Databases Reference
In-Depth Information
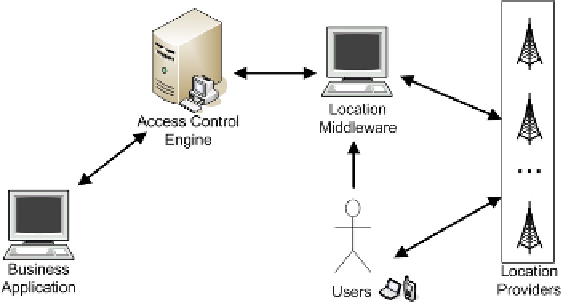
Fig. 2.
A privacy-Aware LBAC Architecture
systems. A privacy-aware LBAC architecture must be developed integrating
components logically tied with the applications that need location-based ac-
cess control enforcement and components providing privacy-aware location
services. One typical approach in the design of LBAC architectures is to pro-
vide a location middleware acting as a trusted gateway between the LBAC
system and the location services. Such a component is in charge of managing
all interactions with sensing technologies and enforce users privacy prefer-
ences. In [30, 31, 32] the authors present a privacy-aware LBAC architecture
(see Fig. 2) whose logical components can be summarized as follows.
•
User.
It is the subject to be located through her mobile device during
the interaction with the Business Application. The user first defines her
privacy preferences at the Location Middleware and then interacts with
the Access Control Engine to gain the access to the Business Application.
•
Business application.
It represents a service provider that offers resources
protected by LBAC policies. It relies on the Access Control Engine for
evaluating policies based on users location.
•
Access Control Engine (ACE).
It is the component responsible for the
evaluation and enforcement of LBAC policies. It relies on functionalities
provided by a specialized privacy-aware Location Middleware to collect
information about the positions of the User involved in the access control
decision process.
•
Location Middleware (LM).
It represents the core component of the ar-
chitecture. It manages the low-level communications with the Location
Provider and enforces both the privacy preferences of the User and the
need of location accuracy requested by the Access Control Engine.
•
Location Provider (LP).
It is the component that manages sensing tech-
nologies to provide location measurement of the User to the Location Mid-
dleware.