You always want to capture packets as efficiently and concisely as possible. Starting a capture and leaving it unattended gives you a huge data file that you have to sift through for information. Start packet captures just before a test call, and then close the capture immediately after completing the test call.
The exact location of the packet capture command varies, depending on how you loaded the tcpdump software. A package management application may establish the packet capture command in one location, but you may have manually installed it somewhere else. Fortunately, you can easily track down the capture file by viewing the Linux command used to initiate it. The command commonly identifies the destination file location, allowing you to let the capture reside in the default directory (where you or your technician installed tcpdump or Wireshark) or in another directory that you specified.
Capturing packets with tcpdump
The tcpdump command-line syntax can be complex and includes many elements that you may never need to use. You execute the packet capture for tcpdump from a Linux session with this command:
![]()
The preceding command is made up of the following elements:
tcpdump: Tells Linux the software you’re using.
-w newfilename.log: Identifies the name that Linux attributes to the capture file. Change the name for each packet capture by adding a number to them, such as capturel, capture2, and capture3. You can make multiple captures while identifying the chronology of those captures.
expression: Identifies the specific elements to which you want to restrict your search. Do a little research of possible expressions in the manual page of tcpdump to figure out how to restrict your search to only the data you require. For example, the following expression captures data on only port 5060, to or from the specified host:
![]()
The capture continues until you stop it by pressing Ctrl+C.
Figure 11-1 identifies the participants of a VoIP call and the conversations that your VoIP proxy enabled with tcpdump can capture. The port or IP address that you specify as the basis for your capture restricts the data that the tcpdump receives.
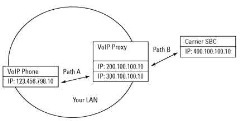
Figure 11-1:
A tcpdump capture scenario.
The most important information that you need when capturing data is the IP address or port from which (or to which) you want to focus the capture. To initiate a capture from the main IP address of 200.100.100.10 listed in Figure 11-1, execute the following command from the Linux CLI:
![]()
Packet-capturing software can monitor a network interface, such as an IP port, in two ways:

Promiscuous mode monitoring: Captures all packets traveling across the interface, regardless of whether they’re originating from or terminating at the tcpdump’s VoIP proxy. Tcpdump installed on your SIP proxy captures packets that pass through the proxy, but originate from other devices on the LAN, if the software is in promiscuous mode.
tcpdump runs in promiscuous mode by default.
Nonpromiscuous mode monitoring: Restricts the packets captured to only the data received by or sent from the specific interface identified in the capture.
The information gathered in the capture is saved as a file called Newtestfile. log that was specified in the line of code used to initiate the capture. As mentioned before, you can name the capture files whatever you want, and place their names in a sequence as well if you are executing several captures in rapid succession. The capture file tcpdump saves in the same directory as the rest of your
tcpdump software (unless you specify a full path name along with your filename in the line of code you use to initiate the capture). The promiscuous mode capture file includes information about all data transferred through that IP address, not just the SIP, SDP, and RTP information for the test call.
Promiscuous mode monitoring captures every packet of data passing through the server running the capture. This can generate huge files of data due to other LAN traffic that isn’t applicable to the research you may be doing. This could result in a slower response time when trying to open or analyze a packet capture. To avoid distilling the information after the fact, simply execute the command in nonpromiscuous mode, as follows:
![]()
Capturing packets with Wireshark
You may find capturing packets with Wireshark much simpler than with tcpdump, as long as your version of Linux has a GUI interface. If your distro doesn’t have a GUI desktop that resembles the desktop of a Mac or Windows PC, then you need to use the command-line version of Wireshark called TShark. If your only Wireshark option is to use TShark, just use tcpdump to capture the data because the commands required are easier and presented for you in the previous section of this topic.
To start and stop a capture by using the Wireshark GUI, follow these steps:
1. Choose CaptureOOptions from the main menu bar.
A window pops up, identifying all the available capture options.
2. Select the options you want and confirm the choices.
These options include the interface, capture filter, and any other specifics you require.
The software provides drop-down lists whenever possible for you to use when selecting interfaces and IP addresses on the server. The interface option on the menu bar lists the network devices from which you can initiate the capture such as Internet Port 1 or Ethernet adaptor. Wireshark allows you to further refine the capture using preset filters available by pressing the Capture Filter: button revealing specific ports and protocols the capture will isolate, ignoring all other packets that don’t meet the filter criteria.
3. Click the Start button to start the capture.
The options window disappears when the capture begins.
4. Choose CaptureOStop on the main Menu bar to close the capture.
Or click Ctrl+E.
5. Select FileOSave As on the main Menu bar and save the file in a location from which you can move or e-mail it to your PC.
You can also execute the packet captures by choosing CaptureOInterfaces on the main Menu bar. A pop-up window appears, identifying all the available interfaces from which you can capture packets. This window has a Start button conveniently located jn the pop-up window identifying the interfaces on which you can execute your capture, which makes beginning the capture easier than using the previously mentioned multi-step process. You can stop the capture either by choosing CaptureOStop in the main Menu bar or pressing Ctrl+E.

