Cryptography Reference
In-Depth Information
AES-128 key
AES-192 key
SW
SW
RW
RW
Rcon
[1]
Rcon
[1]
(a)
(b)
AES-256 key
SW
SW
K
0
RW
K
1
K
2
K
3
Rcon
[1]
(c)
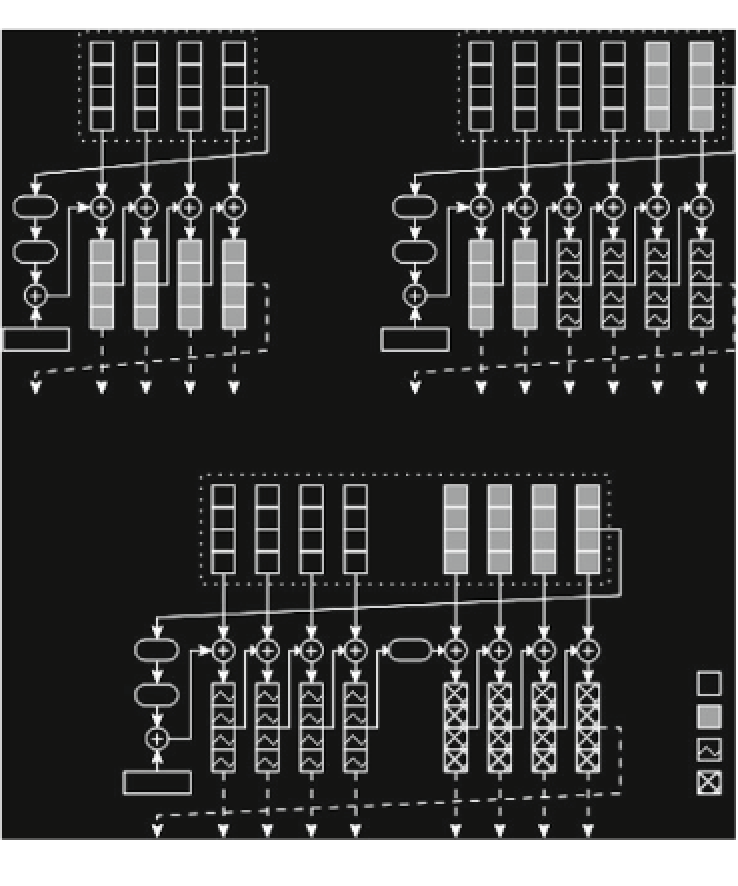
Fig. 4.4
Beginning of the AES key scheduling.
a
AES-128 Key expansion.
b
AES-192 key expan-
sion.
c
AES-256 key expansion
the principle of DFA on the AES, we describe three of the most efficient attacks pub-
lished so far. The first one is often cited as a reference by many variants published
afterwards. It presents a very good compromise between the fault model and the
required number of faulty ciphertexts. Secondly, we present an attack on the middle
rounds of the AES. It allows an attacker to efficiently recover the secret key even
if the last four rounds of the AES are protected against fault attacks. Thirdly, we
describe an attack which is very efficient in terms of fault model since it allows the
disturbance of three diagonals of the State array. Finally, we briefly present some
attacks exploiting faults induced during the first rounds. These attacks can be very
efficient in practice if only the last rounds are protected against fault injection.