases using RFID technology) focused on how to design a wireless framework to reflect how a patient’s medical data can be managed efficiently and effectively leading to the elimination of errors, delays, and even paperwork. Similarly, this section will focus on the previously discussed framework from a security perspective, attempting to increase security and data integrity during the acquisition of a patient’s medical data and when doctors stimulate the patient’s active RFID tag using their wireless mobile devices in order to acquire the medical data stored in it. The third case on locating the nearest available doctor to the patient’s location is more concerned about locating doctors than transferring a patient’s data and it is not discussed here.
The lower part of Figure 6 represents the physical (hardware) encryption layer. This part is divided into two sides. The left side demonstrates the case of a doctor acquiring a patient’s medical data via a passive RFID tag located in a band around the patient’s wrist. The passive RFID tag contains only a very limited amount of information such as the patient’s name, date of admission to the hospital, and above all his or her MRN, which will grant access to the medical record containing the acquired medical data and other information regarding the patient’s medical condition. This process is implemented in six steps, and involves two pairs of encryption and decryption. The first encryption occurs after the doctor stimulates the RFID passive tag to acquire the patient’s MRN, so the tag will encrypt and reply back with the MRN to the doctors PDA, for example. Then the doctor will decrypt the MRN and use it to access the patient’s medical record from the hospital’s server. Finally, the hospital server will encrypt and reply back with the medical record, which will be decrypted once received by the doctor’s PDA.
The right side of Figure 6 represents a similar case, but this time using an active RFID tag. This process involves only one encryption and decryption. The encryption happens after the doctor stimulates the active RFID tag using a PDA that has an equipped RFID transceiver, so the tag replies with the medical data encrypted. Then the received data is decrypted through the doctor’s PDA. The upper part of Figure 6 represents the application encryption layer requiring the doctor to enter a password to decrypt and then access the stored medical data. So, whenever the doctor wants to access a patient’s medical data, he or she simply enters a certain password to get access to either the wireless mobile device or a hospital server, depending on where the medical data actually resides.
Figure 6. Functional flow
Securing medial data seems to be uncomplicated, yet the main danger of compromising such data comes from the people managing it, for example, doctors, nurses, and other medical staff. We have seen that even though the transmitted medical data are initially encrypted from the source, doctors have to run application-level encryption on their wireless mobile devices in order to protect the important data if the device gets lost, left behind, stolen, and so forth. Nevertheless, there is a compromise. Increasing security through using multiple layers and increasing the length of encryption keys decreases the encryption-decryption speed and causes unwanted time delays, whether we are using application- or hardware-level encryption. As a result, this could delay medical data being sent to doctors or online monitoring units. Figure 6 represents the case of high and low levels of security in a flowchart applied to the previously discussed two cases.
We conclude that there are two possible levels of encryption: the software level (application layer) or hardware level (physical layer) depending on the level of security required. Both physical-layer and application-layer encryption are needed in maintaining collected medical data on hospital servers and doctors’ wireless mobile devices. Encrypting medical data makes the process of data transmission slower, while sending data unencrypted is faster. Here there is a need to compromise between speed and security. For medical data, it has to be sent as fast as possible to medical staff, yet the security issue has the priority.
conclusion
Managing patients’ data wirelessly (paperless) can prevent errors, enforce standards, make staff more efficient, simplify record keeping, and improve patient care. In this topic, both passive and active RFID tags were used in acquiring and storing medical data, and in linking to the hospital’s server via a wireless network. Moreover, three practical applicable RFID cases were discussed and it was explained how the RFID technology can be put in use in hospitals while at the same time maintaining the acquired patient data’s security and integrity.
This research in the wireless medical environment introduces some new ideas in conjunction with what is already available in the RFID technology and wireless networks. The aim here is to link both technologies with each other to achieve the research’s main goal, which is delivering patient medical data as fast and secure as possible to pave the way for future paperless hospitals.