Mail and Recipient Content
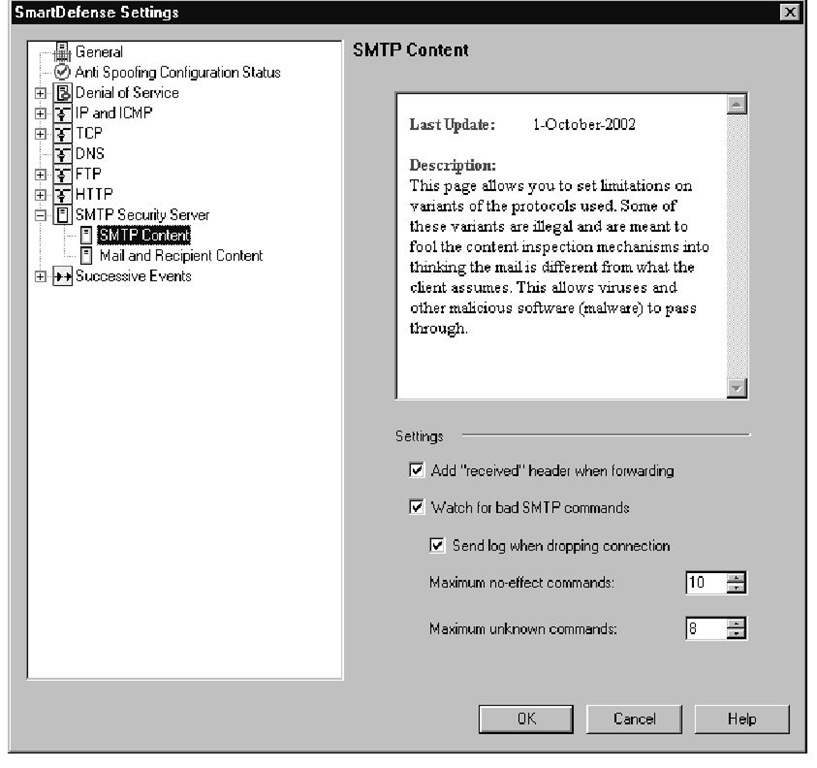
This SMTP category focuses on scanning the data that is passed in an e-mail, specifically the Multipurpose Internet Mail Extensions (MIME) information that is used to identify the accompanying data in the e-mail message. When an e-mail message is created, MIME information is placed in the e-mail header to describe to the recipient how to interpret the data that follows. One of the MIME headers used is content-type, which specifies what sort of data follows, such as text/plain or text/html. When there are multiple types of data being sent in a single message, such as an HTML e-mail with a Word document attached, then the content-type is set to "multipart." Multipart indicates to the receiver to expect multiple MIME sections, or parts, each with their own set of headers describing each chunk of data.Another header called "content-transfer-encoding" is used to describe what encoding method has been used on the attached data, such as 7bit, 8bit, and so on. 7bit and 8bit data must follow certain guidelines about how many octets per line, and what values are acceptable (CR and LF are not allowed). Binary can be specified as the encoding type when the data hasn’t actually been encoded.
Figure 11.21 SMTP Content
When an SMTP message is passed through the SMTP security server, it will scan the data for possible problems with the MIME headers in the message. One of the problems that can be detected is when multiple content-type headers are listed in the message. When there are multiple content-types listed, the receiving workstation has contradictory information it must deal with, and different programs will handle this exception in different ways. Another check that the SMTP security server performs is for multiple encoding headers, which can cause similar problems as with multiple content-type headers. This check will not block multipart messages, because they will have multiple content-types by definition. The difference is that there are boundary lines that separate each MIME part in the message. Each content-type header applies to a different MIME part, so there is no contradictory information.The problem occurs when there are multiple content-type or content-transfer-encoding headers that try to describe the same section of data.
Note
These settings will not apply if you have chosen to apply the security server to all SMTP connections passing through your firewall. For these settings to work, you must define and apply an SMTP resource to the traffic that you want scanned.
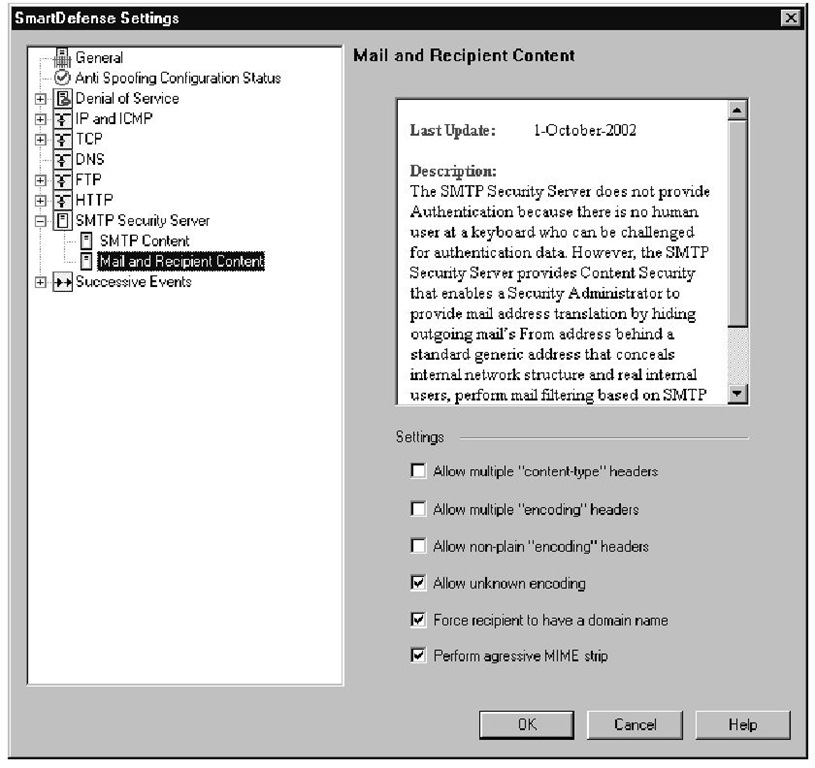
The Security Server also gives you the option of denying "non-plain" and unknown encoding types. A plain encoding method does not modify the data, but just describes how it is represented. Standard ASCII characters are represented by a 7-bit value, and extended ASCII characters are represented with 8-bit characters, so when 7bit or 8bit encoding is used, these characters are represented as themselves. Even encoding schemes such as Base64 can be considered plain, because this method takes a group of three 8-bit characters (24 bits) and separates it into four 6-bit pieces. Each 6-bit section is represented by a character, as described in RFC 1521. Even though this won’t be humanly readable, the data has not been modified as it would be if another process like compression was applied to the data before it was encoded.You can prevent more exotic encoding types by making sure that the Allow "non-plain" encoding types option is wnselected. Some of the encoding types that will pass through as "plain" encoding types are 7bit, 8bit, binary, Base64, and quoted-printable. As new encoding schemes are made available, the Security Server may not understand what the new encoding scheme is, and if you have your enforcement points configured to strip out unknown encoding types, these newer encoding formats will be dropped.You have the option of allowing or disallowing unknown encoding types.
The Force recipient to have a domain name option prevents mail from being delivered through the security server if the destination e-mail address doesn’t contain a domain name for the user.
The Perform aggressive MIME strip option defines how the security server will go about searching for and removing MIME headers. When this option is disabled, the security server will only look in the header area of each MIME part for information that needs to be stripped. If aggressive mode is enabled, the security server will search the entire body of the message for MIME information that should be removed.
Figure 11.22 shows the available options in the Mail and Recipient Content configuration window. As with the previous SMTP section, you can only log when the Security Server detects a suspicious transmission because the Action option is not available.
Figure 11.22 SMTP Mail and Recipient Content
Successive Events
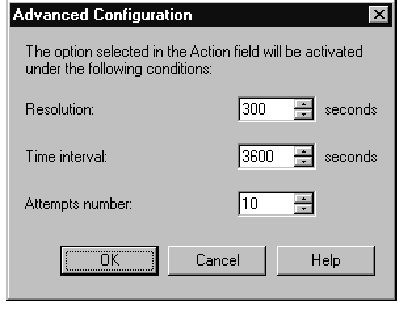
The Check Point Malicious Activity Detection (CPMAD) daemon was integrated with SmartDefense as the Successive Events tree. All of the options in this branch of the tree work by scanning the FW-1 logs for signs of suspicious activity, and they all have an Advanced configuration button, which lets you tweak the sensitivity of the alerts.This Advanced Configuration window is shown in Figure 11.23, and we cover these settings here because the window looks exactly the same for each subsection that will be described below.
Figure 11.23 Successive Events Advanced Configuration
Note
The Successive Events section scans the log entries for evidence of the attacks listed in the configuration tree. Packets that are dropped by the implicit deny at the end of the rule base will be logged. This means that if you have not configured an explicit drop rule that logs all packets that are denied, then most of these features will not report when an attack has occurred.
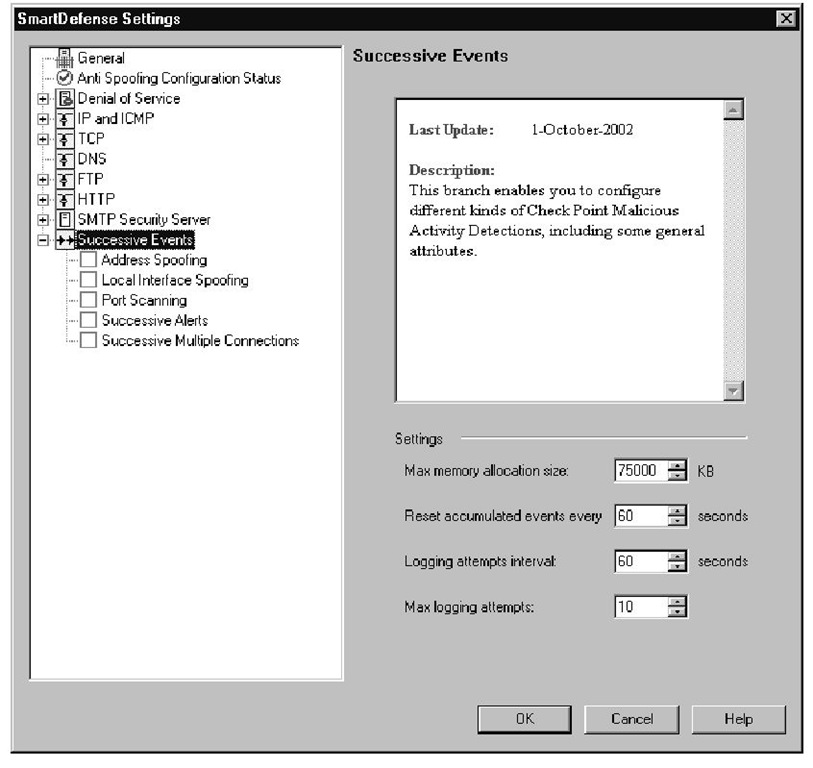
The main Successive Events category contains some options that apply to all sub-options in this category.These options define how much memory will be used for tracking events that show up in the logs.The options are as follows:
■ Max Memory allocation size This is the amount of memory that will be allocated to the Successive Events feature, for use in tracking log entries that are related to an attack.
■ Reset accumulated events every This is the number of seconds that each entry in the Successive Events table can live.This prevents the table from continuously growing by removing old entries that should no longer be taken into account.
■ Logging attempts interval This is the interval of time that log entries are counted.
■ Max logging attempts This is the number of times an entry has to occur before the action is taken.
Each option within the Successive Events category contains an Advanced button that lets you configure the sensitivity levels of each feature.This menu allows you to set a threshold by defining how many events in a certain time period will be considered an attack. Once the threshold is crossed, the selected action will be taken.
These options are also available under the advanced settings of the Denial of Service category, and are as follows:
■ Resolution This is the length of the interval that SmartDefense uses when tracking pertinent log entries. Check Point recommends the resolution to be one-tenth of the Time Interval option, and should never be set less than one-fifth.
■ Time Interval This is the length of time that log entries will be considered valid for an attack. If the Attempts Number of attacks is detected during this time period, the selected alert will be used.
■ Attempts Number The number of attacks that needs to be exceeded within the above time limit to signal an attack.
The following five subsections describe each option available under the Successive Events configuration tree, which is shown in Figure 11.24.
Address Spoofing
As was mentioned at the beginning of the topic, the Anti-Spoofing configuration section does not block any attacks by itself, nor does it even look for evidence of a spoofing attack. It only tells you which gateways are not configured for anti-spoofing protection. Once you have your gateways configured for anti-spoofing, this feature can be used to send alerts when spoofing attempts are detected. If this feature is enabled, it will scan the logs for drops due to the anti-spoofing protection. If the thresholds that are defined in the advanced configuration are exceeded, the selected alert will be sent.
Figure 11.24 Successive Events
Local Interface Spoofing
This section will look for packets that are sourced from local interfaces of your gateways. If packets are dropped because they contained spoofed addresses of the firewall interface, this feature will send an alert when the defined thresholds are crossed.
Port Scanning
An attacker will perform port scans on a server when he is trying to find out which ports are accepting connections. The easiest way to find out which ports are accepting connections is to initiate a connection to that port and see if he receives a response. If the server responds with a SYN/ACK, the attacker knows that the port is open and accepting connections. If a RST/ACK is returned, the attacker knows that the particular port is closed and the server is not accepting connections from that server. Finally, if no response is received from the SYN request, the attacker can assume that port is being filtered by a firewall because a firewall will just drop the packet instead of returning a response as the server will do. This is performed for every port that is being checked, and usually thousands of ports will be checked to determine which networked applications are running on a server.
Since a log entry will be generated for each SYN packet that is sent to a blocked port (assuming you have a cleanup rule that logs), SmartDefense can alert when port scans are being attempted because a large number of packets will be sent in a short period of time. A patient hacker will perform his port scan over a period of days, which will be not be detectable unless you have extremely sensitive thresholds defined, although this will also drastically increase your number of false positives.
Successive Alerts
Certain SmartDefense features can create an excessive amount of alerts when an attack is taking place, such as the HTTP worm catcher. Check Point designed Successive Alerts to give a single alert when these types of attacks take place. For example, you can set the original attack to send a pop-up alert when the offending packets are detected, but have Successive Alerts send an e-mail alert when a certain threshold of attacks are detected.
Successive Multiple Connections
This will scan the logs of an excessive number of connections to the same destination IP and port number within the configurable time limit. The advanced settings let you decide how sensitive this log scan will be by defining the number of attempts that can happen within a certain time limit.
Summary
With the addition of SmartDefense to Check Point’s FireWall-1 NG, you now have additional protection within your enforcement points that was not previously available. SmartDefense allows you to look for abnormalities in packets and can take immediate action to prevent the malformed packets from entering into your network. To prevent these types of attacks, the Firewall has been given additional understanding about the structure of some commonly used protocols, such as HTTP, SMTP, and FTP. Most of the exploitations of these protocols are caused by sending a stream of data that the server never expects to see, such as an HTTP header that is larger than the memory space allocated to hold that piece of information.
Other features watch for suspicious behavior in the protocol data streams, such as in the SMTP protocol where someone may be snooping around and trying different commands to probe the server for information. In these situations, SmartDefense can end a session when it detects that an unusual number of commands are issued that are not directly needed to send an e-mail message.You are also given the ability to limit which commands are available when communicating with an FTP server; you have the option of removing commands that do not have a valid use in your environment.
In each case, you are tightening down what sort of behavior is acceptable on your network, and you can prevent a range of attacks, both new and old, by performing extra sanity checks on the protocol data. In some cases, these features can cause problems in certain network configurations, so Check Point has made most of the SmartDefense features optional, allowing you to pick which types of protection would be most beneficial in your environment.