In This Chapter
Understanding the computer nasties
Fighting pop-up windows
Dealing with fake Web pages
Using a firewall Stopping spyware Inoculating against viruses Coping with the UAC warnings any PC users harbor fears. There is the fear that the computer will get angry with you. There is the fear that you will suddenly, unpredictably, and irrevocably lose all your stuff. Then there is the fear that the bad guys are lurking around every corner on the Internet, waiting to steal from you. It makes you wonder why anyone ever bothers to turn on the computer.
The PC will never be angry with you. You might lose your stuff, but it’s possible to get that stuff back. That last fear, though, is real: The bad guys are out there. You can do a lot to help fend off their attacks, starting by reading the good information in this chapter.
To help save your stuff, see Chapter 22 for information on computer backup.
For more information on PC security, refer to my topics Troubleshooting Your PC For topic and its larger, more encompassing big brother, Troubleshooting & Maintaining Your PC All-In-One For topic (both from Publishing, Inc.).
Fight the Bad Guys
The PC bad guys have a host of names as rich and colorful as any comic topic (see the following sidebar, “PC super-villain roundup”). Knowing the names is important only when you also know the names of the superheroes who help you thwart the plans of the evil ones. Windows has many such superheroes:
Internet Explorer: Microsoft’s Web browser, Internet Explorer, comes with a rich set of features for keeping your computer safe. These include ample warnings when software tries to install itself in your PC from the Internet as well as ways to protect you from visiting phony Web sites.
Windows Defender: The Windows Defender program helps you scan for and remove a clutch of bad guys, especially insidious start-up programs and spyware.
Windows Firewall: The firewall helps to close the windows and bar the doors that bad guys use to infect PCs.
Windows Update: Keeping your PC’s software up-to-date is important because the bad guys like a target that stands still.
Backup: To keep your stuff safe, I recommend that you back it up. The backup procedure creates a safety copy of all files on your PC so that if disaster strikes — naturally created or motivated by evil — you can recover your
stuff.
Antivirus: Your PC needs a good antivirus program to fight infections that fly in from the Internet or arrive on rogue media. Windows doesn’t come with a specific antivirus program, but you can easily obtain a free program. See the section “Antivirus protection,” later in this chapter.
Bottom line: Use these tools to help keep your PC safe and its owner happy.
See Chapter 22 for information on using Backup to protect your PC’s files.
See Chapter 23 for information on using Windows Update.
You can avoid many nasty programs by simply using common sense. In fact, the most successful computer viruses have propagated simply because of human nature. It’s that human engineering the bad guys count on, or your ability to be tricked into doing something you wouldn’t do otherwise, such as open a questionable e-mail attachment or click a Web page link because you’re fooled into thinking, “Your PC is at risk!”
Your ISP can be of great help in dealing with nasty programs on the Internet. Don’t forget to use their assistance, especially when you first try fixing things on your own and it doesn’t help.
PC supervillain roundup
As with most things about computers, malicious software, or malware, is named in either a technical or silly manner. Neither name helps: The technical name is confusing, and the silly name is clever for only people who would otherwise understand the technical names. Regardless, here’s your handy guide:
phishing: Pronounced “fishing,” this term applies to a Web page or an e-mail designed to fool you into thinking that it’s something else, such as your bank’s Web page. The idea is to fish for information, such as account numbers and passwords. The Web page or e-mail tricks you into providing that information because it looks legitimate. It isn’t.
pop-up: A pop-up isn’t a nasty program, but it can be annoying — especially when you’re assaulted by several pop-ups all at once. How any legitimate marketing person would believe that multiple, annoying pop-up windows would entice anyone to buy something is beyond me, but it happens and you can stop it.
spyware: A rather broad category, spyware refers to a program that monitors, or spies on,what you do on the Internet. The reasoning is advertising: By knowing where you go and what you do on the Internet, information obtained about you can be sold to advertisers who then target ads your way.
Trojan: A program is labeled a Trojan (horse) whenever it claims to do one thing but does another. For example, a common Trojan is a special screen saver that saves the screen but also uses your PC on the Internet to relay pornographic images.
virus: A virus is a nasty program that resides in your PC without your knowledge and infects the computer. The program may be triggered at any time, where it may take over the computer, redirect Internet traffic, use your computer to flood out spam messages, or do any of a number of nasty and inconvenient things.
worm: A worm is simply a virus that replicates itself, by sending out copies to other folks on your e-mail list, for example.
Internet Explorer Tools
Internet Explorer comes with a host of security features as well as extra bul-letproofing to help keep you safe on the Internet. The feature list is vast, so for brevity I limit my discussion in the following sections to the two most annoying issues: pop-up windows and phishing.
Blocking pop-ups
To confirm that pop-ups are being blocked in Internet Explorer, follow these steps:
1. Start Internet Explorer.
2. Click the Tools button on the toolbar.
The Tools menu appears (pops up, actually).
3. Choose Pop-up Blocker.
The Pop-Up Blocker submenu is displayed.
4. Choose Turn On Pop-Up Blocker, if necessary, and then click the Yes button to confirm.
Otherwise, if the menu command is Turn Off Pop-Up Blocker, you’re already set.
When set in action, the pop-up blocker suppresses almost any pop-up display window. That means you miss out on all those ads! Yep.
When IE blocks a pop-up window, a warning banner is displayed just above the part of the window where you view the Web page. The banner reads “Pop-up blocked. To see this pop-up or additional options, click here.” Clicking the banner displays a menu of options.
Blocking pop-up windows may disable certain Web page features, such as a pop-up video window, a menu, or another informative display. In those cases, it’s obviously okay to allow pop-ups for that window or Web page: Click the warning banner and choose Temporarily Allow Pop-Ups from the menu.
The pop-up blocker doesn’t work to block certain animated pop-up windows. So if you see that the pop-up blocker is on yet pop-up windows still appear, just accept that, lamentably, there’s nothing you can do about it.
Phighting phishing
The phishing scam effectively fools you into doing something you would never otherwise do. The Web page looks legitimate, but it isn’t. Internet Explorer automatically helps you fight this kind of scam. Confirm that everything is set up properly by following these steps:
1. Click the Safety button on the toolbar.
2. Choose the In Private Filtering Settings command.
3. Click the big button, Block for Me.
If you don’t see the big Block for Me button, In Private Filtering is on and instead you see a summary of how things are working; click the OK button.
In Private Filtering alerts you to any Web page link that, well, appears to be fishy. The link may claim that it goes to one Web page when in fact it goes to another. Or, the link may go to a Web site known for doing naughty things with people’s personal information. Either way, you’re warned.
Don’t lower your guard just because Internet Explorer features In Private Filtering: It’s human engineering that the bad guys count on to make their scams work. No financial institution sends vital information by e-mail. None of them! When in doubt, phone your banker and confirm the message. Oftentimes, you discover that the message is bogus. Even if it shouldn’t be, it’s better to be safe than to be violated by a crook.
The Action Center
The headquarters for security issues in Windows 7 is the Action Center, illustrated in Figure 19-1. The Action Center window provides a quick summary of your PC’s current security state and lists any pending problems or issues with links or buttons that help you resolve those issues.
To open the Action Center, click the link Review Your Computer’s Status, found beneath the System and Security heading in the Control Panel window. High-priority items are flagged in red in the window, and lower priority items are flagged in orange.
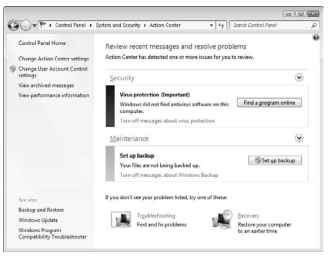
Figure 19-1:
The Action Center.
![]()
Click the Show More button in the window to view all the details for your PC’s security and maintenance conditions. When an area is expanded, you see lots of status information and updates plus links that take you to specific locations in Windows where you can change settings or deal with issues.
Generally speaking, follow the advice in the window.
In Figure 19-1, the PC is lacking antivirus protection. To solve that issue, click the button Find a Program Online; see the section “Antivirus protection,” later in this chapter.
Also in Figure 19-1, the PC hasn’t yet had its important files backed up. See Chapter 22 for information on PC backup.
In Windows Vista, the Action Center is named Windows Security Center. It serves the same purpose but lacks a lot of the detail of the Action Center.
Windows Firewall
In construction, a firewall is used to slow the advance of a fire. It’s created from special slow-burning material and rated in hours. For example, a three-hour firewall takes, theoretically, three hours to burn through — and that helps protect a building from burning down before the fire department shows up.
On a computer with an Internet connection, a firewall is designed to restrict Internet access, primarily to keep unwanted guests from getting in — or out of the computer. The firewall effectively plugs holes left open when the Internet was originally designed.
Windows comes with a firewall named, coincidentally, Windows Firewall. You start it from the Control Panel: Click the heading System and Security, and then click the heading Windows Firewall. The Windows Firewall window appears, shown in Figure 19-2.
As far as you’re concerned, Windows Firewall has only two settings: On and Off. To change the setting, click the link Turn Windows Firewall On or Off on the left side of the Windows Firewall window (refer to Figure 19-2).
When the firewall detects unwanted access, either to or from the Internet, you see a pop-up window alerting you to the intrusion, such as the one shown in Figure 19-3. At that point, you can choose to allow access by the named program by clicking the Allow Access button. If you want to continue blocking the program, just click Cancel.
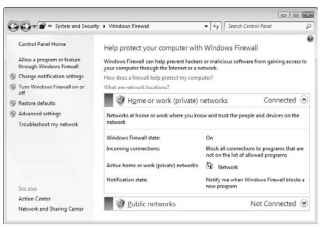
Figure 19-2:
The Windows Firewall window.
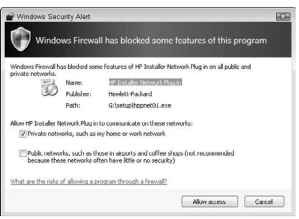
Figure 19-3:
Windows Firewall in action.
If you’re in doubt about your PC’s firewall or just want to ensure that it’s doing its job, I recommend that you give it a test. Many programs available on the Internet probe your PC’s firewall and look for weaknesses. One such program is Shields UP!, which can be found on the Gibson Research Web site:
http://grc.com
Windows Defender
Windows Defender is a single name given to a slate of tools used to protect your PC from snooping programs as well as from irritating startup programs. At its core, however, Windows Defender scans your PC for nasty programs known as spyware.
In Windows 7, the Windows Defender program runs automatically. You’re alerted to any problems in the Action Center window (refer to Figure 19-1). To specifically visit the Windows Defender program window, you follow a set of tricky steps:
1. Pop up the Start button menu.
Click the Start button or press the Win key on the keyboard.
2. In the Search box, at the bottom of the menu, type Windows Defender.
3. Choose Windows Defender from the search results list that’s displayed.
Just press the Enter key to open the window.
The Windows Defender main window is rather boring — well, unless you have a problem. Otherwise, it just lists a quick summary saying that your PC is running normally. You can close the window.
Other anti-spyware programs are available, and most often they can be found in the various security suite programs.
It’s okay to run more than one anti-spyware program in your computer at a time. Well, I’d run two, if you have them: another program plus Windows Defender. There’s no need to load up on anti-spyware programs.
For more information on using Windows Defender, refer to my topic Troubleshooting Your PC For topic
or my more comprehensive title Troubleshooting & Maintaining Your PC All-In-One For topic, both published by .
Antivirus protection
Windows doesn’t come with an antivirus program, though you may have such a program installed on your computer. Manufacturers include Norton AntiVirus, McAfee VirusScan, and, often, the AVG program. All of them work. You need to use one.
If your PC doesn’t yet have antivirus software, you can click the button Find a Program Online, found in the Action Center window (refer to Figure 19-1). Clicking that button takes you to a Web page where you can pick and choose an antivirus program, by downloading it directly to your computer over the Internet.
After the antivirus program is installed, it works by scanning your computer for signs of infection. The program has two modes of operation:
Active Scan: In Active Scan mode, your antivirus software takes a look at every dang doodle file and program on your computer, looking for viral presence. Antivirus programs scan all the files on your PC regularly, if not daily.
Interception: In Interception mode, the antivirus program works to scan incoming e-mail and files you transfer from other computers as well as stuff that floats in from the Internet. If an infection tries to walk into your PC, it’s stopped.
These names, Active Scan and Interception, are my own. The antivirus program you choose probably has its own pet names but still carries out those actions.
When the antivirus program alerts you to an infection, deal with it! Quarantine or delete the infection immediately.
Antivirus programs use quarantine as a way to isolate potentially infected files, preventing them from attacking your PC. Though the file has been quarantined, it hasn’t been deleted, but your system is still safe. (You can delete the quarantined files later.)
You can run two antivirus programs on your PC, though not at the same time. You use only one antivirus program in Interception mode, but you can scan your PC using two antivirus programs, one after the other, to ensure that whatever one misses, the other might catch.
You can access the antivirus program by clicking its little icon, which appears in the taskbar’s notification area.
See Chapter 18 for more information on downloading software from the Internet.
Viruses spread because of simple human engineering. Most folks know not to open strange or unexpected e-mail attachments. Yet viruses continue to be spread by these types of techniques. Perhaps the best anti-virus tool you have is your own brain: Being thoughtful and not careless prevents viruses from being installed in the first place, making antivirus programs necessary but not vital.
User Account Control Warnings
In its efforts to make Windows a more secure operating system, Microsoft has presented you (the user) with something called the User Account Control, or UAC. It displays various warning dialog boxes and pop-up windows whenever you attempt to change something in Windows, such as a computer setting or option, or when you try to download software from the Internet. A typical UAC is shown in Figure 19-4.
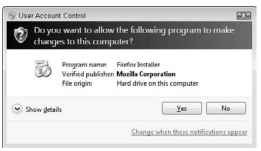
Figure 19-4:
A typical UAC.
![]()
The UACs are to be expected whenever you see a link or button flagged with the UAC shield icon, shown in the margin. It’s your clue that you should expect a UAC warning to appear. If the action is expected, click the Continue button or, if prompted, type the administrator’s password and then click the OK button.
If you see a UAC warning when you’re not expecting one, click the Cancel button. For example, when you’re on the Internet and you see a UAC warning about installing software or changing your home page, click Cancel!
