Cryptography Reference
In-Depth Information
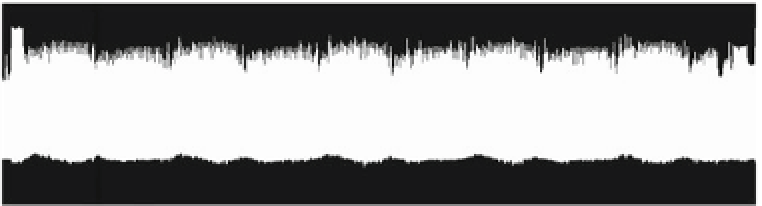
Fig. 1.4
Power consumption trace of a single AES encryption performed by a smart card
⎛
⎞
2311
1231
1123
3112
⎝
⎠
M
=
2
8
whose elements are also in
F
(
)
(here expressed as a decimal digit) is used to
map this column into a new vector.
•
AddRoundKey
: Each byte of the array is XORed with a byte from a corresponding
array of round subkeys.
Algorithm 1.3:
The AES-128
KeySchedule
function
Input
:
th
round key (
X
=
x
i
for
i
(
r
−
1
)
∈{
1
,...,
16
}
).
Output
:
r
th
round key
X
.
1
for
i
←
0
to
3
do
x
(
i
<<
2
)
+
1
←
x
(
i
<<
2
)
+
1
⊕
S
(
x
(((
i
+
1
)
∧
3
)<<
2
)
+
4
)
2
3
end
4
x
1
←
x
1
⊕
h
r
5
for
i
←
1
to
16
do
6
if
(
i
−
1
)
mod 4
=
0
then
x
i
←
x
i
⊕
x
i
−
1
7
8
end
9
end
10
return
X
Figure
1.4
shows a power consumption trace taken while a device was performing
an AES encryption. It shows a pattern that is repeated ten times, corresponding to the
ten AES rounds as described in Algorithm 1.2. The last pattern is slightly different
because the MixColumns function is not computed in the last round.
More information can be observed if the power consumption of one round is
analyzed in more detail. Figure
1.5
shows the power consumption of an ARM7
microprocessor while it is computing the first round of the AES. Two patterns of
16 peaks can be seen on the left-hand side that correspond to the plaintext and secret
key being permuted to enable efficient computation given the matrix representation