Cryptography Reference
In-Depth Information
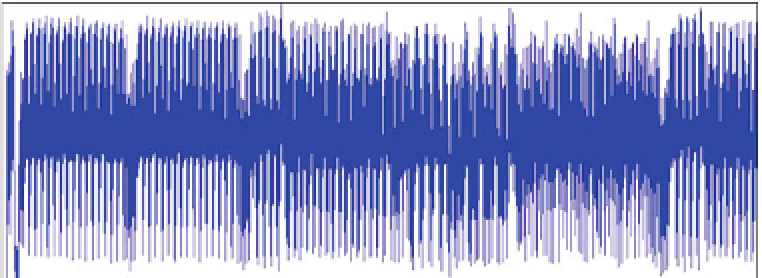
Fig. 1.5
Power consumption trace of a single round of an AES encryption performed by an ARM7
microprocessor
in the specification of the algorithm. This is followed by a pattern of four peaks that
correspond to the XOR with the first key byte (the ARM7 has a 32-bit architecture).
Following this there is a pattern of 16 peaks that correspond to the SubBytes function.
This is followed by two patterns of four peaks that corresponds to the generation of
the next subkey. The ShiftRow function occurs between these functions but is not
visible in the power consumption. The XOR with this subkey can be seen on the
right-hand side of Fig.
1.5
, which means that the remaining area between this XOR
and the generation of the subkey is where the MixColumns function is computed.
However, no obvious pattern can be seen without plotting this portion of the trace
with a higher granularity.
In general, such a visual inspection of the leakage traces can be used as a pre-
liminary step before a more powerful attack (such as DPA or DFA), and allows an
attacker to determine the parts of the traces that are relevant in a straightforward
manner.
The drawback of SPA is its limited granularity, as demonstrated by our example
above. It is typically straightforward to identify the AES rounds, as in Fig.
1.4
,but
identifying to round operations (i.e. AddRoundKey, SubBytes, MixColumns, and
ShiftRows) may be more difficult. For example, in Fig.
1.5
the MixColumns is iden-
tified by a process of elimination rather than by observing a pattern in the power
consumption. Furthermore, devices with larger data buses and ASIC (or FPGA)
implementations that process 128 bits in parallel may also make visual inspection
more difficult.
1.3.3 Case Study: File Access
As demonstrated in the previous sections, an attacker can potentially recover mean-
ingful information by analyzing a single acquisition of a side-channel. This can be
further extended to include branches in the commands being executed by a device.
One example of this is the ten rounds of the AES that are visible in Fig.
1.4
.Ifthis