Cryptography Reference
In-Depth Information
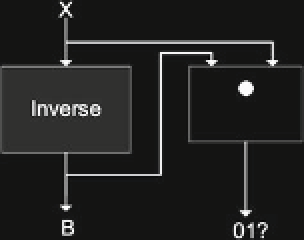
Fig. 11.6
Architecture for
protection of nonlinear block.
The redundant portion per-
forms partial multiplication in
GF
2
8
(
)
,(
r
=
2)
, there is at most one solution for
x
. Therefore all
nonzero errors
e
will be detected with a probability of at least 1
For every nonzero
e
=
(
e
1
,
e
2
)
2
−
r
. Moreover,
since error detection depends on the input
x
, the probability that
e
will be missed
after
m
random inputs is 2
−
rm
.
In one round of encryption of AES there are
T
−
16 disjoint inverters, each
with its own independent error detection. While for a single inverter the probability
of missing an error is constant for all fault multiplicities, this is not the case when
multiple inverters are considered together. The probability that a fault will not be
detected if it affects
t
inverters is
q
t
where
q
is the probability of missing a fault in
one inverter (For the proposed architecture,
q
=
2
−
r
).
Assuming that the distribution of faults is uniform, the probability that a fault of
multiplicity
l
will affect
t
out of
T
inverters can be determined as
P
T
(
≤
N
T
(
t
,
l
)
t
,
l
)
=
,
2
l
)
=
t
(
−
t
−
1
j
t
l
where
N
T
(
16 inverters
the probability of missing a fault of multiplicity
l
in the whole nonlinear portion of
the encryption of one round is
Q
T
(
t
,
l
1
N
t
(
j
,
l
))
. Thus, for AES and its
T
=
=
)
=
min
{
T
,
l
}
i
q
i
P
T
(
l
i
,
l
)
.
=
1
11.6.2 Protection of the Linear Block of AES
The general architecture used for protection with linear codes is presented in Fig.
11.7
.
The architecture is composed of three major hardware components: original hard-
ware, redundant hardware for predicting the
r
-bit signature
v
(which is a linear
combination of components of the output
x
of the original device), and an error
detection network (EDN).
The signature predictor contains most of the redundant hardware. The
k
bits of
output of the original hardware and the
r
redundant output bits of the signature
predictor form the
n
r
extended output of the device. The extended output
forms a codeword of the systematic error-detecting code which can be used to detect
errors in the original hardware or in the Predictor. It is the EDN that verifies that the
extended output of the device belongs to the corresponding code; if it does not, the
EDN raises an error signal. In a linear protection scheme the predicted
r
-bit signature
v
of the predictor is a linear combination of the
k
-bit output of the original device
(
v
=
k
+
=
Px
, where
P
is an
r
×
k
check matrix for the linear code used for protection).