Databases Reference
In-Depth Information
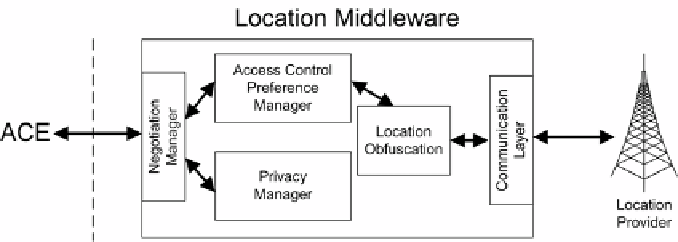
Fig. 3.
Location Middleware
The location middleware, whose logical schema is depicted in Fig. 3, in-
cludes the following components.
•
Communication Layer.
It manages the communication process with Loca-
tion Providers by hiding low-level communication details to other compo-
nents.
•
Negotiation Manager.
It acts as an interface with the Access Control En-
gine to provide negotiation functionalities regarding service quality and
availability based on specific negotiation protocols [34].
•
Access Control Preference Manager.
It manages location service attributes
and quality parameters by interacting with the Location Obfuscation com-
ponent.
•
Location Obfuscation.
It applies obfuscation techniques to location mea-
surements for protecting location privacy of users.
•
Privacy Manager.
It manages privacy preferences expressed by users and
supports the privacy-aware location-based predicate evaluation.
A key aspect of such a privacy-aware LBAC architecture is the choice of
the component in charge of evaluating LBAC predicates. Although LBAC
policy evaluation and enforcement are logically provided by the ACE (i.e.,
the LBAC system), the LBAC predicates evaluation could take place in two
different ways:
•
ACE Evaluation:
the ACE requests to the LM location information rel-
evant to the access decision, without communicating the actual LBAC
predicate to be evaluated. The returned response from the LM to the
ACE is an obfuscated location measurement with associated a relevance
value
R
Priv
that characterizes its accuracy. Given the relevance
R
LBAC
,
the ACE evaluates the LBAC predicate. Since
R
LBAC
represents the min-
imum accuracy level that the ACE is willing to accept for a certain service
provisioning,
R
LBAC
≤R
Eval
must hold or the evaluation of the location
predicate is rejected.
•
LM Evaluation:
the ACE communicates to the LM the actual LBAC predi-
cate and requests its evaluation based on location information managed by