Databases Reference
In-Depth Information
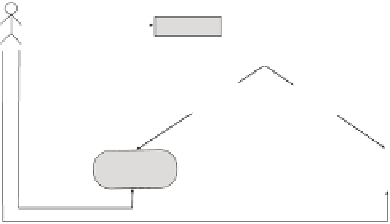
Figure 3 shows a graphical representation of the privacy threat in the
static, single-issuer case. In this case, in order to prevent the disclosure of
the sensible association, it is sucient to prevent the attacker from inferring
either user's identity or user's sensitive information. The ongoing research in
this field is tackling these two subproblems: prevent the attacker from inferring
the user's identity and prevent the attacker from inferring the user's private
information. Despite the solution of one of the two subproblems is sucient to
guarantee user's privacy, we argue that the solution of both subproblems could
enhance better techniques for privacy protection. Indeed, the obfuscation of
requests parameters usually involved in privacy protection techniques implies
a degradation of the quality of service. A location based privacy preserving
system that implements solutions for both the subproblems can combine them
in order to to optimize quality of service while preserving privacy.
Fig. 3.
The static, single-issuer case
Example 1 shows that, in the multiple-issuer case, an attacker can infer the
sensitive association for a user even if the identity of that user is not revealed
to the attacker.
Example 1.
Suppose a user
u
issues a request generalized into
r
by the LTS.
Assume that, considering
r
, an attacker can only understand that the issuer
of
r
is one of the users in the set
S
of potential issuers. However, if all of the
users in
S
issue requests from which the attacker can infer the same sensitive
information inferred from
r
, then the attacker can associate that sensitive
information to
u
.
In the area of privacy in databases, this kind of attack is known as
homo-
geneity attack
[14]. The problem in the area of LBS is depicted in Figure 4.
Note that, differently from the general case (Figure 1), in the static, multiple-
issuer case, a single request for each user is considered.