In this topic, we look at TCP/IP as the protocol set for communication between two or more computers. Remember that TCP/IP is a large suite of components that work together. In this topic, we first describe the layered TCP/IP organization and then the protocols themselves.
TCP/IP technology is designed to allow all parts of your network to work together, regardless of which suppliers you bought them from. To make your network parts cooperate, TCP/IP divides network functions (for example, sending data or connecting different computer hardware) into layers and defines how those layers should interact.
Taking a Timeout for Hardware
There’s no point in having software if you have no hardware on which to run it. Although TCP/IP protocols are software, we need to discuss network connection media and Ethernet — the most widely used local-area network (LAN) technology on the Internet.
Starting with network connection media
Suppose that you want to connect all your networked devices — computers, printers, mobile phone, television, and game system — on your home network. Connection media and devices include much more than cables and wires. You can connect devices by using wireless access points, fiber optics, microwaves, infrared signals, and signals beamed to and from satellites.
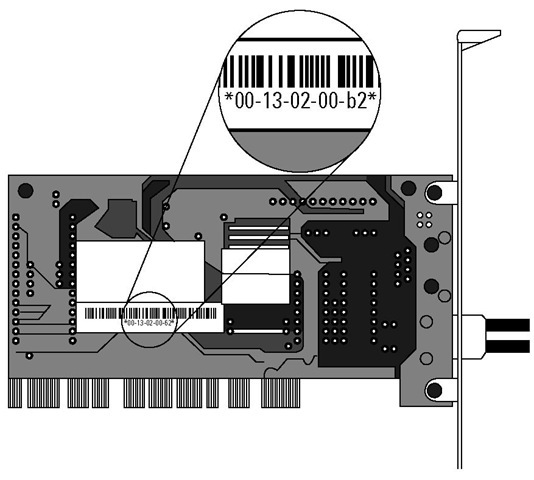
The most important connection device is the network interface card (or NIC, also known as a network adapter or a network card). This computer circuit board (or card, for short) lets your computer be connected to a network by cables or air. The NIC converts data into electrical signals. Most computers come with a NIC, either wireless or wired or both, already installed inside the case. The NIC’s manufacturer hardcodes on every NIC a unique hardware address known as the Media Access Control (MAC). Some protocols access this address. Figure 2-1 shows an example of a NIC with its MAC highlighted. Your card may look a little different, but all NICs function exactly the same.
Figure 2-1:
Every NIC has a unique MAC address.
Colliding with Ethernet
Ethernet is by far the most widely used LAN technology. (See the nearby sidebar, "How fast can Ethernet go?") Ethernet hardware ranges from fat, orange cables to plain old air. Ethernet allows any device on a network, from a giant corporate database server to the cash register in the local delicatessen, to send and receive packetized data.
How fast can Ethernet go?
The IEEE defines different kinds of Ethernet, depending on the connection media and the speed at which Ethernet moves the network data. In an Ethernet LAN, devices connect to the bus, not to each other. When the first edition of this topic was written, Ethernet transmitted 1 gigabit (1 billion bits) of data across the network per second. That’s equal to 125 megabytes. Fast, huh? Ethernet can now move data at 10 gigabits per second. If you do the math, you see lots of zeros. Wait — there’s more! An IEEE group working on faster Ethernet is developing standards for 40 gigabits per second and 100 gigabits per second.
Ethernet uses the Carrier Sense Multiple Access/Collision Detection (CSMA/ CD) technique. This very long name has a simple meaning: When a network device realizes that a packet collision has occurred, it knows when to wait and retry. With Ethernet, the data from the small deli’s cash register is just as important as anything that the headquarters’ big server has to send. All devices on the network are equal. You see in Figure 2-2 a basic LAN connected by Ethernet. Each device on the network, including the printer, has a NIC and TCP/IP software running.
Figure 2-2:
Ethernet watches for collisions in a very small LAN.
Stacking the TCP/IP Layers
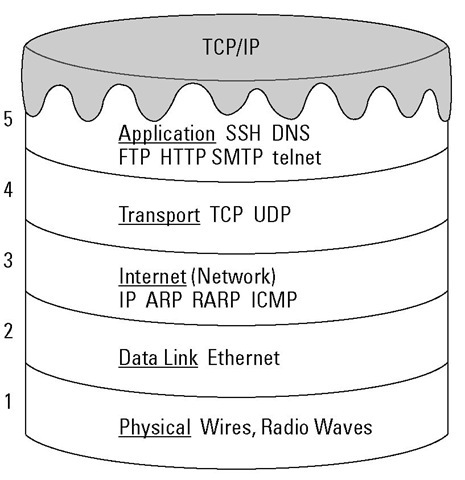
TCP/IP software organizes the protocols in layers so that five layers are stacked up in the TCP/IP model. We love desserts and snacks, so we like to describe TCP/IP as a five-layer cake. Figure 2-3 gives you an idea of how the layers are structured.
Figure 2-3:
Check out these "yummy" layers.
Technically, the five layers in the "cake" comprise a stack, and the protocols that sit in these layers comprise a protocol stack.
Each layer of the stack depends on the layers below it; that is, each layer services the layer above or below it. When two computers communicate, each computer has its own set of layers. When you send a message to another computer on the network, your information starts at the top layer of your computer, travels down all the layers to the bottom of the stack, and then jumps to the other computer. When your information arrives on the other computer, it starts at the bottom layer and moves up the stack to the application in the top layer.
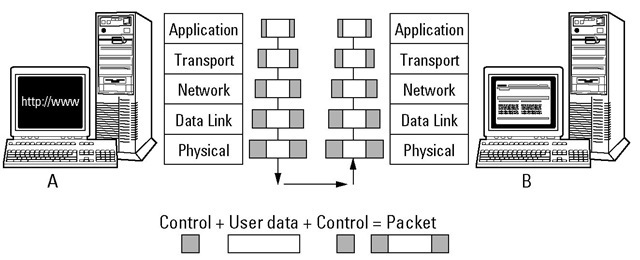
Each layer has a special function: The lower layers are hardware oriented, and the highest layer provides user services, such as e-mail, file transfers, and general network monitoring. Look at Figure 2-4 to see how data moves through these layers.
In the following sections, we examine each layer, starting with Layer 1, at the bottom of the cake.
How many TCP/IP stacks exist?
The answer is "only one, yet many." Or, "It depends." Only one set of standards exists for a TCP/IP stack. On the other hand, the protocols, services, and applications are software programs. Somebody has to write the programs to implement TCP/IP software. And — oh, boy! — are there ever a lot of somebodies. A TCP/IP stack usually is supplied with your computer. If you buy a computer that runs a version of Microsoft Windows, a team of Microsoft programmers most likely wrote the programs that make your computer’s stack run. If your computer is a Mac, Apple Computer programmers wrote the stack. It doesn’t matter who wrote the TCP/IP stack. What’s important is that the programs work the way they’re supposed to, according to the RFCs.
Most Linux and Unix operating systems (and there are so many) have built-in TCP/IP protocol stacks.
If you don’t like the way your stack is programmed, you can swap in another stack. Even better, you can download and swap in a free stack, or just part of a stack, from the Internet. If you search for the phrase free software TCP/ IP at www.google.com, you see a long list of TCP/IP programs.
Figure 2-4:
Data travels up and down through each layer.
Layer 1: The physical layer
The physical layer at the bottom of the stack is pure hardware, including the cable or satellite (or other) connection medium and the network interface card. This layer is where electrical signals move around (and we try not to think too hard about how it works). Protocols in the two bottom hardware layers aren’t part of the TCP/IP stack. The physical layer transforms data into bits that move across the network media. The protocols in the physical layer include protocols related to cables, or to air, in the case of wireless. The physical layer also has protocols for connection methods.
Layer 2: The data link layer
This layer is another one that we don’t want to strain our brains trying to figure out — again, hardware is involved. This layer splits data into packets to be sent across the connection medium, and then wiring, such as Ethernet or token ring, gets involved. The data link layer moves data up through the higher layers for transportation across networks and through tunnels to Virtual Private Networks (VPNs).
The data link layer also includes protocols that work with your Media Access Control (MAC) address and your network interface card (NIC).
A MAC address is a hardwired special address on your NIC. Every NIC has a unique MAC address.
For example, after the information is on the wire (or in the air, in the case of wireless), the data link layer handles any interference. If heavy sunspot activity occurs, the data link layer works hard to ensure that the interference doesn’t garble the electric signals.
Layer 3: The internet layer
The bottom two layers are hardware related, whereas TCP/IP is software. Layer 3 (sometimes called the network layer) is the first place where a TCP/ IP protocol fits into the networking equation: IP is this TCP/IP protocol. This layer receives packets from the data link layer (Layer 2) and sends them to the correct network address. If more than one possible route (or path) is available for the data to travel, the internet layer works out the best route. Without it, the data couldn’t reach the correct location. We explain the IP protocol, and others, in the later section "Internet layer protocols."
Layer 4: The transport layer
Although the internet layer routes your information to its destination, it can’t guarantee that the packets holding your data will arrive in the correct order or won’t pick up any errors during transmission. That’s one of the transport layer’s jobs. TCP works at the transport layer to ensure that the packets have no errors and that all packets arrive and are reassembled in the correct order. Without this layer, you couldn’t trust your network. UDP also works at the transport layer and shares one function with TCP: to move your data up to the next layer. However, sometimes network services would rather be fast than correct, so UDP does no error checking on your packets, saving transport time.
Layer 5: The application layer
The TCP/IP protocols that sit on Layer 5 receive packets from the lower protocols, de-packetize them back into their original form, and let the various TCP/IP applications and services manage the data according to the original user request, such as, "Please browse the Web." Layer 5
✓ Establishes and coordinates a session, which is a connection between two computers: Before two computers can transmit data between themselves, they must establish a session. The session announces that a transmission is about to occur and, at the end of it, determines whether the transmission was successful.
✓ Works with operating systems to convert files from one format to another, if the server and client use different formats: Without file format conversion, file transfers could happen only between computers that have the same file format.
✓ Sets up the environment so that applications can communicate with each other and with users: Requests for service and data start at the application layer and move down through the remaining four layers before going out across a network. The application layer is also where secure protocols for specific applications, such as Web browsing and e-mail, reside.
Chewing through Network Layers: A Packet’s Journey
TCP/IP slices your network message into packets (little bites) and sends them out to the network. When the packets arrive at their destination, TCP/IP reassembles them into your original message. We use the life span of a packet to explain the layers in the network model.
A packet’s life begins when an application creates it. Each packet then travels down the layers of the sending host (computer), across the network cables, up the layers of the destination host, and into the appropriate application.
As the packets travel down the layers of the sending host, headers containing control and formatting information and directions are added. When the packets reach the destination host, that information is read and stripped as the packets move upward through each layer. For example, if you FTP a file from Computer A to Computer B, the data in the file is packetized at the application layer and sent through all layers on Computer A. By the time the packets are sent out across the wire, they have gained some "weight" (all that added network information). After the roly-poly packets reach the destination host, they start to slim down; when they arrive at the top layer and deposit your file, they’re positively svelte again.
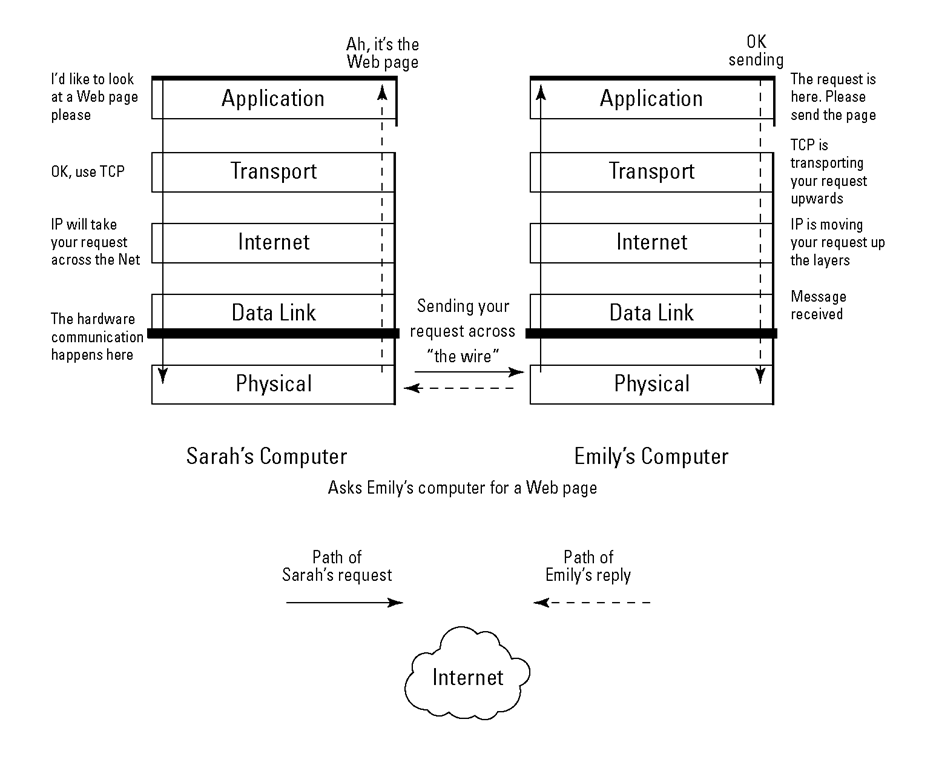
Figure 2-5 shows a Web browser request that uses the Hypertext Transfer Protocol (HTTP) to start at the application layer. The packet travels from the application layer on Computer A (Sarah’s computer) onto the network and then up to the application layer on Computer B (Emily’s computer). You can see how the packet gains weight at each of Computer A’s layers and then goes on a diet (so to speak) as it moves up through computer B’s layers. Yo-yo dieting may be unhealthy for humans, but it works well for packets on the network.
The TCP/IP stack (or suite) is a large collection of protocols, named after the two original pieces: TCP and IP. You may say, "A suite is too big. Can I just have the protocols I need?" Nope. (Sorry.) The protocols in the TCP/IP suite move the data from one layer to another and interact with each other. You can’t have a truly functional network by using just one of the TCP/IP protocols.
Figure 2-3, earlier in this topic, shows the TCP/IP five-layer "cake" with some protocols drawn on the individual layers. You don’t need every protocol on the stack to run a network application, but you need at least something from each layer in the stack. So, even though you may not use every protocol on each layer, you definitely need more than one.
Figure 2-5:
Packets eat TCP/IP layer "cake" on the network.
Now that you’ve gotten used to the idea that TCP/IP includes numerous protocols in its stack, you’re about to find out that TCP/IP is even more than the stack. TCP/IP also includes services and applications. The stack alone would be useless if there were no services and applications to take advantage of them. Most of these services and applications sit at the top layer of the TCP/ IP "cake," and Parts III and IV of this topic describe them in detail. The following section uses FTP as an example of a TCP/IP component that functions as protocol, service, and application.