Cryptography Reference
In-Depth Information
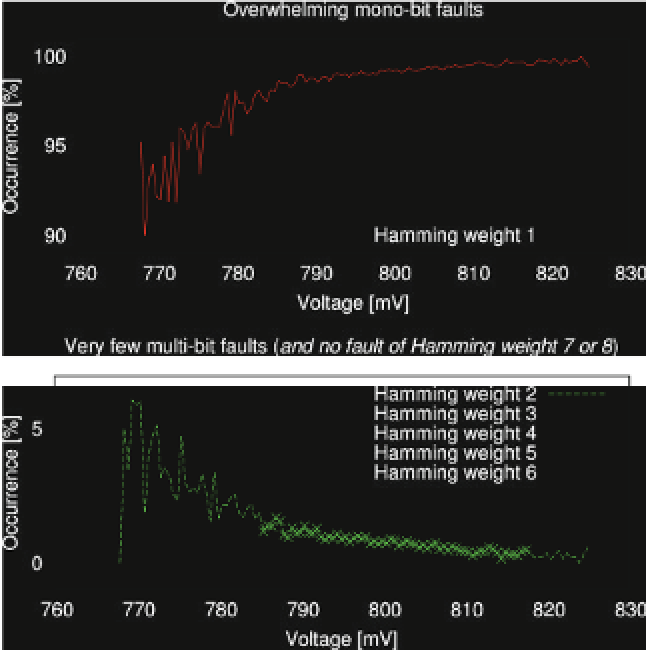
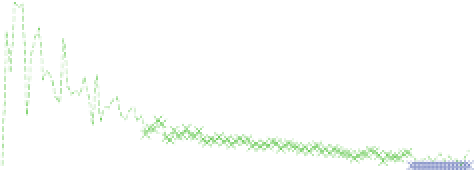
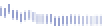
Fig. 17.11
Number of bits flipped amongst the single faults detected during the AES encryption
in the first rounds. Thus the maximum number of faults is expected to take place
exactly at the middle of the encryption (around round R5), accounting for the shape
of the occurrence curve. The average and variance of the time between two faults
depends on the stress level (in our case on the voltage) and on the implementation
type, as observed in [43].
The number of bits flipped in a byte is shown in Fig.
17.11
. It clearly appears that
for a low level of stress, most faults consist of a single bit-flip. This is consistent with
the fact that one single critical path gets violated. Conversely, we note that when the
stress gets higher single faults mainly consist of multiple erroneous bits.
17.3.2 Fault Statistics in Other Targets
As described in [43, 223], the same manipulations done in Sect.
17.3.1
on an ASIC can
be ported on an FPGA. For instance, the faults follow an occurrence law represented
in Fig.
17.12
. It is qualitatively similar to that of an ASIC (refer to Fig.
17.7
); thus
FPGAs are suitable platforms for studying global faults.
Now, if the critical component in a SoC is the CPU, then faults can modify either
the execution flow or the manipulated data. A complete study is carried out in [22,
24] on a 32-bit CPU of the ARM family running an AES. The fault model is found
to be original: faults occur only when the CPU is interacting with its internal RAM.