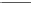Cryptography Reference
In-Depth Information
Definition 5.1.6
Basic Galois Counter mode (GCM)
Let e
()
be a block cipher of block size 128 bit; let x be the plaintext
consisting of the blocks x
1
,...,
x
n
; and let AAD be the additional
authenticated data.
1.
Encryption
a. Derive a counter value CT R
0
from the IV
and compute
CT R
1
=
CT R
0
+ 1
.
b. Compute ciphertext: y
i
=
e
k
(
CT R
i
)
⊕
x
i
,
i
≥
1
2.
Authentication
a. Generate authentication subkey H
=
e
k
(0)
b. Compute g
0
=
AAD
×
H
(Galois field multiplication)
c. Compute g
i
=(
g
i
−
1
⊕
y
i
)
×
H
,
1
≤
i
≤
n
(Galois field
multiplication)
d. Final authentication tag: T
=(
g
n
×
H
)
⊕
e
k
(
CT R
0
)
Figure 5.8 shows a diagram of the GCM.
Fig. 5.8
Basic authenticated encryption in Galois Counter mode
The receiver of the packet [(
y
1
,...,
y
n
)
,
T
,
ADD
] decrypts the ciphertext by also
applying the Counter mode. To check the authenticity of the data, the receiver also
computes an authentication tag
T
using the received ciphertext and
ADD
as input.
He employs exactly the same steps as the sender. If
T
and
T
match, the receiver is