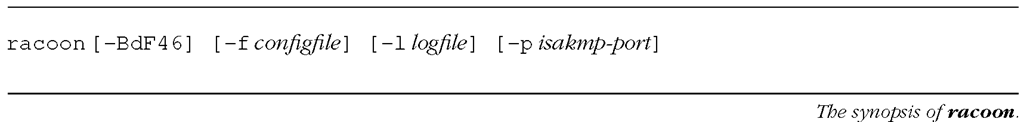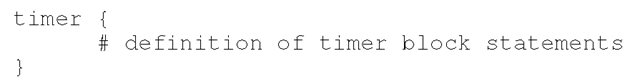Racoon is an implementation of the IKE protocol specification. It establishes SA entries between two nodes based on the SP entries configured in the kernel in advance. The parameters of the SA entries are automatically negotiated by Racoon and the IKE process running on the other end node. All we have to do is to specify the SP entries we require. When the kernel processes the outgoing packets or incoming packets, it searches the Security Policy database to see if there is any policy definition for that packet. If the kernel finds a matching SP entry, it searches for an appropriate SA entry from the SAD. If no SA entry is found, the kernel informs Racoon of the lack of required SA entry. After receiving the notification, Racoon starts the IKE negotiation procedure to establish requested SA entries.
Configuring Racoon
The command name of Racoon is racoon. racoon is a user space application. Figure 6-26 describes the synopsis of the racoon command.
In most cases, we need to create a suitable configuration file for racoon and pass the configuration file to racoon. The following describes the option switches of racoon briefly.
-B Install SA entries from the file specified by the path backupsa directive in a configuration file. racoon can back up SA entries which are negotiated in the file. The directives will be discussed in Section 6.10.2.
-d Increase log level. Multiple -d will increase log level.
-F Run racoon as a foreground process.
FIGURE 6-26
-f configfile Specify a configuration file. The default location of the configuration file depends on the build environment of racoon. /usr/local/v6/etc/racoon.conf is the default location if you are using the KAME distribution.
-l logfile Use logfile as an output file of log messages. racoon usually writes its log messages using the syslog mechanism with the LOG_DAEMON facility.
-p isakmp-port Specify the port number which is used for ISAKMP. The default port number is 500.
Configuration File Format
In this section, we explain the directives used in the racoon configuration file. To make it easy to understand the configuration format, we divide the directives into six categories.
Path specification part Specify path names which are included by a configuration file.
Timer specification part Specify several timeout/counter values.
Listening address specification part Specify the address and port number used by racoon. Remote node specification part Specify Phase-I parameters and behavior per remote node. SAinfo specification part Specify negotiation parameters of SAD entries. Other part Other miscellaneous parameters.
Path Specification
Path specification is used to define the directory in which other configuration files are located.
• path include path;
Specify the path in which other configuration files are located. Other configuration files may be specified by the include directive.
• path pre_shared_key file;
Specify the filename which contains a pre-shared secret which is used to create the ISAKMP SA entry.
• path certificate path;
Specify the path which stores X.509 certificate files.
• path backupsafile;
Specify the filename to which racoon backs up the SA entries negotiated. If the -B switch is used when executing racoon, racoon reads the contents of the specified file and recovers SA entries negotiated before.
• include file;
Include another file. We can divide the configuration file, for example, per remote node. Timer Specification
Timer specification defines the retry counter and interval. All definitions are quoted by the timer block. For example,
There are four directives.
• counter number;
Specify the retry count of IKE messages to number. The default value is 5. racoon resends a message if there is no reply where the specified timeout period is elapsed. The timeout period can be specified by the interval directive.
• interval number timeunit;
Specify the interval to resend a message. timeunit is one of sec, min, hour. The default value is 10 seconds.
• persend number;
Specify the number of packets per one message. Since ISAKMP messages are sent as UDP packets, racoon can be configured to sent multiple same messages at one time. The default value is 1.
• phasel number timeunit;
Specify the maximum time to wait to complete an ISAKMP SA creation. timeunit is one of sec, min, hour. The default value is 15 seconds.
• phase2 number timeunit;
Specify the maximum time to wait to the complete the IPsec SA creation. timeunit is one of sec, min, hour. The default value is 10 seconds.
Listening Address Specification
Listening address specification defines addresses and port numbers which racoon uses. All definitions are quoted by listen block as follows:
There are two directives.
• isakmp address [ [port] ];
Specify the address and port number to use for ISAKMP communication. If we do not specify any address in the listen directive, racoon will use all available addresses for ISAKMP communication. The port number is 500, if it is not specified explicitly. The port number must be quoted by brackets ([ and ] ) if specified.
• strict_address;
If strict_address is specified, racoon will exit when binding addresses by the isakmp directive fails. This statement does not have any effect if isakmp is not specified.
Remote Node Specification
Remote node specification defines parameters used in Phase-I per remote node or a set of remote nodes. The statements are quoted by the remote block.
The remote directive has up to two arguments. The first argument which is used to specify the address of a remote node is mandatory. We can specify the exact address of the remote node or anonymous. When anonymous is specified, all communications for Phase-I use the same parameters defined in this remote block, unless there are other specific remote blocks for a particular node.
If we want to use a port number other than the default ISAKMP port number (500), port can be specified.
• exchange_mode main | aggressive | base;
Specify the exchange mode that racoon uses to establish ISAKMP SA. Possible options are main, aggressive and base, which means the main mode, the aggressive mode, and the base mode, respectively.
• doi ipsec_doi;
Declare that racoon uses key exchange parameters defined in [RFC2407]. Since racoon does not support other domains of interpretation, this statement can be omitted.
• situation identity_only;
Declare that racoon uses SIT_IDENTITY_ONLY as a situation definition. Other types of definitions defined in [RFC2407] are not supported. This statement can be omitted.
• my_identifier type;
Specify the type of identifier of this node. The remote IKE process distinguishes the local node by this identifier. The following five types are defined.
— address [address]
The identifier is an IP address. If we do not specify the type of identifier by the my_identifier directive, address is the default type.
— user_fqdn string
The identifier is a fully qualified domain name with user name.
— fqdn string
The identifier is a fully qualified domain name. For example, mobilenode1.kame.net.
— keyid file
Specify the identifier as the ID_KEY_ID type defined in [RFC2407]. The identifier should be stored in file. file is just a byte stream of arbitrary length.
— asn1dn [string]
Specify the identifier as an ASN.1 distinguished name specified by string. string must be the same as specified in the subject field in the certificate file of this node. If string is omitted, racoon automatically extracts a distinguished name from the subject field of the X.509 certificate.
• peers_identifier type;
Specify the identifier of a peer node. type has the same format as that used in the my_identifier directive. Note that racoon verifies the peer’s identifier only if the peer’s identifier is defined by this parameter and the verification is enabled by the verify_identifier directive.
• verify_identifieron|off;
If set to on, racoon verifies the identifier passed by the communicating node. If the identifier does not match the identifier defined by the peers_identifier directive, racoon aborts the Phase-I negotiation. The default value is off.
• certificate_type x509 certfileprivatekeyfile;
Specify the X.509 certificate file of the local node. certfile is the file name of the certificate file and privatekeyfile is the file name of the private key.
• peer_certfile dnssec | certfile;
Specify the certificate file of a peer node. If dnssec is specified, racoon tries to retrieve the peer’s certificate using DNS. Otherwise, certfile should be specified as the file name of the certificate file of the peer node.
• send_cert on|off;
Specify whether racoon sends the certification of the local node. The default is on.
• send_cron|off;
Specify whether racoon requests the certification of a peer node. The default is on.
• verify_cert on|off;
Specify whether racoon verifies the certificate file sent from a peer. The default is on.
• lifetime time number timeunit;
Specify the lifetime of ISAKMP SA entries. The lifetime can be specified separately for each proposal by the proposal block if the exchange_mode is set to main.
• initial_contact on | off;
Specify if racoon sends INITIAL-CONTACT messages when it communicates with peer nodes the first time. This is useful when a node is unintentionally rebooted or has crashed. The remote node may still have the state of the local node, which is already outdated. Since the INITIAL-CONTACT message suggests removing all existing state information corresponding to the local node, the IKE procedure can be started cleanly. The default is on.
• passive on|off;
If set to on, racoon will act as only a responder. That is, racoon never initiates IKE negotiation. The default is off.
• proposal_check level;
Specify the proposal check level. racoon compares the length of lifetime and PFS (Perfect Forward Secrecy) group of the Phase-II proposal sent from the initiator when it is acting as a responder. If those values are different from the local proposal, then racoon acts based on the following specified level.
— obey
Always obey the proposal of an initiator.
— strict
If the lifetime of the responder is longer than the proposal of an initiator, the lifetime of the initiator is used. Otherwise, the proposal is rejected.
If PFS is not required by the responder, the responder will accept one of proposals based on the lifetime validation above.
If PFS is required by both nodes and the group specified as a PSF group is different, the responder rejects the proposal.
— claim
If the lifetime of the responder is longer than the proposal of that of the initiator, the lifetime of the responder is used. With regard to PFS, the same rules are applied with the case of strict.
— exact
Accepts a proposal only when the lifetime of the responder is equal to the lifetime of the initiator. With regard to PFS, the same rules are applied with the case of strict.
• generate_policy on | off;
In some cases, an administrator may want to accept a node which has a dynamically assigned IP address. Since the IP security processing requires pre-configured SP entries, such a node cannot use IP security. If the generate_policy directive is set to on, racoon will install an SP entry based on the contents of the proposal for Phase-II. This directive has an effect only when racoon is acting as a responder. The default value is off.
• nonce_size number;
Specify the length of nonce in a unit of a byte which is exchanged in Phase-I. Usually, number is 8 to 256 as specified in [RFC2409].
• proposal
The proposal block defines parameters for Phase-I negotiation. The following directives can be specified.
— encryption_algorithm algorithm;
Specify the encryption algorithm used for Phase-I. Any one of des, 3des, blowfish or cast128 can be specified.
— hash_algorithm algorithm;
Specify the hash algorithm used for Phase-I. Either md5 or sha1 can be specified.
— authentication_method type;
Specify the type of authentication method for Phase-I. Either pre_shared_key, rsasig or gssapi_krb can be specified.
— dh_group group;
Specify the group of Diffie-Hellman exponentiations. Either modp7 68, mpdp1024 or modp1536 can be specified. Or, just specify the number of DH group as 1, 2 or 5 respectively.
— lifetime time number timeunit;
Specify the lifetime of ISAKMP SA entries for each proposal. This can be specified when racoon uses the main mode in the exchange_mode directive.
—gssapi_id string;
Specify the GSS-API endpoint name.
SAinfo Specification
The SAinfo specification defines parameters for IPsec SA entries which are negotiated in Phase-II. All parameters must be specified in the sainfo block.
source_id and destination_id are either of the following formats.
• address address{/prefixlen}{ [port] } ul_proto ul_proto is a transport protocol name.
• idtype string
idtype is either user_fqdn or fqdn.
The sainfo block has the following directives.
• pfs_group group;
Specify the group of Diffie-Hellman exponentiations. This directive is required when we need PFS for Phase-II negotiation.
• lifetime time number timeunit; Specify the lifetime for IPsec SA entries.
• encryption_algorithm algorithm{, algorithm …};
• authentication_algorithm algorithm{, algorithm …}; Specify available algorithms for IPsec SA entries.
Algorithms for encryption can be chosen from des, 3des, des_iv64, des_iv32, rc5, rc4, idea, 3idea, cast128, blowfish, null_enc, twofish, or rijndael. Algorithms for authentication can be chosen from des, 3des, des_iv64, des_iv32, hmac_md5, or hmac_sha1.
If the specified algorithm has a variable key length, the bit length can be specified immediately after the name of the algorithm. For example, blowfish 44 8 for using the blowfish algorithm with a 448-bit key.
racoon automatically expands the possible combinations based on the specified algorithms above, and includes all of them in the proposal.
Other Specifications
We can specify the logging level by the log directive.
• log level;
level is either notify, debug or debug2. notify is the default level.