Information Technology Reference
In-Depth Information
using Trusted Extensions to meet the needs of sensitive data environments, in-
cluding corporate financial transaction systems and medical record systems.
The Trusted Extensions feature set uses Containers to compartmentalize
data and processing. A key factor in its ability to achieve the Common Criteria
Certification described earlier is the robust security boundary that exists around
individual Containers.
The features of Oracle Solaris Trusted Extensions are described in detail in the
book
Solaris Security Essentials
.
OpenSolaris offers some features that are not available in Solaris 10. These fea-
tures include network virtualization features originally called Project Crossbow.
Each of these feature sets is described in detail at
http://opensolaris.org
and in the
man
pages for OpenSolaris. The network virtualization features are
described in this section.
Network virtualization makes it possible to implement traditional network archi-
tectures within a computer without losing any flexibility in network design. The new
network virtualization features in OpenSolaris enable you to create these objects:
Virtual network interface connectors (VNICs), which can be used with
Containers to increase the isolation between Containers without losing
scalability
■
Virtual switches (vSwitches), which can be used in the same way as physical
switches—that is, to connect VEs to each other and to a physical network port
■
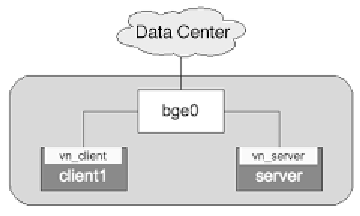
The use of virtual networks starts with a network design. The simplest practi-
cal use of virtual network components is to create multiple VNICs so that two
Containers can share a physical NIC. In Figure 6.8, one VNIC has been created for
each of two Containers. Each VNIC uses a physical NIC for communication with
network devices outside of this computer.
Figure 6.8
Virtual NICs

Search WWH ::

Custom Search