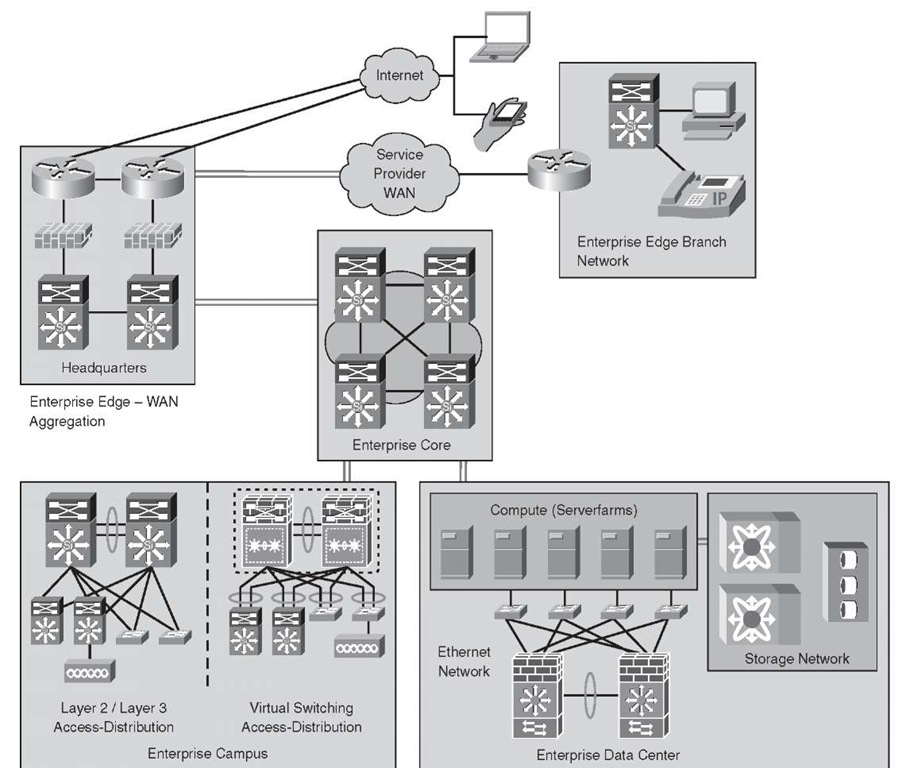
The enterprise edge module includes the Internet, Virtual Private Network (VPN), and WAN modules that connect the enterprise to a service provider network. The enterprise edge contains all the network elements for efficient and secure communication between the enterprise campus, data center and remote locations, business partners, mobile users, and the Internet. The edge module aggregates the connectivity from various remote sites, filters traffic, and routes the traffic into the enterprise. The modular design of the edge network enables flexibility and customization to meet the needs of different-size customers and their respective business models. The edge network for an enterprise has three key network areas:
■ The corporate headquarters, which is commonly known as the WAN aggregation network
■ The branch side to connect to the WAN aggregation network
■ The area facing the Internet, which serves both remote VPN and regular Internet access
Figure 2-10 illustrates the relationship between different enterprise edge network modules.
Figure 2-10 Enterprise Edge Design
Each module shown in Figure 2-10 has distinct network components and services that fill specific roles. The common components found in the headquarters enterprise edge module are introduced in the following section.
Headquarters Enterprise Edge Network Components
Within the enterprise edge, there are commonly deployed network components that offer distinct functionality. Depending on the size and complexity of the network, these components can be high performing, highly available, and scalable, and offer comprehensive features and security, or they can be consolidated and somewhat minimalistic in function. The enterprise edge network commonly includes infrastructure components as shown in Table 2-5.
Table 2-5 Enterprise Edge Network Components
|
Network Infrastructure |
Functionality |
|
Edge router |
Basic WAN/Internet connectivity to the service provider. Serves as the first line of protection against spoofing and other network attacks. Collection point for network flow and event information useful for analysis and correlation purposes. Redundancy is achieved by deploying two or more routers and by configuring a First Hop Redundancy Protocol (FHRP). |
|
Outer switch |
Provides Layer 2 or Layer 3 connectivity between the firewalls and the edge routers. Two switches are deployed for redundancy. The outer switches provide connectivity to the distributed denial of service (DDoS) mitigation component. |
|
Firewall |
Secures the demilitarized zone (DMZ) and WAN aggregation modules by controlling and inspecting all traffic entering and leaving those modules. For redundancy, firewalls are deployed in stateful active/standby failover mode. |
|
Additional security |
Implements an intrusion detection system (IDS) with the intent to identify and alert on well-known attacks and suspicious activity. Alerts and alarms generated by the IDS and the endpoint security software are processed by a monitoring and analysis system for analysis and correlation purposes. Identifies DDoS and other network-based attacks, and works with the DDoS mitigation system deployed at the outer switches. |
Headquarters Enterprise Edge Network Design
The enterprise edge network infrastructure provides a common infrastructure to enable branch connectivity, Internet connectivity, teleworker connectivity, and communication channels to partners (extranets), thereby reducing capital expenditure and operational expenses. Table 2-6 outlines the design requirements for the edge infrastructure.
Branch Network Architecture
The previous section outlined the network architecture and design considerations for the enterprise edge network at the headquarters site. This section outlines the design components of the edge network in each remote office or branch office for an enterprise. One of the main goals for the branch network architecture is to provide a flexible, scalable, reliable, and secure network infrastructure.
Table 2-6 Headquarter Enterprise Edge Design Requirements
|
Design Requirements |
Features |
|
Network resiliency |
The edge design needs to ensure that there is no single point of failure, thereby maximizing the availability of the network infrastructure. Any downtime of the edge network can result in bringing down access to data center resources (intranet and extranet resources) and the communication partner channels, contributing to loss of business. The edge design is built out of many platforms and components that can fail or that can be subject to attack. Hence, it is critical to eliminate single points of failure by deploying several layers of redundancy, including redundant interfaces, standby devices, and topological redundancy |
|
Regulatory compliance |
The edge design needs to meet regulatory compliance for standards: Payment Card Industry Data Security Standard (PCI DSS) for the payment card industry. Health Insurance Portability and Accountability Act (HIPAA) for the healthcare industry. Any noncompliance can lead to the revocation of licenses, stiff penalties, and even legal actions. |
|
Modularity and flexibility |
The modular design provides a clear demarcation between the network and the services offered for Internet versus branch offices. The design flexibility helps add services (IPsec and WAN optimization services) without impacting the existing design. |
|
Pervasive security |
The edge network needs to ensure confidentiality, integrity, and availability of applications, endpoints, and the network. |
The branch network architecture has the following key components:
■ Edge routers: The edge routers (also known as access routers or just branch routers) are the gateways to enable connectivity between the branch network and head-end enterprise edge network. These routers provide connectivity through one or more WAN or Internet service providers (ISP). These key features are enabled on the edge routers to gain visibility on traffic flows, network activity, and system status: QoS, rate limiting, security (ACLs and uRPF), NetFlow, and SNMP. These routers can have built-in firewalling or can connect to dedicated firewalls to protect branch assets from the external world and to provide a secure communication channel between each branch and the head-end enterprise edge network.
■ Inner switches: These switches provide connectivity from the edge routers to the remainder of the branch LAN. Smaller branches can have just a few Layer 2 switches connecting to the edge routers. Larger branches can have the same basic design as a larger campus network deployment using the traditional core, distribution, and access layers.
Branch Edge Router Functionality
The branch edge router provides network connectivity between the remote offices and the head-end enterprise edge. Along with basic network connectivity, it also provides firewall and application intelligence services required for a secure and optimized communication channel between the remote sites. The key branch edge router services include
■ Optimized application delivery through quality of service (QoS), integrated flow monitoring (NetFlow), and application acceleration (Cisco Wide Area Application Services [WAAS])
■ Security, including platform, WAN, and VPN (includes Secure VPN authentication using public-key infrastructure [PKI])
The edge router infrastructure is the foundation upon which the rest of the branch network and advanced services are built. Flexibility and scalability are the two key design requirements for network infrastructure. You need to design a flexible network infrastructure so that advanced network services can be efficiently and seamlessly integrated. You also need to design a scalable network infrastructure so that you can easily add more capacity or more branch sites without disrupting the existing network operations.
The branch edge solution is designed with respect to different requirements such as size, business vertical, location, cost, and so on. The branch design introduces the concept of three profiles: single-tier branch, dual-tier branch, and multitier branch.
Table 2-8 Branch Design Profiles
|
Branch Design Profiles |
Design Considerations |
|
Single-tier branch |
The single-tier branch solution consists of a fully integrated, one-box solution. This one device is responsible for LAN and WAN connectivity. This profile is generally deployed where enterprise branches do not require platform redundancy. User capacity is typically between 20 and 30 users in a remote branch office. |
|
Dual-tier branch |
The dual-tier branch solution provides a two-layer architecture. The first layer provides dual redundant WAN capabilities, and the second layer provides LAN connectivity. The dual WAN links provide higher availability as compared to the single-tier. A separate Ethernet switch would provide more LAN connections as compared to the single-tier. |
|
Multitier branch |
This profile separates network functionality into separate layers. The separate tiers are WAN termination, firewall functionality, services termination, and LAN termination. The significant benefits of this profile are redundancy, availability, and router/switch CPU utilization. |
Typical Branch Network Design
Depending on the size of the branch, each branch office would require an external connectivity: up to 1.5 Mbps for small branch offices (up to 100 users) or high-speed (up to 45 Mbps) for larger branches. In some designs, enterprises can use traditional private WAN technologies such as MPLS or Frame Relay, or they can leverage the Internet to connect remote sites using VPN technologies. The branch router hosts the following integrated services:
■ Security services: Security services such as firewalls and IPsec are either integrated or implemented in a separate appliance depending on the amount of traffic that exits at the branch. Integrated modules inside the edge router can provide services, or a dedicated, standalone device such as a Cisco ASA Firewall can be used.
■ Unified Communications services: These services include local call control, FXO/FXS ports for direct public switched telephone network (PSTN) connectivity (emergency 911), and backup connectivity
■ Application intelligence services: One of the key design objectives for the branch solution is to provide branch network users with the same network capabilities and service levels as corporate users. This can be challenging because of the limited bandwidth and inherent delay in WAN links. The typical small branch, which has limited WAN bandwidth, can benefit greatly from application intelligence services, such as WAN optimization/application acceleration using the Cisco WAAS.
The branch also includes a Layer 2 access switch with the following key features:
■ Power over Ethernet (PoE)
■ Spanning Tree
■ Class of service (CoS) on access ports and QoS policing and shaping on edge routers
Additionally, some branch sites can have localized infrastructure services such as a local Microsoft Active Directory server, local DNS, and local DHCP. As it relates to IPv6, the branch edge router can be configured to provide local addressing the Cisco IOS DHCPv6 server or be configured to provide DHCPv6 Relay to forward local DHCP requests to the corporate headquarters site.
Most enterprises find that the enterprise edge design that they use today with IPv4 will most likely be the same design that they use with IPv6.
Summary
The topic provides a basic overview of a hierarchical enterprise network design. It begins by discussing the three key design principles: modularity, hierarchy, and resiliency. This topic begins by comparing the flat network designs and the need for hierarchical modular network designs. As networks grew in size and applications’ demand for network bandwidth and services grew, new designs for the network were needed.
The network design principle concepts help segment the enterprise network into simpler, multiple building blocks based on the functionality that each module provides. The topic also summarizes some of the design considerations for each of these building blocks, enabling a network designer and/or architect to review the various design options and extend these design principles in his or her own enterprise network designs.
The enterprise campus section provides connectivity to end users and devices and then introduces and compares the various access-distribution block designs: Layer 2 access (looped or loop-free access design), routed access, and Virtual Switching System distribution block.
The network services block is a new concept that enables network architects to reduce the scope of running tunnels between multiple endpoints required during the transition from IPv4 designs to dual-stack IPv4/IPv6 designs.
The enterprise data center section covers the network design for providing IP connectivity to server farms and the storage network. The SAN design was also reviewed. Although the SAN is agnostic to IPv6, the section brought out the importance of a SAN in an enterprise network and different topologies in a SAN.
The enterprise edge design focuses on how remote locations and teleworkers connect to the enterprise network and discusses some high-level concepts for Internet connectivity. You also reviewed features and security requirements required in a WAN/branch network design.