Cryptography Reference
In-Depth Information
K
r
−2
K
r
−1
K
r
Key scheduling
Key scheduling
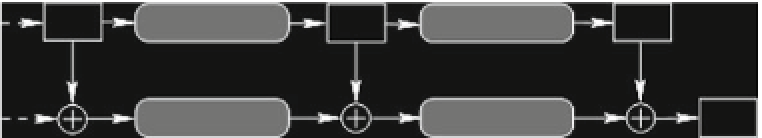
MC
SR
SB
SR
SB
C
Fig. 4.3
The last two rounds of the AES
4.
AddRoundKey
, in which a round key is added to the State by using the bit-wise
XOR operation.
The last round is composed of the same transformations as the other rounds, with
the exception of the
MixColumns
transformation; cf. Fig.
4.3
.
The AES key scheduling provides
r
1 round keys
K
i
of 128 bits,
r
depending
on the AES key length (cf. Table
4.1
). To do so, the AES key is firstly expanded into
a 128
+
1 round keys.
The key expansion is performed by operating on the columns of the array repre-
senting the AES key. Figure
4.4
depicts the beginning of the expansion where
(
r
+
1
)
-bit buffer, then split into
r
+
•
SubWord
(RW) applies the AES S-Boxto each of the four bytes of its input,
•
RotWord
(RW) is a rotation such that a four-byte input
(
a
,
b
,
c
,
d
)
gives
(
b
,
c
,
d
,
a
)
,
x
i
−
1
,
x
i
−
1
•
Rcon
[
i
]
is a four-byte array defined by
Rcon
[
i
]=
(
,
{
00
}
,
{
00
}
,
{
00
}
)
F
2
8
.
For more information about the AES, the reader can refer to [113].
Since May 2002, the AES has been the new standard for symmetric encryption.
It has been therefore used more and more for secure applications, in particular in the
embedded environment. In the latter case, the implementations of the AES must resist
specific attacks such as side-channel analysis (e.g. SPA, DPA) and fault analysis (e.g.
DFA). This chapter deals with the state of the art of Differential Fault Analysis of
the AES and it is organized as follows. Section
4.2
presents the principle of DFA on
the AES before describing in detail three of the most efficient attacks. These attacks
allow an attacker to recover the AES key with a very relaxed fault model and/or a
very small number of faulty ciphertexts. In Sect.
4.3
we compare the characteristics
of the various DFAs on the AES published so far. Finally we present in Sect.
4.4
the different specific countermeasures which have been proposed to protect the AES
against DFA.
being a power of
x
(
x
represented by
{
02
}
) in the field
4.2 Differential Fault Analyses of the AES
When Rijndael was selected as the AES, no DFA was known against this new cryp-
tosystem. Indeed, in 2000 only the original differential fault attack of Biham and
Shamir [49] was known on symmetric cryptosystems and it does not directly apply
to Rijndael. Therefore, many researchers have worked on this subject and many
DFAs on the AES have been published since 2000. In this section, after presenting