Cryptography Reference
In-Depth Information
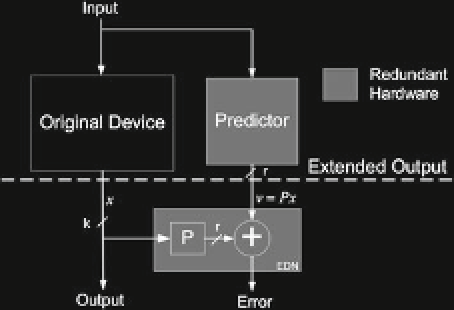
Fig. 11.7
General architec-
ture for protection of hardware
with linear error detecting
codes
Fig. 11.8
Architecture for
protection of hardware with
nonlinear partially robust error
detecting codes
With only slight modification, the same architecture used for protection with
linear codes can be used to provide protection based on the systematic nonlinear
partially robust codes
)
−
1
. The transformation only requires an addition of
two copies of one extra component for the multiplicative inverse in
GF
{
x
,(
Px
}
2
r
.The
modified architecture is shown in Fig.
11.8
. The extended output of the device is
now protected with the partially robust nonlinear code with the properties outlined
above. An additional (and identical) multiplicative inverse is also needed in the EDN
to verify the nonlinear signature. This transformation can be applied to any linear
protection method regardless of the algorithm it is protecting.
As Table
11.1
shows, one very desirable consequence of the addition of inversion
to create a robust code is the reduction in the number of undetectable errors. The
number of undetectable errors is reduced from 2
k
(
)
to 2
k
−
r
. When
k
=
r
, the code is
robust and all nonzero errors are detectable.
Since large
r
may be necessary to provide for a sufficiently high error-detecting
probability, the use of one large device which takes the multiplicative inverse of
all of the
r
-redundant bits might not be practical. Transforming an implementation
protected by a linear code with
r
32 into one protected by a robust systematic
code would require several thousands additional two-input gates.
=