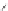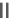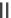Cryptography Reference
In-Depth Information
key
K
AF
, Fred (who is the only person who can derive both
K
AF
and
K
BF
) can
decrypt the ciphertext using
K
AF
to learn the plaintext. He can then re-encrypt
the plaintext using
K
BF
and send this to Bob. In this way, Fred can 'monitor' the
encrypted
communication between Alice and Bob without them being aware
that this is even happening.
This man-in-the middle attack was only able to succeed because neither Alice
nor Bob could determine from whom they were receiving messages during the
Diffie-Hellman protocol run. To solve this problem, we need to strengthen the
Diffie-Hellman protocol so that it meets the authentication goals of Section 9.4.1
as well as the key establishment goals.
AKE PROTOCOLS BASED ON DIFFIE-HELLMAN
Although the basic Diffie-Hellman protocol that we described in Section 9.4.2
does not provide authentication, there are many different ways in which it can be
adapted to do so.
We now describe one way of building in authentication. The
station-to-
station
(STS) protocol makes an additional assumption that Alice and Bob have
each established a long-term signature/verification key pair and have had their
verification keys certified (see Section 11.1.2). The STS protocol is shown in
Figure 9.12 and proceeds as follows (where all calculations are modulo
p
):
1. Alice randomly generates a positive integer
a
and calculates
g
a
. Alice sends
g
a
to Bob, along with the certificate
CertA
for her verification key.
2. Bob verifies
CertA
. If he is satisfied with the result then Bob randomly generates
a positive integer
b
and calculates
g
b
. Next, Bob signs a message that consists
of Alice's name,
g
a
and
g
b
. Bob then sends
g
b
to Alice, along with the certificate
CertB
for his verification key and the signed message.
3. Alice verifies
CertB
. If she is satisfied with the result then she uses Bob's
verification key to verify the signed message. If she is satisfied with this, she
signs a message that consists of Bob's name,
g
a
and
g
b
, which she then sends
back to Bob. Finally, Alice uses
g
b
and her private key
a
to compute (
g
b
)
a
.
Alice
Bob
a
b
g
a
(mod
p
)
CertA
g
b
(mod
p
)
CertB
Sig
B
( Alice
g
b
g
a
)
Sig
A
( Bob
g
a
g
b
)
(
g
b
)
a
=
g
ab
(
g
a
)
b
=
g
ab
Figure 9.12.
Station-to-station protocol