Cryptography Reference
In-Depth Information
K
r
−1
K
r
MC
SB
SR
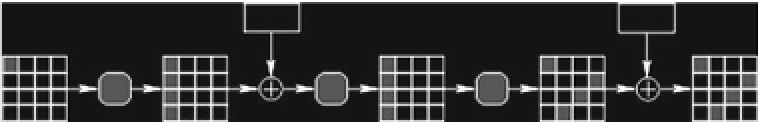
Fig. 4.5
Propagation of the differential by assuming a byte fault at the input of
MixColumns
of
round
r
−
1
4.2.1 Principle of DFA on the AES
The objective of an attacker performing DFA on the AES is to recover enough
information on the last round key (or the last two round keys) to be able to mount an
exhaustive search to recover the AES-128 key (or AES-192 or AES-256 key).
To obtain information on the last round key(s), the principle of DFA on the AES is
to analyze the differential at some point between a correct and a faulty AES execution.
Such a differential is computed from a guess on a small part of the last round key
and from a pair
C
)
of correct and faulty ciphertexts. If the guess is correct,
the differential must satisfy some properties depending of the corresponding fault
model, which gives us a key distinguisher.
(
C
,
4.2.2 The Standard DFA on the AES
At CHES 2003, Piret and Quisquater presented a new DFA on the AES which requires
few faulty ciphertexts and a relaxed fault model [324]. Such a combination is rare
and it makes this attack a reference. In the rest of this section, we first present their
attack, before presenting its application to AES-192 and AES-256.
4.2.2.1 Basic Attack
The principle of this attack is to induce a fault resulting in a differential of one byte
at the input of the last
MixColumns
. By guessing four bytes of the last round key, the
attacker tests if the corresponding differential at the output of the last
MixColumns
corresponds to a one-byte differential at its input.
First of all, the attacker computes a list
of possible differences at the output
of one column of the
MixColumns
transformation, assuming a one-byte difference
at its input. The list
D
255 four-byte elements. This operation is
done only once and can be used for future attacks.
Secondly, the attacker obtains a pair
D
thus contains 4
×
C
)
of correct and faulty ciphertext,
C
obtained from a random byte fault injected into the input of the
MixColumns
transformation of round
r
(
C
,
−
1. If the fault is injected into the first column of this
State then
C
will differ from
C
in bytes at position 0, 7, 10 and 13. If the fault is