In today’s business environment it has become necessary to track computer assets—both hardware and software—to determine the cost of ownership and depreciation, and aid departmental budgeting and theft deterrence. A key aspect of asset management is applications metering, which entails monitoring how many copies of a particular software program are in use at any given time. Not only is software usually the most expensive asset, but it often determines how much an organization spends in other areas, such as hardware, staff training, and support. Several compelling reasons why small and large organizations should monitor software usage is that is allows them to:
■ Minimize software costs by not overspending for software licenses and upgrades.
■ Eliminate exposure to litigation and financial penalties by ensuring compliance with vendor licensing agreements.
■ Identify patterns of usage that can aid in capacity planning, training, and budgeting.
■ Limit the amount of time personnel are engaged in using nonessential applications.
■ Minimize exposure to viruses and other hostile code that may be lurking in bootleg copies.
Applications metering tools are available as stand-alone products, such as CentaMeter from Tally Systems Corp., or they may be embedded in a larger systems management package, such as Intel’s LANDesk or Microsoft’s SMS. All provide scanning capabilities and management reports of varying degrees of flexibility and detail. Other related functions may be included in these tools such as automated software distribution and installation.
Operation
Monitoring software allows IT administrators to control the number of people concurrently using stand-alone applications as well as those in a software suite. In the case of a software suite, the metering software tracks each application in the suite individually to automatically allow the correct number of concurrent users, per the vendor’s license agreement. In addition, information is provided on which applications have been used, for how long, and by which users.
The metering software automatically tracks which applications are being used on each system on the network by scanning local hard drives and file servers for all installed software. The executable files of each application are examined to determine the product name. Files that cannot be readily identified are listed as found, but flagged as unidentified. Once the file is eventually identified, the administrator can supply the missing information.
Each application in the software inventory is automatically assigned a unique name or tag, which is used for metering. When a user launches a metered application, the tag is checked to determine if there are available copies (licenses). When a user starts an application, one less copy is available to run. Likewise, when the application is closed, the copy becomes available again. Before users are granted access to an application, the software inventory is checked to determine whether or not there are copies available. If all copies are being used, a status message is issued to the requesting user, indicating that there are no copies available. The user can then decide to wait in queue for the next available copy or try again later.
Functionality
The IT administrator can choose to be notified when users are denied access to particular applications because all available copies are in use. If this happens frequently, it may help justify the need to purchase additional copies of the software or pay an additional license charge to the vendor so more users can access the application.
Some software metering packages allow application usage to be tracked by department, project, workgroup, and individual for charge-back purposes. Charges can be assigned on the basis of general network use, such as time spent logged on to the network or disk space consumed. Reports and graphs of workgroup or department charges can be printed out or exported to other programs, such as an accounting application. Even if workgroups and departments are not actually required to pay for application or network usage, the charge-back feature can still be a valuable tool for identifying operations costs and for budget planning.
Metering software can also be used for capacity planning. For example, if a company has accounting software running on six different servers, it might want to consolidate applications on fewer servers. To do this properly, the company needs to know which servers are being accessed the most and from which locations. With this information, the company can decide which servers can safely handle the redistributed load without imposing undue performance penalties on frequent users.
Another function performed by some metering products is automated software distribution. After a software inventory is compiled, this information can be used to create a software distribution list that includes workstation addresses. When an upgrade or patch becomes available from the vendor, the IT administrator can send it to all the workstations appearing on the distribution list.
Some metering products not only automate software distribution, but they also facilitate remote installation by allowing administrators to add conditional logic to customize mass installations across a network. Ordinarily, it would take considerable effort for an administrator to develop a script for automating software installations because he or she would first have to anticipate all the changes an application makes when it is installed. With the right installation package, however, the administrator can concentrate on adding the customization logic and let the installation com-ponent of the metering software figure out the hundreds of files that are changed by an individual installation.
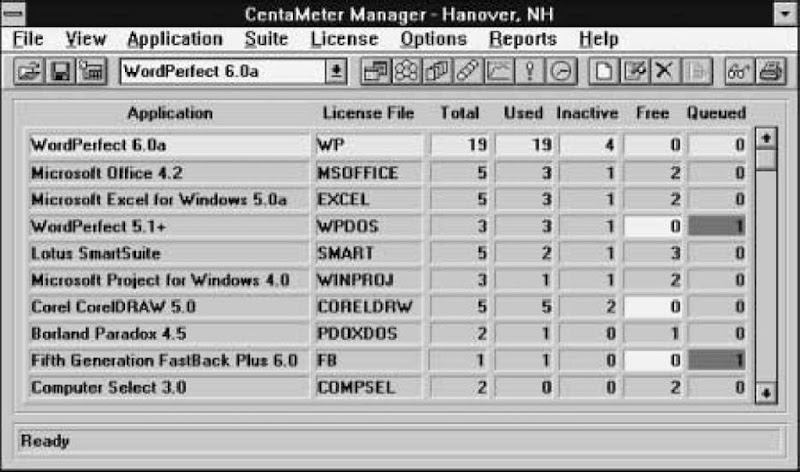
Figure 4
View of license usage by application from Tally Systems’ CentaMeter.
License Tracking
In monitoring the usage status of all software on the network, each application can be identified by total licenses, licenses used, licenses inactive, licenses free, and users queued for the next available copy (Figure 4). This and other information is used to monitor software license compliance and optimize software usage for both network and locally installed software packages. Some products, including CentaMeter from Tally Systems, even provide an analysis of software usage by time of day (Figure 5).
Microsoft’s SMS 2.0 is among the systems management products that features dynamic license sharing across servers and domains. SMS also has extensive license metering capabilities, letting users with laptop computers check out licenses, providing pools of licenses or static licensing, and supporting accounting for charge-back on application usage. SMS can also search for unsupported applications on the network and report their existence to the administrator, or even disable them so they cannot be run. It also has tamper-resistant features that report when a malicious user attempts to disable client software or rename applications.
Features
Some software metering products issue a warning if the limit on the number of legal copies in use has been exceeded. Depending on the prod-uct, the tracking program may even specify the directories where these files were found. This saves the IT administrator from having to track down any illegal copies and delete them. Some of the advanced features of today’s software metering products include:
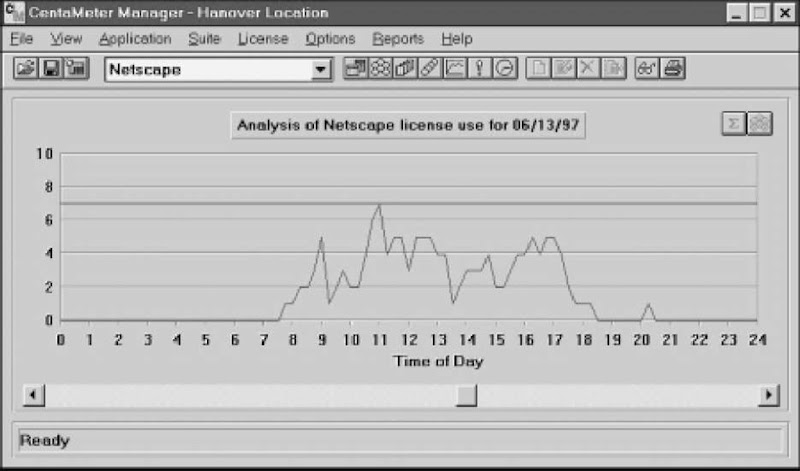
Figure 5
Tally Systems’ CentaMeter Manager provides a visual indication of software usage by time of day. In this analysis of Netscape browser usage, for example, the peak hour was 11:00 A.M., when seven of the ten browser licenses were in use at the same time.
CUSTOM SUITE METERING WITH OPTIMIZATION CAPABILITY Allows the administrator to monitor the distribution of software suites in compliance with license agreements. This ensures that a suite will never be broken up illegally. The metering software automatically monitors the usage of individual components by end users and switches whole suite licenses to users working with more than one suite application at a time, leaving stand-alone licenses available whenever possible. With the optimization capability single and suite licenses are used efficiently and legally—automatically.
INTERACTIVITY TRACKING AND REMINDERS Allows the administrator to track the amount of time open applications are inactive and reminds users to close inactive applications to make those resources available to others.
LICENSE ALLOCATION Allows the administrator to allocate licenses to an individual, group, machine, or any combination of these. Access to applications is given on a priority basis to users who need it most. Overflow pool licenses can be created for common access.
PRIORITY QUEUING Gives users the option of joining a queue when all eligible licenses for an application are in use. Different queuing arrangements and access limits can be implemented for each application. High-priority users can jump ahead in the queue, while VIPs can get immediate access to an application regardless of license count restrictions.
POINT-OF-EXECUTION METERING Allows tracking of applications, regardless of where they are executed—even on a local disk drive where users think they have privacy and can get away with ignoring company policy. Unauthorized programs can be shut down wherever they reside—even for VIP users.
LICENSE SHARING ACROSS LOCALLY CONNECTED SERVERS The metering software can be installed on any server for tracking applications across multiple servers. Access to licenses for a product installed on more than one server can be pooled together.
ENTERPRISE MANAGEMENT CAPABILITIES Allows licenses for applications to be transferred to remote locations across WAN connections, facilitating configuration changes and organizational moves.
LOCAL APPLICATION METERING Tracks software usage and restricts access to unauthorized applications installed on local hard drives.
UNREGISTERED APPLICATIONS LOGGING An IT administrator can log all executions of local applications that do not have defined license profiles. For example, this feature can be helpful for learning what downloads are being used and who may be using unregistered software on a network, further preventing software piracy and the spread of harmful viruses.
ENHANCED APPLICATION IDENTIFICATION Allows the administrator to use a variety of categories to identify an application for metering, including filename, size, date, drive and path, or any combination of these.
DYNAMIC REALLOCATION OF LICENSES Allows the administrator to transfer licenses between groups and users to accommodate special access needs.
FILES-TRACKED METERING This is a relatively new feature, offered by Tally Systems, in which storage hierarchy decisions are made based on which files are frequently and infrequently used. An infrequently used file might be archived to tape, for example, while a frequently used file would stay on a local hard disk. Files can be tracked by any extension and reports are generated on usage. This feature can save money by minimizing the need for more disk drives or other types of online storage.
Reports
Application use can be metered on a global basis or selectively according to such parameters as users, workgroups, workstations, hardware configuration, and networks. The information gathered by the monitoring software can be reported in a variety of ways, including:
GRAPHS A graph is created daily for each application, showing peak usage over a 24-hour day. Administrators can also view usage by group or user, as well as queuing patterns over time.
ERROR REPORT An error report describes users who have been denied access to an application, attempted unauthorized access, or restarted their applications in mid-operation.
COLOR-CODED STATUS SCREEN A single screen displays the ongoing status of each metered application, and administrators may select different colors to indicate that a license limit has been reached or that users are in the queue.
COLOR-CODED USER SCREEN Displays which users are active and which are inactive on any application.
E-MAIL ALERTS Messages can be sent via any mail application to a designated address when an unauthorized user attempts to access an application, when a user has been denied access to an application, or when license limits have been exceeded.
PAGER ALERTS Messages that are deemed crucial by the administrator can be sent to a pager so immediate action can be taken. For example, a pager alert can be sent whenever unauthorized software has been installed on a workstation. Since this can cause problems on the network, as well as unwanted legal trouble, immediate notification by pager allows the offending user to be tracked down as soon as possible.
Vendors provide different kinds of reports. The standard usage report calculates the number of users that have started applications during a specified time period. Another type of report shows peak usage over a 24-hour period. There is even a report that shows all unmetered applications that are running on the network. Examples of unmetered applications are freeware and beta programs, demo software, and internally developed applications.
A license report offers an enterprise-wide view of license usage by calculating usage for each application by location in order to determine whether more or less licenses should be allocated. This also helps determine how software-license load should be balanced among servers. There are also reports that provide historical data on such events as total number of executions, total time the application has been in use, and the total number of reject/queue occurrences.
Some vendors include a built-in report writer in their monitoring products to help the administrator summarize historical data. Seagate Software, for example, provides trending reports through its Crystal Reports engine, an application that is included as part of its Desktop Management Suite.
More than 15 types of reports can be generated, including one that shows compliance with Microsoft’s Select Agreement. Hewlett-Packard includes a copy of the Crystal Reports engine in its Desktop Administrator.
Global Licensing
A global license is created by defining the total number of purchased licenses for any given product. The monitoring software keeps track of user demands for each application and will automatically move unused licenses from a server with excess counts to a server in need of a license. When a global license is defined, one server is designated as the dispatcher for that license.
In the case of Elron Software’s SofTrack, for example, messages between servers keep each other informed of user demand for various applications. If a server on the network runs out of licenses for a particular application, it will request one from the dispatch server. The dispatch server, in turn, will borrow a license from the server with the most available licenses. The communication continues so the server in need of a license borrows it, and the maximum concurrent user counts for that application are automatically updated on each server. From the user’s perspective, it looks as if he or she is just waiting in queue for the next available license.
SofTrack is also useful for organizations that are in the process of migrating their networks from NetWare to Windows NT. In addition to running over TCP/IP and IPX nets, it provides concurrent global license sharing between the two types of servers under central administration. This gives organizations the ability to share licenses between different server platforms to ensure license compliance and maximize license availability, while allowing them to migrate at their own pace.
Another product that spans multiple operating environments and also works over TCP/IP networks is KeyServer from Sassafras Software. The license metering tool can run on a Windows NT/Windows 95 computer or a Macintosh/Power Macintosh computer. Regardless of which platform and operating system is actually running KeyServer, its license management services can support thousands of clients on both platforms with negligible traffic overhead. Using a common console from the Windows or Macintosh platform, all of KeyServer’s features can be configured locally or remotely, enabling global administration via a corporate intranet or the Internet (Figure 6).
A key advantage of products that work over WANs is that the IT administrator can distribute and meter software to remote IP servers that are not part of the local network. Depending on the specific product, software usage can be monitored and controlled across file servers for Windows, OS/2, UNIX, and Macintosh clients.
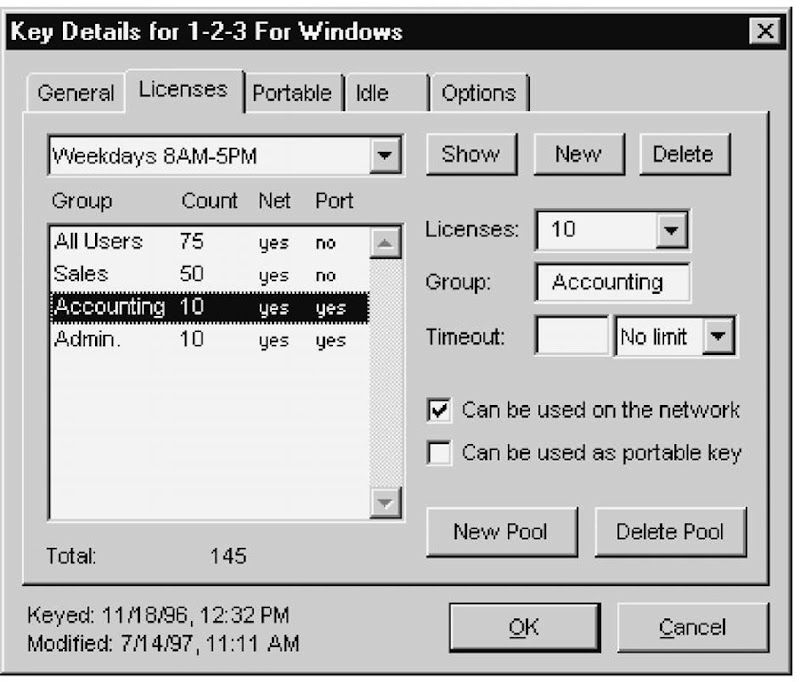
Figure 6
Using the Key Details window in Sassafras Software’ KeyServer, the IT administrator can set up permissions for multiple groups of users via TCP/IP nets.
The IT administrator can tag applications or suites for metering and can set several properties, such as maximum concurrent users, rules for license-borrowing between servers, program files to meter, and the amount of time a user waits in a queue. With the ability to monitor all the me-tered servers in the enterprise and print comprehensive reports, the IT administrator is saved the time-consuming chore of collating reports from many different locations.
License Registration Standard
Most legitimate computer software use is regulated by an explicit license. The license typically states who may use the software and under what conditions. There are many different types of licenses, each of which reflects the intended use of the software.
Until a few years ago, software use licenses were often nothing more than a printed license statement included in the product’s packaging.
Software vendors relied on the integrity of their customers to not violate the license; in many cases, this was sufficient to protect the vendor’s investment in developing the software. However, in an attempt to further reduce losses that result from illegal software distribution and use, a group of software companies cooperated in developing the Licensing Service Application Programming Interface (LSAPI).
The LSAPI specification was developed in 1994 by a consortium of vendors including Sassafras, Microsoft, Novell, Apple, and DEC to provide a common programming interface to licensing services while hiding the underlying details. LSAPI lets supporting software products monitor and control the number of application instances concurrently in use. Through the LSAPI, an application can register itself with a license server. When run on a workstation, the application asks the license server if the license agreement recorded in the license server permits another instance of the application to run.
Legal Ramifications
Another use of metering software is for auditing purposes. It lets companies know if more copies of programs are being used than were paid for under each vendor’s licensing agreement. An audit can also spot software that has been installed by individual users without company authorization, but for which the company is ultimately responsible.
The ability to identify and locate unauthorized software is important because it is a felony under U S federal law to copy and use (or sell) software. Companies found guilty of copyright infringements face financial penalties of up to $100,000 per violation.
The two leading trade associations of the software industry are the Software Publisher’s Association (SPA) and the Business Software Alliance (BSA). Both organizations run antipiracy campaigns and provide opportunities for whistleblowers to report software piracy through toll-free numbers and forms posted on their Web pages.
Software piracy is actually commonplace among businesses. In a 1997 study of global software piracy jointly sponsored by the SPA and BSA, it was estimated that of the 523 million new business software applications used globally during 1996, 225 million units—nearly half—were pirated. This figure represented a 20-percent increase in the number of units pirated in 1995. Although revenue losses in the worldwide software industry due to piracy were estimated at $11.2 billion in 1996, a 16- percent decrease over the estimated losses of $13.3 billion in 1995, the decline was attributed to lower software prices rather than a decrease in piracy.
The 1200-member SPA represents companies that develop and publish software applications and tools for use on the desktop, client/server networks, and the Internet. The SPA claims to receive about 40 calls a day from whistleblowers over its toll-free hotline. It sponsors an average of 250 lawsuits a year against companies suspected of software copyright violations. Since 1988, every case the SPA has been involved in has been settled successfully.
The BSA is another organization that fights software piracy. Its membership includes leading publishers of software for personal computers, such as Adobe Systems, Lotus Development, Microsoft, Novell, and Symantec. According to the BSA, software piracy cost U S businesses $6 million in fines and legal fees in 1997. In the U S alone, software piracy cost 130,000 jobs in 1996, and piracy is expected to cost another 300,000 jobs by 2005.
Both the SPA and BSA offer free audit tools that help IS managers find licensed and unlicensed software installed on computer systems. BSA offers Softscan for Windows and MacScan for Macintosh. SPA offers SPAudit by McAfee (now part of Network Associates, Inc.) and KeyAudit by Sassafras Software. SPAudit does hardware and software audits on both network and stand-alone Windows NT and NetWare machines using a catalog to identify over 4,400 software applications. KeyAudit works on Macintosh machines.
One of the most comprehensive and accurate audit tools available is GASP from Attest Systems. This is the tool that SPA, BSA, Microsoft, and other software companies use for conducting enforcement audits worldwide. Its database of applications exceeds 7,000 and is user-expandable. Most audits are completed in less than two minutes. GASP comes in two versions: GASP Net is compatible with Windows NT, SMS, NetWare, Vines, and other network operating systems, and GASP Audit is compatible with Windows NT, Windows 95, Windows 3.x, DOS, and Macintosh.
Last Word
When software metering arrived on the scene, it was primarily used to prevent the unauthorized use of software and manage concurrent-use software licenses. Today, information—not control—is the primary use of software license metering programs. Knowing what users are doing at their desktops promotes effective asset management. Specifically, the focus is on reporting actual usage, trends in usage site to site, what software packages are being used effectively, and what ones are not being used at all.
Gathering all license usage information in one place allows companies to see the big picture and use the information for decision support. Among other things, this can save money on software, support, and training. It can also aid capacity planning and budget development. The use of asset management information as decision support criteria is a trend that will likely continue. See Also Asset Management