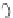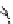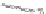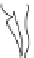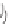Cryptography Reference
In-Depth Information
Alice
Fred
Bob
b
a
g
a
(mod
p
)
g
f
(mod
p
)
g
f
(mod
p
)
g
b
(mod
p
)
(
g
f
)
a
=
g
af
(
g
f
)
b
=
g
bf
Figure 9.11.
Man-in-the-middle attack against the Diffie-Hellman protocol
3. Bob continues the Diffie-Hellman protocol as if nothing untoward has
happened. Bob randomly generates a positive integer
b
and calculates
g
b
.
Bob sends
g
b
to Alice.
4. Fred intercepts this message before it reaches Alice. Fred then claims to be
Bob and sends
g
f
to Alice instead of
g
b
.
5. Alice nowbelieves that the Diffie-Hellman protocol has successfully completed.
She uses
g
f
and her private integer
a
to compute
g
af
=
(
g
f
)
a
.
6. Bob also believes that it has successfully completed. He uses
g
f
and
b
to
(
g
f
)
b
.
7. Fred computes
g
af
compute
g
bf
=
(
g
b
)
f
. He now has two different shared
values,
g
af
, which he shares with Alice, and
g
bf
, which he shares with Bob.
(
g
a
)
f
and
g
bf
=
=
At the end of thisman-in-the-middle attack, all three entities hold different beliefs:
• Alice believes that she has established a shared value with Bob. But she is
wrong, because she has established a shared value with Fred.
• Bob believes that he has established a shared value with Alice. But he is wrong,
because he has established a shared value with Fred.
• Fred correctly believes that he has established two different shared values, one
with Alice and the other with Bob.
Note that at the end of this man-in-the-middle attack, Fred cannot determine the
shared value
g
ab
that Alice and Bob would have established had he not interfered,
since both
a
and
b
remain secret to him, protected by the difficulty of the discrete
logarithm problem. Nonetheless, Fred is now in a powerful position:
• If Fred's objectivewas simply to disrupt the key establishment process between
Alice and Bob then he has already succeeded. If Alice derives a key
K
AF
from
g
af
and then encrypts a message to Bob using this key, Bob will not be able
to decrypt it successfully because the key
K
BF
that he derives from his shared
value
g
bf
will be different from
K
AF
.
• Much more serious is the situation that arises if Fred remains on the
communication channel. In this case, if Alice encrypts a plaintext to Bob using