MUICache
In addition to the UserAssist key values, there’s another way to see what software may have been run under a user account on the system. The MUICache key is located in the following path:
Unlike the UserAssist key, the values within the MUICache key do not have time and date data associated with them. In fact, the values in the MUICache key have descriptive comments associated with them. Although some of the values, such as those that start with "@," seem to be default entries for software that may already be installed on the system, others seem to be created when software is run on the system.
The muicache.pl RegRipper plugin extracts data from the MUICache key within the NTUSER.DAT hive file, and skips over the values that start with "@" and displays the remaining values as illustrated here:
As you can see, a variety of value names and data is visible. Again, little (i.e., no) documentation, particularly from the vendor, describes how values are added to this key, or any circumstances under which values may be removed from the key. However, it appears that for a value to be created in the MUICache key, the software program or application needs to be run on the system by the user; therefore, the contents of this key would give an analyst an indication of user activity, even if the user deleted the application, or (as indicated by the preceding plugin output) ran the application from separate media.
Diane Barrett of the University of Advancing Technology has done work in the area of virtualization artifacts; that is, looking for indications of the use of virtualization technologies that have been used on systems. In one particular presentation, Diane revealed that the use of visualization applications such as MokaFive (you can find additional information at www. mokafive.com/, as well as at http://en.wikipedia.org/wiki/Moka5) and MojoPac (www. mojopac.com/) can be seen in the MUICache key. In some cases, these types of applications may be used to keep the user’s activities private, in that the applications on the host are not used, and the applications (Web browser, etc.) are specifically configured or designed to not maintain a cache or history of activity. Interestingly, MojoPac reportedly maintains its own Registry, so in cases involving this virtualization environment, you’d want to look for a MojoPac device to acquire and analyze, as well. Also, keep in mind that other visualization environments, such as the free Portable Virtual Privacy Machine from MetroPipe (www. metropipe.net/pvpm.php), exist and may be in use.
MRU Lists
Many applications maintain an MRU list, which is a list of files that have been most recently accessed. Within the running application, these filenames generally appear at the bottom of the drop-down menu when you select File on the menu bar.
Perhaps the most well-known (and all-inclusive) MRU list Registry key is the RecentDocs key:
This key can contain quite a number of values, all of which are binary data types. We are interested in the values that have numbers as names, which contain the names of the files accessed (in Unicode), and the value named MRUListEx, which records the order in which the files were accessed (as DWORDs). For example, on my system, the first DWORD (i.e., 4-byte value) in the MRUListEx value data is 0×26, or 38 in decimal. The value with the name "38" points to a directory that I opened. Given that adding a value and its associated data to the key, as well as modifying the MRUListEx value, constituted modifying the key, the LastWrite time of the RecentDocs key will tell us when that file was accessed.
Again, to be clear, the values beneath the RecentDocs key (and its subkeys) have numbers as names; however, these names alone do not correspond to the order in which the files referenced in the data were last accessed. This information is maintained in the MRUListEx value data.
Tip::
In most cases, MRU keys contain some way of determining when the most recent activity took place. With the RecentDocs key, the MRUListEx value contains the ordered list of those activities. Other keys have different ways of maintaining this information, depending upon the specific key. However, the LastWrite time of the key corresponds to the time that the most recent activity occurred. For analysis purposes, this provides additional information that can be used to develop a timeline of activity on the system.
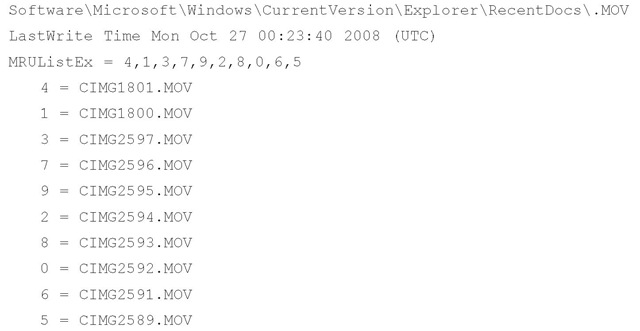
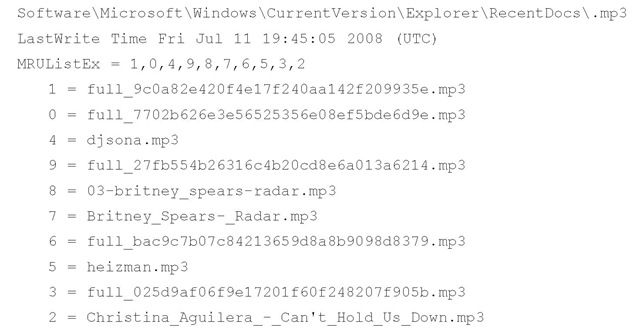
The RecentDocs key also has a number of subkeys, each one being the extension of a file that was opened (.doc, .txt, .html, etc.). The values within these subkeys are maintained in the same way as in the RecentDocs key: The value names are numbered, and their data contains the name of the file accessed as a binary data type (in Unicode). Another value called MRUListEx is also a binary data type and maintains the order in which the files were accessed, most recent first, as DWORDs. The recentdocs.pl plugin parses the RecentDocs key contents, as well as the contents of each subkey, and lists the values in MRUListEx order, as illustrated in the plugin output excerpt that follows:
As you can see, the plugin displays the RecentDocs subkey name, the LastWrite time for the key, the contents of the MRUListEx value (with the final, terminating 0xffffffff value removed), and then value names in MRUListEx order. From this example, we can see that the user viewed a MOV movie file Monday, October 27, and listened to a particular MP3 file Friday, July 11.
You can find another popular MRUList in the RunMRU key:
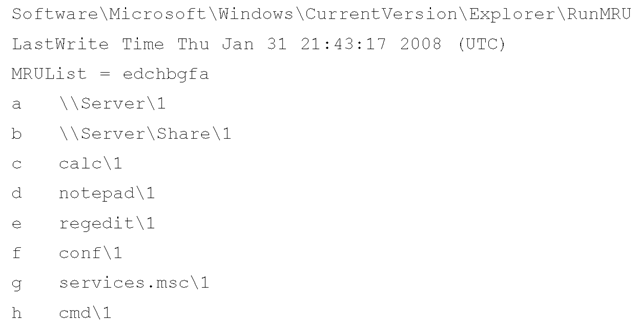
This key maintains a list of all the values typed into the Run box on the Start menu. Figure 4.19 illustrates what the contents of this key might look like.
Figure 4.19 Excerpt from RunMRU Key
The RunMRU MRUList value is maintained in clear text and is more easily readable than the RecentDocs MRUListEx value. As with the RecentDocs key, however, the most recently typed items are listed first within the MRUList value.
Entries are added to this key when a user clicks the Start button, chooses Run, and types a command, name of a file, or the like. The runmru.pl plugin displays the information within the RunMRU key as shown here:
The MRUList value within the RunMRU key tells us that the most recent item to be typed into the Run box is item "e", which, in this case, is "regedit". The RunMRU key value names, much like the values beneath the RecentDocs key, do not correspond to the order in which the various items were typed into the Run box; rather, the MRUList value maintains that information. In the preceding example, the "h" value (i.e., "cmd") was not the most recent item typed into the Run box; "regedit" was the most recent item the user typed into the Run box.
During investigations centered around user or employee activity, I have found entries in the RunMRU key that show accesses to remote systems (such as those listed in the preceding example), as well as to applications and files on removable storage media.
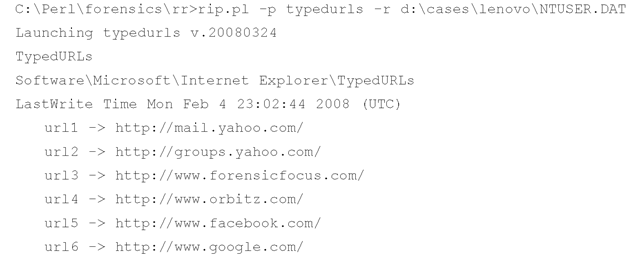
Another key similar to the RunMRU key is the TypedURLs key:
Similar to the RunMRU key, the TypedURLs key maintains a list of the URLs the user types into the Address bar in Internet Explorer. However, the value names within the TypedURLs key are ordered with the most recently typed URL having the lowest number; consequently, this key doesn’t have an MRUList or MRUListEx value. The typedurls.pl plugin displays the information from within this key as follows:
This information can be combined with Temporary Internet files to show which Web sites were visited by clicking a link and those that the user typed in by hand. You can find yet another location for MRU lists in the following key:
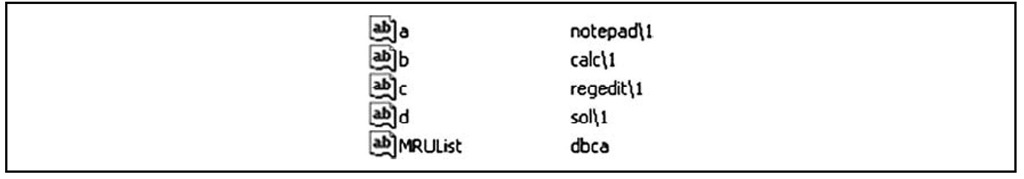
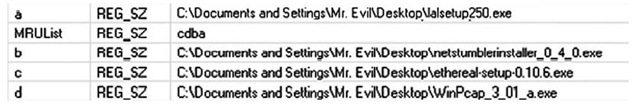
This key (a good reference is available at http://support.microsoft.com/kb/322948) maintains MRU lists of files opened via the Open and SaveAs dialogs within the Windows shell. Similar to the RecentDocs key, the OpenSaveMRU key also maintains subkeys of specific file extensions that have been opened or saved. Like the RunMRU key, however, the data within these keys consists of string data types and is easily read. The contents of this key can be very useful in several ways. First, some file extensions do not appear frequently during normal system use, so the subkey beneath the OpenSaveMRU key for that file extension may have only one entry, named a. In this case, the data for the MRUList value will have only a listed, as shown in Figure 4.20. The LastWrite time for the key will tell you when that file was opened or saved.
Figure 4.20 Excerpt from a Subkey of the OpenSaveMRU Key
Opening an image acquired from a Windows XP system in ProDiscover, I navigated to the OpenSaveMRU key for the user. The LastWrite time for the exe subkey is listed as August 17, 2004, at 11:18 a.m. Figure 4.21 illustrates the contents of the exe subkey.
Figure 4.21 Excerpt from the exe Subkey of the OpenSaveMRU Key (via ProDiscover)
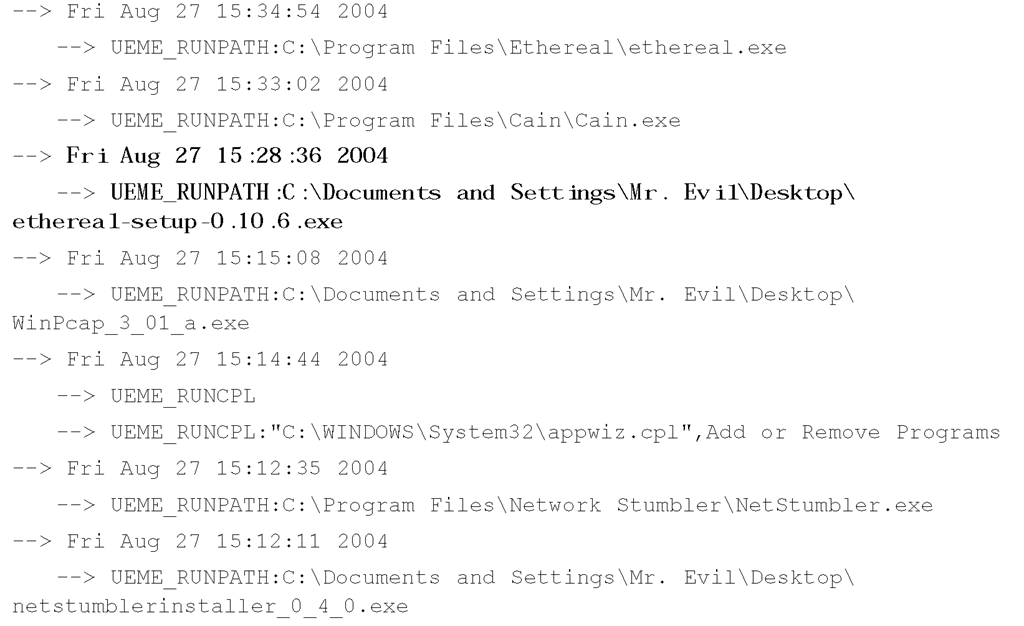
Figure 4.21 shows that the most recent file accessed was the Ethereal setup utility (Ethereal is a suite of network traffic capture and analysis tools, now called Wireshark), used to install the application. This information can then be correlated with the contents of the UserAssist key (using the uassist.pl ProScript, Version 0.11, 20060522). When the ProScript is run against a test image, we see the following:
As you can see, our user was quite busy on August 27, 2004. (The ProScript extracts raw FILETIME data and translates it into UTC time, which is roughly equivalent to GMT time. The ProDiscover application shows all times relative to the examiner’s system and TimeZoneInformation settings.) The TimeZoneInformation Registry key shows that when the system was running, it was set for the Central time zone, with automatic adjustments for daylight saving time enabled. The ActiveTimeBias is 300 minutes (five hours), and ActiveTimeBias on my system (with ProDiscover open) is 240 minutes (four hours). From this information, we see that about 10 minutes after saving the Ethereal setup application to his system the "suspect" installed that application.
Another way this information can be useful is to show the use of external storage devices. Not only will the LastWrite time of the subkey provide the date and time the device was connected to the system, but also the information can be correlated to the contents of the MountedDevices key to provide additional information about the device.
Yet another MRU list can be found beneath the following key:
The subkeys beneath this key correspond to extensions for files that have been opened on the system. Beneath the file extension subkeys, you will find subkeys called OpenWithProgIDs and OpenWithList. These Registry entries tell the system what application to use to open a file with that extension when the user double-clicks the file. This may be important during an examination as a user may have installed and then uninstalled an application that would open files with a particular extension. When the application is removed, information may still remain in the FileExts key. The fileexts.pl RegRipper plugin parses and displays this information.