Client/server solutions comprise the foundation of most TCP/IP services ^^and applications. As you take a look at what client/server means to a network computer user, you see that TCP/IP is an excellent protocol choice for client/server computing because TCP/IP allows so many different computers and network devices to communicate as both clients and servers.
The client/server (C/S) distributed style of computing spreads computing from central data centers to desktops, laptops, handheld devices, and even cars regardless of where people are located.
Contrary to popular belief, software, not hardware, defines client/server. In the client/server game, a client application on one computer requests services from another computer running server software. The client and server software can run on any kind of hardware. Sometimes they even run on the same computer! You might even use a gigantic supercomputer running client software to request services from a tiny little PC by way of a network protocol, such as TCP/IP.
In this topic, we discuss client/server (C/S) basic concepts, including both server side and client side software.
Understanding the Server Side
Although we write that the client/server computing style is defined by software, you hear most people refer to computer hardware as clients and servers. In this section, we extend the definition to include more informal definitions of clients and servers. Even though the word client comes first in client/server, we need to start with the definition of the server.
Examining the server’s job
A server is software that provides a resource or a service to share with clients. In this topic, when we write about the technically correct definition of server, we use the term server software to avoid confusion with hardware.
When we write about servers, we’re using the term to mean computers that run server software. Servers may be specialized or multipurpose. A specialized server provides just one element, whereas a multipurpose server provides more than one. Another way to think about the difference is that multipurpose servers can be reached using several different TCP/IP protocols.
People often call the computer that’s running the software the server.
Identifying types of servers
Specialized servers include the ones in this list:
✓ Web server: Software that accepts requests from browser clients to deliver Web objects, such as home pages, documents, graphics, and applets. Also known as a web application server. Popular Web servers include Apache HTTP Server, Microsoft proprietary IIS (Internet Information Services, formerly named Internet Information Server), Google Web Server, and lighttpd.
✓ Commerce server: A type of Web application server that enables you to conduct business over the Web. The server software includes security features, such as TLS (Transport Layer Security), so that you can use your credit card without worrying. You still have to worry about your bills, though. Some people still refer to the security protections by the older name SSL (Secure Sockets Layer) even though TLS has replaced it.
✓ File server: A computer or group of linked computers (a cluster) that shares disk space. One advantage of having a file server is that the shared files still look like they’re on your own computer.
The computers that borrow the file server’s disk space are the clients. These clients may use an operating system that’s different from the server’s. When you have various operating systems, you have various file formats. The server’s job is to hide those format differences.
✓ Compute server: A computer that runs a program for you and sends the results back to you. For example, analyzing weather patterns requires enormous amounts of computer power. The meteorologists’ client workstations often aren’t capable of solving the complex mathematics involved, so they send the problem from their workstations to a supercomputer, which completes the calculations and sends back the results. That supercomputer is the compute server.
Using dedicated servers
Often you dedicate a server computer to one task only. For example, you don’t usually run a file server together with an e-commerce server. Reasons to use dedicated servers include
✓ Management: Different servers require different system administration tasks. For example, a file server might require a large disk farm and nightly backups, whereas a compute server, which needs only weekly backups, may require more fine-tuning and a more powerful CPU.
✓ Performance: Running different server programs on a single computer can slow down all the servers.
✓ Security: Some of the tasks involved in protecting the servers are quite different. For example, protecting an e-commerce server requires that you set up secure transactions and protect customer information.
On the other hand, you can have good reasons for running multiple servers on the same computer. For example, if your mail server is also running Web server software, you can read your mail with a Web browser in addition to the mail client you would normally use.
Understanding the Client Side
If you read the previous section about servers, you know that a client/server network relies on specialized central points — namely, servers — to provide services. Having all these services available unless something needs service, however, doesn’t make sense. That needy something is the client. A network contains many, many more clients than servers because a single server can satisfy hundreds (sometimes thousands) of client requests.
Defining a client
It’s this simple: A client is software that asks for and receives a resource or service from a server. Clients do all sorts of work — anything they want. We could write a whole topic on the types of clients that are out there.
People often call a computer that runs client software the client.
Clients, clients everywhere
For each server we describe in the previous section, you have a choice of many different clients. Consider these examples:
✓ Browser: Likely the most often used clients on the Internet, this client software receives services from a Web server.
✓ E-mail: If you and someone else in your household access the same e-mail server, one of you might use Microsoft Office Outlook for your e-mail client and the other might use Mozilla Thunderbird.
✓ Mobile: When companies want employees to be able to work anywhere, at any time, they make their mission-critical applications accessible by way of wireless handheld devices. The BlackBerry, smartphone, two-way pager, and personal digital assistant (PDA) are examples of mobile clients. Most contain a wireless internet browser, or WIB (also known as a mobile browser, microbrowser, or minibrowser), that knows how to use Wireless Application Protocol (WAP) to find information and display it on the small screen. These clients communicate over cellular networks or wireless LANs. The data is in Extensible Hypertext Markup Language (XHTML), Wireless Markup Language (WML), or even just the standard HyperText Markup Language (HTML), used for normal Web browsers. Many organizations also interconnect their e-mail and voice messaging systems with inbound and outbound fax services to create unified messaging solutions.
Answering the Question "Are You Being Served
Because of the software that any computer is (or isn’t) running, the computer can be
✓ Either a client or a server
✓ Both a client and a server
✓ Neither a client nor a server
The computer can also change as often as necessary to provide and access any number of services.
Figure 3-1 shows an example of multiple roles: One computer provides a shared printer and is thus a print server. The same computer is also a file server and accesses some files from another computer, which means that it’s also a client of a file server.
Figure 3-1:
A computer can be a client and a server at the same time.
Supporting TCP/IP with Client/Server and Vice Versa
Not only is TCP/IP a major enabler of client/server computing, it’s also one of the biggest users of it. The layered and modular design of TCP/IP makes it easy to design and implement new network services.
TCP/IP is a key element of many, but not all, client/server solutions. Other network protocols can be used on the network at the same time as TCP/IP.
TCP/IP is accepted as the protocol that links computers to not just each other but also all the different computers and servers in the world, from the smallest palmtop to the mightiest mainframe. TCP/IP makes all of them candidates for clients or servers.
Recognizing Other Internetworking Styles: Peer-to-Peer Computing
Although TCP/IP itself is built on a client/server architecture and enables most client/server computing, other internetworking architectures also run across TCP/IP networks. Peer-to-peer (P2P) is an older networking style that has become new again as the Internet has become accessible to much of the world’s population. Everything that’s old becomes new again.
Years ago, peer-to-peer networks were everywhere. They provided an easy way for a few cooperating users to share files and other computer resources. These users were considered a workgroup. In a peer-to-peer network, no computer is better than any other. A peer-to-peer network requires no dedicated servers.
Determining whether peer-to-peer Workgroups are still handy
Although small workgroups are convenient, peer-to-peer networking has its downsides:
✓ Decrease in speed: It slows down when too many users (more than 15) try to share.
✓ Unreliable resource access: Imagine that your colleague’s computer has a file that many people share. And then suppose that one day your colleague’s computer has a disk failure! The result: A critical file resource is lost to many users.
✓ Disintegration into a collection of separate computers: When resources in a workgroup are limited, the workgroup can disintegrate into a collection of separate computers. Suppose that members of your workgroup use so much of your computer’s shared disk space that no space remains for your files. You then have to decide whether to turn off disk sharing or disconnect the network cable.
P2P applications — P2P across the Internet
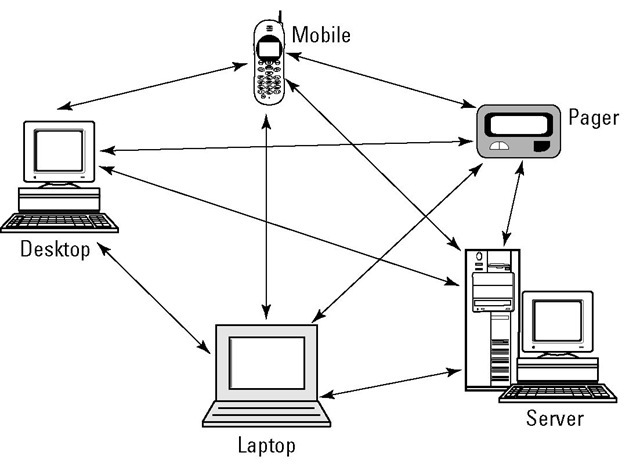
The earlier P2P section talks about the P2P computing style. P2P sharing applications have sprouted all over the Internet. Although these users don’t comprise a neatly formed private workgroup, they usually number in the millions. Figure 3-2 shows the architecture for a large, Internet-wide, P2P application.
Our teenage niece was once a big fan of P2P applications for sharing music. Little did she know that P2P software is subject to its fair share of worms and viruses.P2P programs can also bring lots of adware to your computer along with the videos and music you’re downloading. One of our computers became almost useless because of the amount of adware that made its way on there. The computer ground along slower than slow, and we almost cried from seeing all the pop-up ads, pop-under ads, and ads that were all over our screen. You would think we would know better. Unfortunately, when your teenage niece is using your computer, stuff happens.
Figure 3-2:
P2P application sharing across the Internet is unstructured.
Here’s a list of possible solutions, in case this situation happens to you:
✓ Make your teenager use the computers at the public library. They don’t let you download stuff.
✓ If you’re really nice, get your teen a computer of her own.
✓ Threaten all sorts of dire consequences if the computer gets clogged again — if that method works with your teenager.
Network administrators can use applications to manage network traffic, such as PacketHound from Palisade Systems, Inc., at www.palisadesystems. com, to block Gnutella (a popular file-sharing network) traffic from a network. Reasons to do this might include
✓ An effective but brute force way for an organization to protect against employees possibly violating copyright laws is to block all unauthorized P2P sharing.
✓ Overenthusiastic file sharers can clog an organization’s network bandwidth. Blocking P2P downloading activity relieves network stress.
Depending on the P2P program you use, security may be extremely lax or nonexistent.