Introduction
With the rapid growth of networked systems and applications such as e-commerce, the demand for effective computer security is increasing. Most computer systems are protected through a process of user identification and authentication. While identification is usually non-private information provided by users to identify themselves and can be known by system administrators and other system users, authentication provides secret, private user information which can authenticate their identity. There are various authentication approaches and techniques, from passwords to public keys (Smith, 2002).
This article presents the three main authentication approaches, their technology and implementation issues, and the factors to be considered when choosing an authentication method.
background
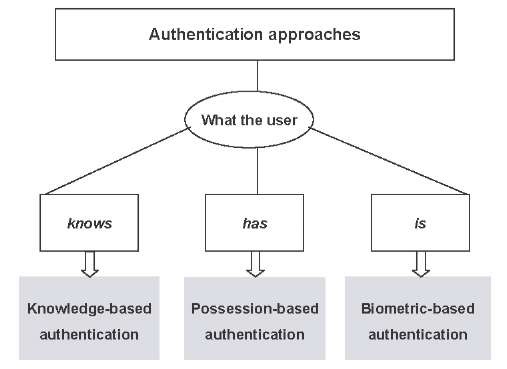
Even before computers came along, a variety of distinguishing characteristics were used to authenticate people. Computer systems have applied these characteristics for user authentication. The authentication approaches can be classified into three types according to the distinguishing characteristics they use (Menkus, 1988), as presented in Figure 1:
• What the user knows—knowledge-based authentication (e.g., password, PIN, pass code)
• What the user has—possession-based authentication (e.g., memory card and smart card tokens)
• What the user is—biometric-based authentication: physiological (e.g., fingerprint) or behavioral (e.g., keyboard dynamics) characteristics
Figure 1. Classification of authentication methods
As all these authentication types have benefits and drawbacks, trade-offs need to be made among security, ease of use, and ease of administration. Authentication types can be implemented alone or in combination. To strengthen the authentication process, the use of at least two types is recommended. Multiple layers of different types of authentication provide substantially better protection.
knowledge-based authentication
The most widely used type of authentication is knowledge-based authentication. Examples of knowledge-based authentication include passwords, pass phrases, or pass sentences (Spector & Ginzberg, 1994), graphical passwords (Thorpe & Van Oorschot, 2004; Wiedenbeck, Waters, Birget, Brod-skiy, & Memon, 2005), pass faces (Brostoff & Sasse, 2000) and personal identification numbers (PINs). To verify and authenticate users over an unsecured public network, such as the Internet, digital certificates and digital signatures are used. They are provided using a public key infrastructure (PKI) which consists of a public and a private cryptographic key pair (Adams & Lloyd, 1999).
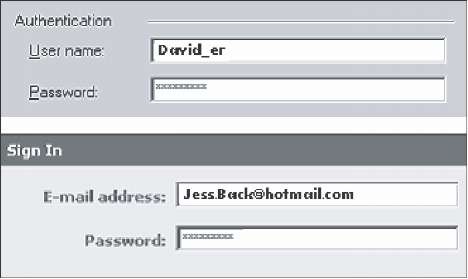
The traditional, and by far the most widely used, form of authentication based on user knowledge is the password (Zviran & Haga, 1993). Most computer systems are protected through user identification (like user name or user e-mail address) and a password, as shown in Figure 2.
Figure 2. Authentication through user identification and password
A password is conceptually simple for both system designers and end users. It consists of a secret series of characters according to some predefined rules. The user ID and password pair acts as user identification and authentication and serves to block unauthorized access to computing resources. In most systems, it can provide effective protection if used correctly.
However, passwords are known to suffer from a number of pitfalls due to human information processing limitations (Sasse, Brostoff, & Weirich, 2001; Yan, Blackwell,Anderson, & Grant, 2005). First, there is a trade-off between memorability and security. Passwords should be difficult to guess and easy to remember. The fact that difficult-to-guess and difficult-to-crack passwords are difficult to remember and that easy to remember passwords are easy to guess and easy to crack poses a dilemma for the generation of passwords. The most secure password is a random string of characters. Such passwords are difficult to guess by others, but at the same time are difficult to remember and thus compel the users to write them down, which impairs their secrecy. Moreover, most users have multiple passwords for different systems and applications, forcing them to remember several passwords. In order to help them to remember the passwords, they usually choose meaningful strings such as names, nicknames, or initials (Adams & Sasse, 1999), which are easy to remember but also easy to crack. They also tend to duplicate their passwords and thus cause the domino effect of password reuse (Ives, Walsh, & Schneider, 2004); namely, all the systems with the same password are no more secure than the weakest system using this password.
In order to improve password security and protect it from dictionary and brute force attacks, password policy should implement rules for choosing and maintaining passwords (Smith, 2002). The major rules are:
• Non-dictionary and no-name passwords.
• Long enough passwords with mixed types of characters.
• Password ageing and not reusing.
• Complex passwords using acronyms, rhymes, and mnemonic phrases, which are difficult to guess and easy to remember (Carstens, McCauley-Bell, Malone, & DeMara, 2004; Yan et al., 2005).
• Passwords should not be shared and should not be written down.
• The number of unsuccessful authentication attempts should be limited by the system.
• Passwords should never be stored in clear text; they should be encrypted or hashed.
Passwords based on the aforementioned rules are more effective, more difficult to identify and to determine by cracking utilities. To overcome the problem of sniffing passwords when authentication is performed over the Internet, one-time passwords are used. The one-time password can be implemented using smart cards—a kind of possession-based authentication discussed hereafter.
Passwords, used as the first level of authentication, that allow access to information system resources through operating systems are commonly referred to as primary passwords. Passwords used as the second level of authentication, for further control and protection of multi-level access to segments of these resources, such as sensitive applications or data files, are commonly referred to as secondary passwords (Zviran & Haga, 1993).
In determining primary passwords, the operating system manufacturer uses system-generated passwords or user-generated passwords with predefined rules. User-generated passwords are shown to be easier to remember but less secure than system-generated passwords as they can be easily guessed (Lopez, Oppliger, & Pernul, 2004).
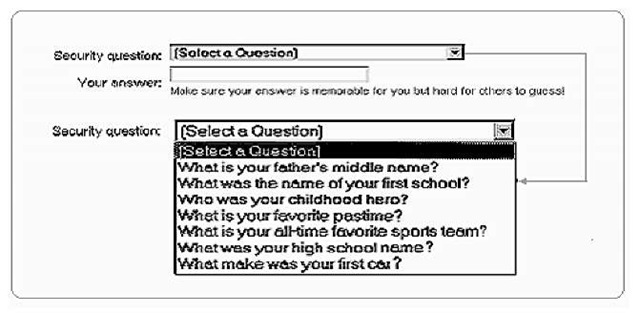
In order to overcome the difficulty of remembering passwords, a question-and-answer password method has been suggested (Haga & Zviran, 1991). This method is mainly used for secondary passwords. It involves a dialogue between the user and the system, as shown in Figure 3.
Figure 3. Example of a question-and-answer password
In a typical question-and-answer session, the user is presented with several randomly selected brief questions from a set of questions stored in his or her profile in the operating system. Access to a system or to a particular application is granted only upon a match between the user’s answers and those stored in his/her profile.
The two main types of question-and-answer passwords are: cognitive passwords and associative passwords (Bun-nell, Podd, Henderson, Napier, & Kennedy-Moffat, 1997; Haga & Zviran, 1991; Zviran & Haga, 1993). In cognitive passwords, the user must provide the system with answers to personal fact-based or opinion-based questions, such as the user’s mother’s maiden name (fact-based) or user’s favorite type of music (opinion-based).
In associative passwords, the user must provide the system with a set of word associations, consisting of both cues and their unique associated responses.
possession-based authentication
Possession-based authentication, referred to also as token-based authentication, is based on what the user has. It makes use mainly of physical objects that a user possesses, like tokens. Aside from the fact that presentation of a valid token does not prove ownership, as it may have been stolen or duplicated by some sophisticated fraudulent means (Svi-gals, 1994), there are problems of administration and of the inconvenience to users of having to carry them.
Tokens are usually divided into two main groups: memory tokens and smart tokens. Memory tokens store information but do not process it. The most common type of memory token is the magnetic card, used mainly for authentication together with a knowledge-based authentication mechanism such as a PIN. Memory tokens are inexpensive to produce. Using them with PINs provides significantly more security than PINs or passwords alone.
Unlike memory tokens, smart tokens incorporate one or more embedded integrated circuits which enable them to process information. Like memory tokens, most smart tokens are used for authentication together with a knowledge-based authentication mechanism such as a PIN. Of the various types of smart tokens, the most widely used are those that house an integrated chip containing a microprocessor. Their portability and cryptographic capacity have led to their wide use in many remote and e-commerce applications (Juang, 2004; Ku & Chen, 2004; Wu & Chieu, 2003). Due to their complexity, smart tokens are more expensive than memory tokens but provide greater flexibility and security and are more difficult to forge. Because of their high security level, smart tokens are also used for one-time passwords for authentication across open networks.
biometric-based authentication
Biometric-based authentication is based on what the user is, namely, automatic identification using certain anatomical, physiological or behavioral features and characteristics associated with the user (Kim, 1995; Wayman, Jain, Maltoni, & Maio, 2004). Biometric authentications are based on the fact that certain physiological or behavioral characteristics reliably distinguish one person from another. Thus, it is possible to establish an identity based on who the user is, rather than on what the user possesses or knows and remembers. Biometrics involves both the collection and the comparison of these characteristics. A biometric system can be viewed as a pattern recognition system consisting of three main modules: (1) the sensor module, (2) the feature extraction module, and (3) the feature matching module. The users’ personal attributes are captured and stored in reference files to be compared for later authentication to determine if a match exists. The accuracy of the different biometric systems can be evaluated by the measurement of two types of errors (Matyas & Stapleton, 2000): (1) erroneous rejection, that is, false non-match (type I error), and (2) erroneous acceptance, that is, false match (type II error). In a biometric system that provides a high level of authentication, the rate of these two errors is low.
Biometric authentications are technically complex and usually expensive as they require special hardware. Although all biometric technologies inherently suffer from some level of false match or false non-match, they have a high level of security. Despite their high security, they do not have a high acceptance rate by users as they are perceived to be intrusive and an encroachment on privacy (Prabhakar, Pankanti, & Jain, 2003) through automated means. They also raise ethical issues of potential misuse of personal biometrics such as for tracking and monitoring productivity (Alterman, 2003). Thus, they are not popular and mainly used in systems with very high levels of security.
The emergence of biometric authentication addressed the problems that plagued traditional verification methods, providing the most effective and accurate identification method with an edge over traditional security methods in that it cannot be easily stolen or shared. Biometric systems also enhance user convenience by alleviating the need to determine and remember passwords. However, while convenient, the digital scan or pattern is vulnerable to network analysis and once stolen, can no longer be used (Ives et al., 2004).
There are various kinds of biometrics (Matyas & Staple-ton, 2000) and they are usually divided into two main categories: physiological and behavioral biometrics. Physiological biometrics are based on the user’s stable physical attributes. The best known are fingerprints, finger scans, hand geometry, iris scans, retina scans, and facial scans. Fingerprints are the most widely used physiological characteristic in systems that automatically recognize a user’s identity (Ratha & Bolle, 2005; Wayman et al., 2004). An example of one of its up-to-date applications is the use of fingerprint-based identification and authentication to support online, Web-based course examinations (Auernheimer & Tsai, 2005).
Behavioral biometrics are based on users’ behavioral attributes that are learned movements (Guven & Sogukpinar, 2003; O’Gorman, 2003; Yu & Cho, 2004). The best known are: keystroke dynamics, signature dynamics, mouse dynamics, and speech or voice verification.
FACTORS IN CHOOSING AN AUTHENTICATION METHOD
In choosing an authentication method a number of factors need to be considered: effectiveness, ease of implementation, ease of use, and user attitude and acceptance (Furnell, Dowland, Illingworth, & Reynolds, 2000). Table 1 shows the ranking of the three authentication types according to these four factors.
The knowledge-based authentication type is inexpensive and easy to implement and change. Unfortunately, it is also the easiest to compromise and is less secure than tokens or biometric-based authentication methods, which are inherently more secure. On the other hand, tokens and biometric-au-thentication methods are more expensive to implement. User attitudes towards knowledge-based authentication are highly positive, less positive towards possession-based authentication, and negative towards biometric-based authentication (Deane, Barrelle, Henderson, & Mahar, 1995; Prabhakar et al., 2003). As knowledge-based authentication is less effective than the other types, it is recommended that it be used in two-type authentication; for example, a password and a token or a password and a keystroke (Furnell, Papadopoulos, & Dowland, 2004; Yu & Cho, 2004).
Passwords provide the most cost effective solution, they are portable to other applications, easy to deploy and scale to an unlimited number of users. They are integrated into many operating systems and users are familiar with them.
Table 1. Ranking of authentication types from 1 (low) to 3 (high)
| Factor | ||||
| Authentication type | Security effectiveness | Ease of
implementation |
Ease of use | User attitude and acceptance |
| Knowledge-based | 1 | 3 | 3 | 3 |
| Possession-based | 2 | 2 | 2 | 2 |
| Biometric-based | 3 | 1 | 1 | 1 |
Improved security can be achieved with a secondary technique, like a cognitive or associative password.
Possession-based authentication using tokens provides higher security than knowledge-based authentication. Most of the problems associated with tokens relate to their cost, administration, loss, and user dissatisfaction. Because of vulnerability to theft, a token should not be used alone but with another authentication type. When combined with a password, it can provide major advantages as it can store or generate multiple passwords, and the user has to remember only the single password needed to access the token.
FUTURE TRENDS
Since passwords are comparatively inexpensive, simple to use, and attractive to users, they will probably continue to be the most widely used form of authentication in the foreseeable future. When properly managed and controlled, they can provide effective security. Further research is needed on the three authentication types to improve and enhance their technologies and to enable the design of more usable and effective security systems.
CONCLUSION
Computer systems are protected by three main types of authentication approaches: (1) knowledge-based, (2) possession-based, and (3) biometric-based. Each of these has both benefits and drawbacks. When choosing an authentication method we have to consider the trade-off among security effectiveness, ease of implementation, ease of use, and user attitude and acceptance. In order to strengthen the authentication process, the use of at least two-type authentication is recommended.
Overall, there is no one best solution to the user authentication problems. Multiple layers of protection provide substantially better security.
KEY TERMS
Associate Password: A question-and-answer password in which the user provides the system with associated responses to rotating cues.
Authentication: Verifying the identity of the user. There are three main approaches to user authentication: knowledge-based, possession-based, and biometric-based.
Biometric-Based Authentication: An authentication based on what the user is—unique physiological characteristics such as fingerprints or behavioral characteristics such as keyboard dynamics.
Cognitive Password: A question-and-answer password in which the user provides the system with answers to personal, fact-based questions such as the user’s mother’s maiden name, or opinion-based questions such as the user’s favorite type of music.
Identification: The activity of users who supply information to identify themselves, such as name, user name, and user ID.
Knowledge-Based Authentication: An authentication based on what the user knows, such as password, PIN, and pass code.
Password: Knowledge-based authentication consisting of a secret series of characters according to predefined rules.
It is the most widely used mechanism of authentication.
Possession-Based Authentication: An authentication based on what the user has, such as memory cards and smart card tokens. Possession-based authentication is also referred to as token-based authentication.
Question-and-Answer Password: A session in which a user is presented with several randomly selected questions from a set of questions stored in the user’s profile in the operating system. The user’s answers are compared to match with those stored in the profile. The two main types of question-and-answer passwords are cognitive passwords and associative passwords.