Cryptography Reference
In-Depth Information
0.9
0.8
0.7
0.6
0.5
0.4
0.3
Residue Mod 3
Hamming
Residue Mod 7
Parity
Double Parity
Complementary Parity
Reference
0.2
0.1
0
0
5
10
15
20
25
30
35
40
45
50
Number of Traces
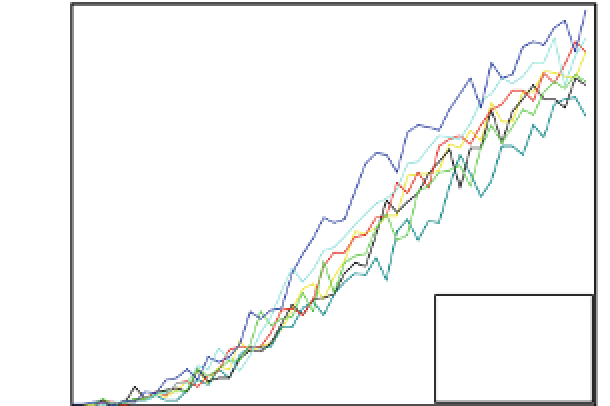
Fig. 15.10
Success rate of the correlation-based DPA attack versus the number of traces using
attack hypothesis of 8 bits only (the adversary is unaware of the error detection and correction code
used)
success rate of the correlation-based DPA when the attacker is aware of the presence
of the code, thus targeting all the bits of the output register. Figure
15.10
shows the
success rate of the DPA when the attack hypothesis is based on the Hamming weight
of only the eight output bits of the S-box, i.e., the attacker is unaware of the code
used. In both figures, the faster the curve approaches 1, the easier it is for the attacker
to recover the secret key.
As can be seen from Fig.
15.9
, the error detection/correction circuit that yields the
worst resistance against the correlation-based DPA attacks is the one that uses the
Hamming correcting code. The only code that seems to be slightly more resistant
than the reference S-Box is the one based on complementary parity. We can therefore
state that when the adversary mounting a correlation-based DPA attack is aware of
the particular error correction code used, the added redundancy significantly helps
the adversary. Note that the ranking of the circuits in Fig.
15.9
is in agreement with
that reported in Sect.
15.4.3
. The information theory metric was computed using
all the points of the trace and assumes a strong adversary; thus it incorporates also
information which can not be exploited by the attack considered in this case.
In contrast, as shown in Fig.
15.10
, when the presence of the particular error
detection/correction circuit is not known, the success rate of the reference S-box is
higher than all the others. This, however, does not mean that the presence of the check
bits can never help the attacker when he is unaware of them. The implementations that
include check bits still generate a large amount of information leakage, as indicated
by the information theory metric (and shown in Sect.
15.4.3
), and it is possible that
different technological libraries or more sophisticated attacks can show a significant
improvement even when the presence of the code is unknown.