Information Technology Reference
In-Depth Information
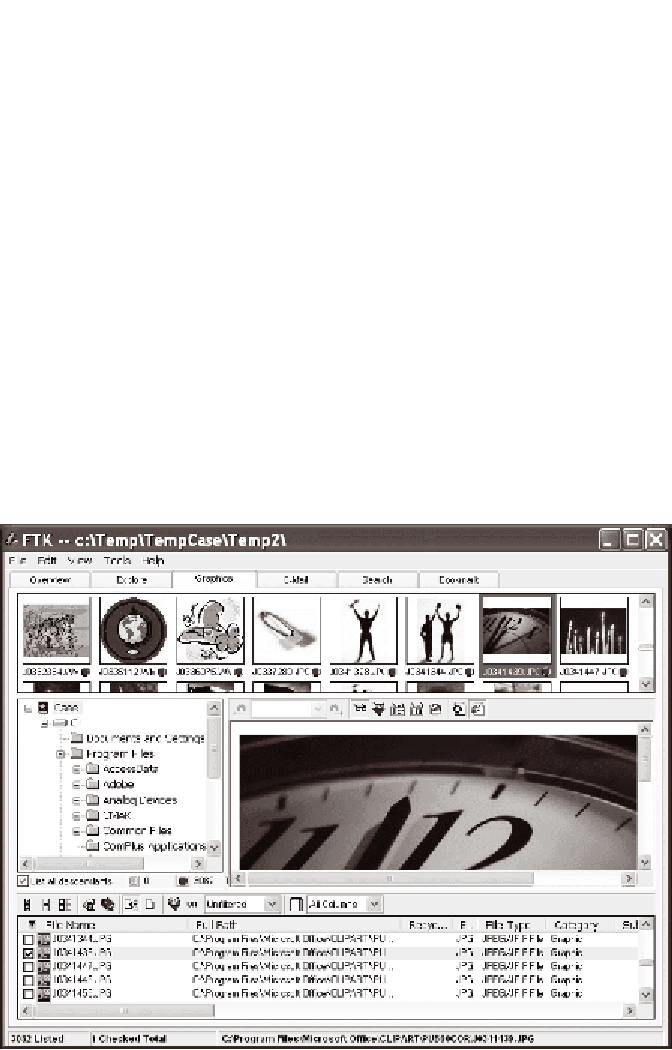
Figure 3.2 shows the use of this same tool to rapidly example files of
interest to an attacker after only a brief window of access to an unpro-
tected system.
Commercial forensic suites include products such as the Forensic Tool-
kit, as well as offerings from Encase, Paraben, and many other vendors.
FOSS-developed tools also exist, such as those preinstalled on the popu-
lar Helix bootable forensic CD based on the Knoppix Linux distribution.
Using tools already installed on this insert-and-run package, an attacker
can examine running processes, extract stored passwords and form data,
search for specific types of files, or even replicate an entire hard drive
for later deep analysis. These functions are invaluable to the professional
forensic investigator, but they are equally available to potential attackers
seeking to bypass access control mechanisms to gain unauthorized access
to protected resources.
Figure 3.2
The Forensic Toolkit being used to examine image fi les.