Databases Reference
In-Depth Information
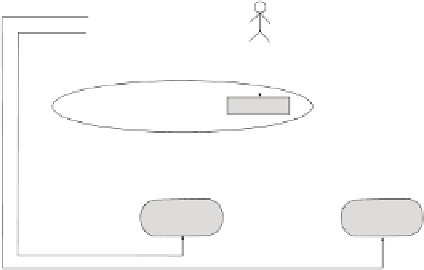
Fig. 4.
The static, multiple-issuer case
2.3 The dynamic case
In contrast with the static case, in the dynamic case it is assumed that the
attacker is able to recognize that a set of requests has been issued by the same
user. Researchers [1, 10] have considered such a possibility. We call this
linking
.
Several techniques exist to
link
different requests to the same user, with the
most trivial ones being the observation of the same identity or pseudo-id in
the requests. We call
request trace
a set of requests that the attacker can
correctly associate to a single user.
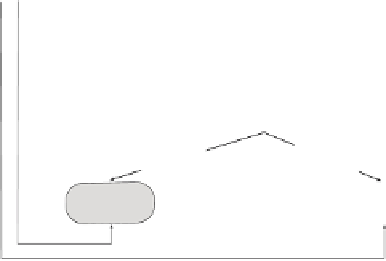
Figure 5 shows a graphical representation of the dynamic case. The corre-
sponding techniques to preserve privacy are facing two problems. First, pre-
venting the attacker from linking the requests (called
linking problem
); In-
deed, the longer is a trace, the higher the probability of the issuer to loose
her privacy. Second, preventing the attacker from understanding the sensitive
association from a request trace.
Fig. 5.
The dynamic case