Information Technology Reference
In-Depth Information
directly from a Live CD or USB flash drive (Knoppix is a good example
of a media-bootable operating system), physical access to any computer
presents an attacker with almost immediate results. Security cannot
be “bolted on” later; it must form the basis for enterprise defense, data
encryption during storage and transport, and be deeply integrated into
application development standards.
Attackers Have Tools Too
An organization's most sensitive data is readily accessible without an
encrypted file system strong enough to resist tools that are available on
the Internet. Many tools originally intended for law enforcement and
security purposes can also be used by attackers to access sensitive infor-
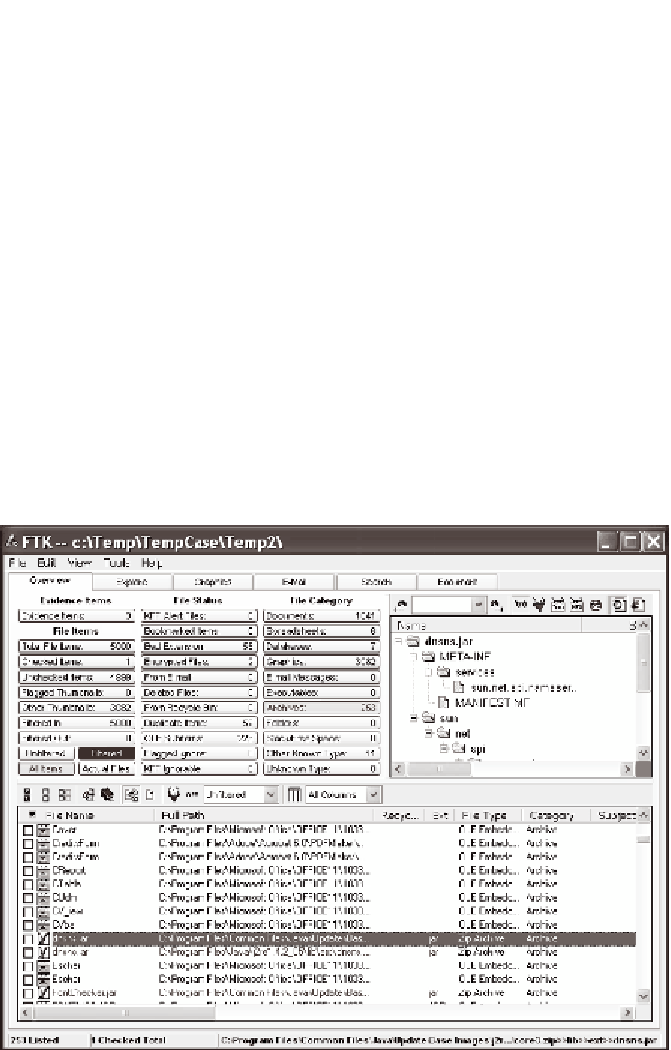
mation. Figure 3.1 shows an example of the type of data recovery that can
be conducted using the Forensic Toolkit package.
Figure 3.1
The Forensic Toolkit being used on an unencrypted drive.