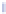Cryptography Reference
In-Depth Information
100
Detected errors
Exploitable errors in R7
Exploitable errors in R8
90
80
70
60
50
40
30
20
10
0
760
770
780
790
800
810
820
830
Voltage [mV]
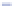
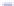
Fig. 17.8
Coverage of single faults, and detail of exploitable faults
17.3.1.5 Spatio-Temporal Characterization of Faults
The “covered” faults are single byte errors detected as per the search algorithm
depicted in Fig.
17.6
, and they are represented in Fig.
17.8
. We continue the analysis
in this section in terms of their spatio-temporal locality:
•
in which rounds (from R0 to R9) are they more likely? (refer to Fig.
17.9
) and
•
in which byte of the state are they more likely? (refer to Fig.
17.10
).
Figures
17.9
and
17.10
show the empirical PMF (Probability Mass Functions) of the
faults.
As already mentioned, we can see in Fig.
17.9
that the first round (R0) is never
affected by faults. This observation was indeed predictable, since the first round is
special: it consists of the AddRoundKey transformation alone. Therefore, the critical
path is not in this round.
It can seem counterintuitive that faults occur at one round and not at the others.
In a static timing analysis (STA) of a design, the critical path is the same for every
iteration. Therefore, one might expect that if a critical path is violated at one round,
then all the rounds will be faulty. However, we observe single errors localized at a
given round. The reason could be that the critical path is highly data-dependant.
From the analysis of Figs.
17.9
and
17.10
, we show that the faults are not uni-
formly distributed over time and space. This observation, albeit not general since our
setup is very particular, can be valuable for the designers in charge of implementing
countermeasures.
We can see that the first round is never affected by faults. Also, it appears clearly
that the faults are not uniformly distributed over time and space.
Some hints can be given about possible reasons for the heterogeneous distribution
of the faults. First of all, several instances of the S-Boxes operate in parallel in the