ABSTRACT
Access to mobile data and messages is essential in healthcare environment as patients and healthcare providers are mobile. This is inline with the need of ubiquitous computing in everyday life. Mobile and wireless devices can assist in ensuring patient’s safety by providing easy availability of the data at the point of care. Portability and accessibility of these devices enhances use of them in healthcare environment. However, data integrity and confidentiality of information in them need to be ensured to provide safe, effective and efficient healthcare. Mobile healthcare involves conducting healthcare related activities through using mobile devices such as a smart phone,
Personal digital assistant (PDA), wireless enabled computer, iPod and so on. Mobile computing is suitable for healthcare as healthcare providers are mobile. These would be suitable for conducting patient’s healthcare activities in emergencies, ward rounds, homecare, chronic disease management, conducting clinical trials, and so on. There are various projects using mobile devices to enhance patient’s care. With the advancement of medical informatics, telemedicine and information technology, mobile data devices play an enormous role in healthcare system. In this topic, we outline the need of mobile devices in healthcare, usage of these devices, underlying technology and applications, importance of security of these devices, securing mobile data communication in healthcare through different security models and case examples of applications that we have developed, in particular (1) iPathology tool on iPod, (2) securing healthcare information using Pocket PC 2003, and (3) securing information on handheld devices. There were several incidents in the past due to the insecurity of mobile devices that can leak information to anyone who does not have access to the information. In this topic, we will illustrate several techniques that we have developed to protect these malicious activities and how these are applicable for securing mobile data computing in healthcare.
INTRODUCTION
In recent years, a wide range of handheld devices have been introduced in the market. Pocket size handheld organizers, called personal digital assistants (PDAs), have evolved from offering simple services such as calendar, address book, and e-mail, to working as a powerful mobile network client that can be used to access corporate databases and be used as part of an e-commerce platform. The healthcare industry is not an exception with healthcare providers using various handheld devices for accessing information and for telemedicine purposes. These days, the mobile devices are also equipped with communication abilities, such as GSM/GPRS ability, WiFi 802.11a/b/g Wireless LAN or Bluetooth. Handheld devices are perfect for carrying information, such as multimedia information, on the fly. Users can enjoy the information while they are on their way to work, etc.
Securing such devices includes providing protection for wireless communication, stored data and against viruses and malicious codes, together with making provisions for preventing theft of the device. The more we become dependent on handheld devices, the more threatening the attack will be. Today the U.S. military is already relying extensively on such devices. These devices can be used for GPS, viewing maps of areas, interacting with other troop units and as (remote) sensors (such as those used against bio-warfare), etc. Moreover, the U.S. military is spending large amounts of money to expand the capabilities of such devices. Other applications in critical infrastructures can be expected. For example, today many firefighters and ambulance services rely on paper maps. In regions in the world that expand rapidly, there is a significant advantage to switch to handheld devices where maps are updated more frequently. Since several manuals are primarily available via the Internet, handheld devices will be used by technicians to repair machinery in nuclear power plants, airplanes, etc.
There are several major differences between a desktop computer and a handheld device including limited input methods, small screen size, lower range processor, and limited memory for the handheld device. These differences affect the design of applications that run on these devices. Palm OS and Pocket PC handheld devices do not have a keyboard. Although a third party keyboard, such as Palm Portable keyboard or Targus Stowaway keyboard, can be used, most users enter text to the device with a stylus which is then recognised by a character recognition program such as Palm Graffiti or Microsoft Transcriber. Other methods of input include using the on-screen keyboard, or typing text on a desktop PC that is connected to the PDA. Communication with the device is achieved by using the HotSync/Activesync that synchronizes the data with its copy that is stored on a desktop computer, using a communication port such as the serial port, the IrDA (Infrared Data Association) port, or the USB port.
Palm 1000 was introduced by 3Com in 1996. Devices running Palm OS have dominated the handheld market and currently having around 70% of the market share (Hansmann, Merk, Nickous, & Stober, 2001). Palm OS is also adopted by companies such as HandSpring and IBM with applications ranging from Palm OS native applications including Address Book and Date Book, to other applications that are available as freeware, shareware or commercial products from third-party providers, including fax software, calculators, and software development kits for developers. The second major operating system for handheld computers is Windows CE (or pocket PC) which takes almost the rest of the market share. The most recent version is known as Windows Mobile 2005, with its support to GSM/ GPRS mobile phone connection, together with its ability to connect to Wireless LAN 802.11a/b/g and Bluetooth.
Our Contribution
In this topic, first we review the background on handheld devices, together with their known weaknesses. Then, we proceed with the use of handheld devices in healthcare environment. Finally, we provide some case studies that we have done in the effort to securing such devices.
Background of Handheld Devices
In this section, we review the necessary background and knowledge in handheld devices.
PALM OS PDA
Storage on a Palm PDA includes RAM and ROM that reside on memory cards. A memory card can store 256 MB and is divided into a dynamic heap and multiple storage heaps that are used for providing runtime environment, and storing data and applications. Newer models of Palm PDA, starting from Palm m505, m515, and Tungsten, are equipped with SD (Secure Digital) expansion slots that could be used for Bluetooth or Wireless LAN 802.11b devices.
Palm OS and built-in applications are stored in the ROM while user’s data and applications are stored in RAM which is always powered to allow persistent storage. Applications and users’ data can be backed-up on a desktop PC, or to the backup expansion pack (for the new models).
development systems
There are several development systems for building programs for Palm OS with C and C++ being the most commonly used languages for Palm Computing platform. Other available languages are Basic, Java, and Assembly.
A newly created application can be tested on a Palm OS Simulator or a Palm OS Emulator before it is installed on a Palm device. Palm OS Simulator is only available on the Macintosh OS and requires the application to be linked with a Simulator library that allows it to run as an independent application. Palm OS Emulators are available for Windows, Mac OS and Unix systems. The Emulator imitates the Palm OS device and allows an application to run without requiring additional library.
third Party Program Installation
There are a number of ways of downloading programs to a Palm PDA. Firstly, HotSync program can be used to download new applications during the synchronization between the Palm and a desktop PC. A second method uses a third party program such as Pilot Install (envi.com, online). Applications can also be downloaded using IrDA port or a Bluetooth connection. IrDA drivers for desktop PCs can send a file to another IrDA point and so an application can be sent to a Palm PDA. An application can also be attached to a mail. This requires connection to users’ mailbox on their PC via a synchronization program and so in terms of difficulty is similar to downloading the program via the HotSync program. Downloading a program is also possible through a browser (either on-line or off-line browser), such as AvantGo.
communication and Networking
Palm OS supports two types of data communication: serial/USB and infrared. The serial/USB communication is used to synchronize the Palm via a HotSync or be used to transmit or remove data through a serial bus. The Palm is equipped with an infrared transceiver and can beam data (such as contact details) to another Palm using appropriate communication protocols. This ability has been used to enable a Palm to remotely control another device or to print to an infrared printer.
A TCP/IP connection can be established when a Palm connects to the Internet via a modem or a cradle with a software that supports the PPP protocol. Palm OS provides two libraries for TCP/IP networks which are known as Palm OS Net Library and Internet Library.
Wireless Portal
Many handheld devices can only access Web pages that have specially formatted data to download. Webclipping and WAP are the two commonly used technologies that meet the limitations of small displays that are not capable of displaying regular multimedia Web sites. Although Web browsers such as ProxyWeb and PalmScape, are available for Palm, the two technologies above are usually preferred due to the size limitation of the device.
Palm.Net offers mobile Internet access for Palm device with ROM version 3.5 and above. This service is available in North America and allows users to connect to the Web through a connectivity gateway, operated by Palm.
windows ce devices
Windows CE was introduced in 1996 to provide a common operating system for a range of devices including handheld computers, industrial controllers, embedded appliances and wireless communication devices. Windows CE has the same API as Windows 2000 and allows the programmers to use a subset of Win32 API development tools and languages including Visual Basic and Visual C++ targeted for CE devices. There are also special versions of the compiler, known as the Embedded Visual C++ and Embedded Visual Basic, that makes it easier to create programs.
Windows CE is not an on the shelf OS. Rather, a device manufacturer needs to configure the Windows CE operating system for the processor platform of his/her choice. The operating system is usually built into the device’s ROM, although sometimes it is put in flash memory.
Windows CE devices support serial and USB communication for one-to-one communication, and network connection which can use one or many devices and more sophisticated protocols such as HTTP and file exchange protocols like remote access service (RAS). To support infrared communication based on IrDA protocol, the IrSock API has been added to the operating system.
The latest version of Windows CE is known as the Windows Mobile 2005 Operating System, which is equipped with GSM/GPRS mobile phone connection together with 802.11a/b/g Wireless LAN and Bluetooth support.
vulnerabilities of palm os devices
In the following, we illustrate the known vulnerabilities of handheld devices. Without losing generality, we only illustrate the vulnerabilities against Palm OS devices. Three types of attacks have been reported on Palm.
Eavesdropping Palm Infrared connection
The Palm OS Infrared is vulnerable to data stealing attack. Two main reported cases include constructing a program called “NotSync” which enables a Palm to steal the password from another Palm via its IrDA interface (@stake, online), and an eavesdropping attack (Nutheesing, online).
Denial of Service Attacks via HotSync
Palm HotSync manager is used to synchronize data between a Palm and a desktop PC. The HotSync program has a network mode that allows remote synchronization via a modem, hence adding more flexibility to Palm.
It is shown (Knight, online) that setting Hot-Sync in the Network mode can lead to a denial of service attack by sending a large amount of data followed by a new line which results in the Palm to crash.
Palm virus and trojan Horse
Similar to other operating systems, Palm OS is vulnerable to viruses and Trojan Horses. The first Palm OS virus, known as the “Liberty crack” (Harris, online), is written by one of the co-authors of the Liberty program. It is a destructive Palm application, disguised as a free version of the Liberty application, that deletes all of the programs stored on a Palm and then reboots the device. A more comprehensive survey of Palm OS weaknesses can be found elsewhere (Kingpin, 2001).
PROTECTION OF HANDHELD DEVICES VIA PERSONAL FIREWALL
We have created a personal firewall for Pocket PC 2003 handheld device. Our personal firewall will allow an authorized information to pass through the device, but an unauthorized information will not be able to enter the device. The technique that we used is by rewriting the Ethernet driver for Pocket PC 2003 device. We will illustrate our work in the following section.
Background
In such a pervasive connected environment, network security is critical to protect devices and the information they contain. Central to network security is the firewall, which acts as a barrier between an untrusted network and the trusted network (or device). Due to high-profile hacker attacks and proliferation of viruses, firewalls have become a fundamental security tool. At this stage, no security system can ensure with absolute certainty that all of the information will be protected all of the time. Firewalls are one of the most effective security tools that a network administrator can deploy to limit vulnerability.
A firewall is hardware or software that monitors the transmission of packets of digital information that attempt to pass through the perimeter of a network. A firewall can be described as a system for enforcing access control policy between two networks. A firewall can deny unauthenticated requests or requests with potential threats, while permitting authenticated requests, thus protecting the internal network. In most cases, firewalls are used to prevent outsiders from accessing an internal network. However, firewalls can also be used to guard one highly sensitive part of a private network against its other parts. Such sensitive parts are for payroll, payment processing, R&D systems, etc.
There are essentially three types of firewalls: (1) packet-filtering firewalls, (2) stateful firewalls, and (3) application-level firewalls. A packet-filtering firewall drops packets based on their source or destination address or ports. For example, it blocks all packets from a site that we do not trust, or blocks all packets to an internal machine that should be inaccessible from an external network. Linux’s ipfwadm and ipchains are examples of this type of firewall. A stateful firewall works at the session layer of the OSI model, or the TCP layer of TCP/IP. It monitors TCP handshaking between packets to determine whether a requested session is allowed. It creates a circuit then relays data between external and internal network. Stateful firewalls keep track of sessions and connections in internal state tables. It can protect against certain types of denial of service attacks. An example of this type of firewall is Checkpoint FW-1. In addition to lower levels, application-level firewalls inspect packets at the application level. A packet reaches the firewall and is passed to an application-specific proxy, which inspects the validity of the packet.
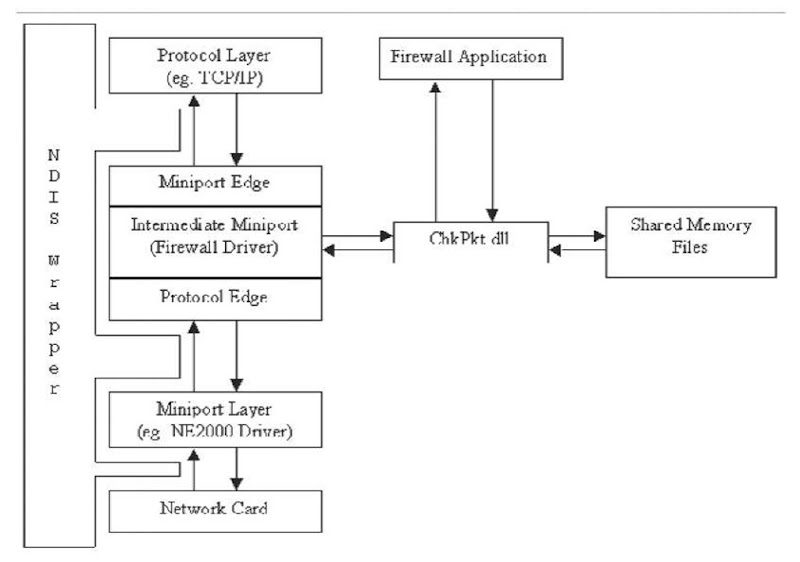
Figure 1. Relation between the modules
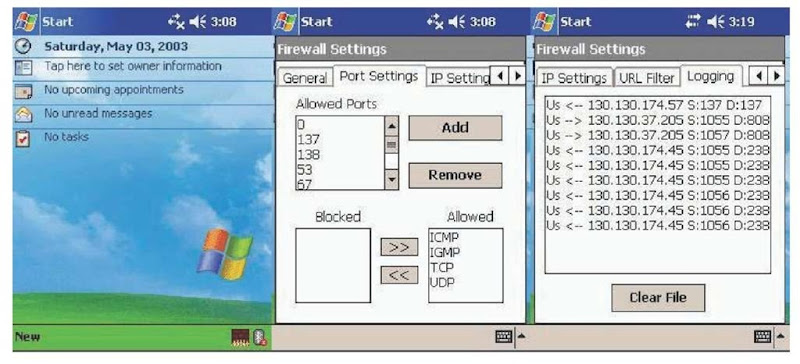
Figure 2. Screen captures of Personal Firewall for Pocket PC 2003 devices
Newer types of firewalls include distributed firewalls and personal firewalls. In distributed firewalls, security policy is centrally defined but is enforced at individual network end points, such as routers, gateways, servers or user PCs. Policy can be distributed to end points in various forms. For example, policy can be pushed to end points where such policy should be enforced. Policy may also be provided to the users as credentials that will be presented when needed.
Unlike traditional firewall sitting between the external and internal networks, a personal firewall runs on a user’s computers. Personal firewalls do not have problems such as end-to-end network encryption, malicious insider attacks, single point of failure, etc.
Personal firewall for Pocket Pc 2003 Handheld devices
We have designed and implemented a personal firewall for Pocket PC 2003, which filters TCP/IP traffic passing to and from the device via an Ethernet card. The concept can be extended to allow other protocols such as 802.11b to be covered. Although personal firewalls exist in the market (e.g., Norton Personal Firewall, etc.), their design and implementation are not widely available. In this topic, we present the first open source firewall for Pocket PC 2003 operating system devices. The personal firewall is a packet-filtering type firewall, which analyzes the contents of network packets. The firewall examines, if applicable:
1. Source and destination IP address
2. Source and destination port
3. Protocol
4. HTTP domain and URL
It establishes the validity of network packets, based upon a strict set of rules. Depending on the packet validity, the firewall either accepts or rejects the network packet. If the firewall encounters a packet that is suspicious or unknown, the user will be notified, depending on the security level, and asked to respond with the appropriate action to be taken.
The design of our firewall consists of three separate modules:
1. IMDrv.dll — network device driver
2. ChkPkt.dll — dynamic link library
3. FWApp.exe — application
The relation between these three modules are illustrated in Figure 1.
We have successfully developed and implemented our personal firewall on Pocket PC 2003 handheld devices. Some of the screen captures of our implementation are shown in Figure 2.
the need for mobile devices in healthcare
In healthcare, mobile healthcare involves conducting healthcare related activities through using mobile devices such as a wireless phone, personal digital assistant (PDA), wireless enabled computer, iPod and so on. Portability and accessibility of these devices enhance their use of them in healthcare environment. Moreover, ease of use, affordability, and ability to read handwriting attracted use of these devices (Al-Ubaydli, 2004). The devices would be suitable for conducting patient’s healthcare activities in emergencies, ward rounds, homecare, chronic disease management, conducting clinical trials, and so on.
Mobile computing is suitable for healthcare as healthcare providers are mobile. Healthcare providers would like to enter information in the patient record and process information during the ward round and at the point of care (Reuss, Menozzi, Buchi, Koller, & Krueger, 2004). Health information system located at the fixed terminal is inefficient because the necessary information will not be available at the time of query and that will interrupt the workflow (Eisenstadt et al., 1998).
usage of these devices
Mobile and wireless devices can assist in ensuring patient’s safety by providing easy availability of the data at the point of care. Computerised physician order entry systems are being developed in most healthcare institutions to reduce medical errors (Ash, Stavri, & Kuperman, 2003). Mobility of mobile devices embrace usage of computerised physician order entry systems (Schuerenberg, 2005) and enhance patient safety. There are various projects using mobile devices to enhance patient’s care. With the advancement of medical informatics, telemedicine, and information technology, mobile data devices play an enormous role in healthcare systems. Nursing staffs at St. Clair Hospital in Pittsburgh use PDAs equipped with peripheral scanning technology. This led to identification and prevention of 5000 errors (Anonymous, 2005). A survey and interview conducted on the usage of Personal Digital Assistants by medical residents noted that the current usage is as a single information source for personal organisation and general reference materials (Barrett, Strayer, & Schubart, 2004). However, a study conducted by Fischer, Stewart, Mehta, Wax, and Lapinsky (2003) indicated that these devices have been used for accessing medical literature, as drug information databases (pharmacopoeias), patient tracking, medical education, research data collection, business management, prescribing, speciality-specific applications such as family medicine, paediatrics, pain management, critical care, and cardiology (Fischer et al., 2003).
Two types of use of these devices can be seen in healthcare, which are download on demand (DoD) and downloading data periodically via the synchronization process (Afrin & Daniels, 2001). DoD allows the real time access of data and it is suitable for medical literature, patient tracking and various speciality specific applications. Downloading data periodically is applicable to medical educational application such as iPathology application on the iPod. A study conducted on all the American Academy of Family Physicians and American College of Osteopathic Family Practice in 2000 indicated that most commonly used operating system is the Palm on handheld computer (Criswell & Parchman, 2002). Currently, most healthcare providers use handheld devices and usage increases with emergence of smart phones and blackberry. However, only a few clinical applications are available at this stage for these devices (Al-Ubaydi, 2004).
Data integrity and confidentiality of information in these devices need to be ensured to provide safe, effective and efficient healthcare. Protecting patient confidentiality and privacy during the use of handheld device is a concern in the healthcare industry (Fischer et al. 2003). Implementing personal firewall for these devices enhances security and maintains the data integrity of health information.
conclusion and further work
In this topic, we identified handheld devices as important tools for the future. We briefly reviewed the two well-known handheld devices, namely Palm OS-based and Windows CE-based handheld devices. We also illustrated our work to secure these devices. Finally, we concluded with the use of these devices in the area of healthcare. In the future, we will be developing applications that will use handheld devices for specific purpose required in the healthcare area.
key terms
Bluetooth: Bluetooth is an industrial specification for wireless personal area network (PANs). Bluetooth provides a way to connect and exchange information between devices like personal digital assistants (PDAs), mobile phones, laptops, PCs, printers and digital cameras via a secure, low-cost, globally available short range radio frequency (Wikpedia, http://en.wikipedia.org/wiki/).
General Packet Radio Service (GPRS): GPRS is a mobile data service available to users of GSM mobile phones. It is often described as ’2.5 G’, that is, a technology between the second (2G) and third (3G) generations of mobile telephony (Wikpedia, http://en.wikipedia.org/wiki/).
Global System for Mobile Communications (GSM): GSM is the most popular standard for mobile phones in the world. GSM phones are used by over a billion people across more than 200 countries. The ubiquity of the GSM standard makes international roaming very common with “roaming agreements” between mobile phone operators. GSM differs significantly from its predecessors in that both signalling and speech channels are digital, which means that it is seen as a second generation mobile phone system. This fact has also meant that data communication was built into the system from very early on (Wikpedia, http://en.wikipedia.org/wiki/).
IrDA: IrDA refers to Infrared data association, a standard for communication between devices (such as computers, PDAs and mobile phones) over short distances using infrared signals (Wikpedia, http://en.wikipedia.org/wiki/).
Wireless LAN or WLAN: WLAN is a wireless local area network that uses radiowaves as its carrier: the last link with the users is wireless, to give a network connection to all users in the surrounding area. Areas may range from a single room to an entire campus. The backbone network usually uses cables, with one or more wireless access points connecting the wireless users to the wired network (Wikpedia, http://en.wikipedia.org/wiki/).