QoS Configuration
The QoS policies for the HM should match the existing IPv4 policies. As previously mentioned, the HM model presents a challenge with respect to where the IPv6 packets are classified and marked. The IPv6 packets are encapsulated within ISATAP tunnels all the way from the host in the access layer to the core layer, and IPv6 QoS policies cannot see the packets inside the tunnel. The first point where the IPv6 packets can have policies applied is at the egress interfaces of the core layer switches. The configuration in
Table 6-6 IPv6 QoS – Class Map, Match ACL, and DSCP Setting
|
Application |
Access Group Name |
DSCP Setting |
|
FTP |
BULK-DATA |
AF11 |
|
Telnet |
TRANSACTIONAL-DATA |
AF21 |
|
SSH |
TRANSACTIONAL-DATA |
AF21 |
|
All others |
N/A |
0 (default) |
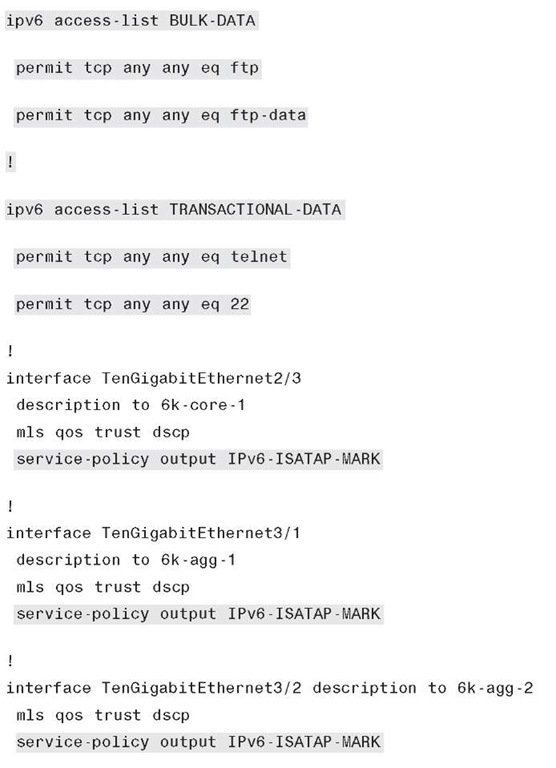
Example 6-38 is meant as a simple example only. In this policy, class maps are used to match against IPv6 access lists, as listed in Table 6-6.
The service policy is applied on egress (output) interfaces (upstream from the access layer). Upstream switches can trust these DSCP settings and also apply queuing and policing as appropriate (refer to the section "Implementing the Dual-Stack Model," earlier in this topic).
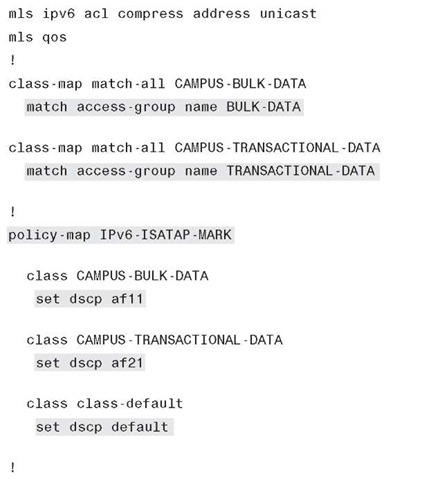
Example 6-38 shows the HM QoS example for 6k-core-1. The QoS policy is very basic and has two class-maps used to classify IPv6 applications: FTP, Telnet, and SSH traffic leaving (output) the 10-Gbps interfaces. Traffic that matches the policy will have a DSCP value set. These values are trusted upstream, and appropriate queuing and policing can be applied.
Example 6-38 Hybrid Model – QoS Example 6k-core-1
Infrastructure Security Configuration
You might want to further tighten IPv6 access control for ISATAP tunnels at the access layer. An access list can be applied to either a host port or an uplink/trunk port at the access layer. It is easier to manage the ACL at the uplink rather than configuring ACLs on each host port.
One access list that can be used is an ACL to permit tunnels from the hosts on the access switch to the ISATAP router address for that VLAN. For example, the following ACL permits the ISATAP tunnels (through protocol 41) only if the destination is 10.122.10.102 (the ISATAP router address previously configured). The ACL ends with a permit for all other IPv4 traffic (this is a dual-stack configuration so IPv4 must be permitted). Again, this ACL can be applied on a specific host port on input (ip access-group 100 in) or an uplink trunk or routed port (ip access-group 100 out).
![tmp19-130_thumb[2] tmp19-130_thumb[2]](http://what-when-how.com/wp-content/uploads/2011/09/tmp19130_thumb2_thumb.jpg)
