Java Reference
In-Depth Information
stored, processed, or transmitted by it. Several incorrect implementation practices of authentica-
tion are in use, of which we will cover a few signiicant ones:
Direct page request
—he irst one is the direct page request. For instance, an attacker accesses
a Web application, which presents him/her with a login page requesting credentials from the
attacker. he attacker tries to directly access a restricted page, and in case of an improperly
implemented authentication system that does not bind authentication and authorization
requirements to pages, the attacker is allowed to access the requested page and the suppos-
edly sensitive and restricted resources of the application.
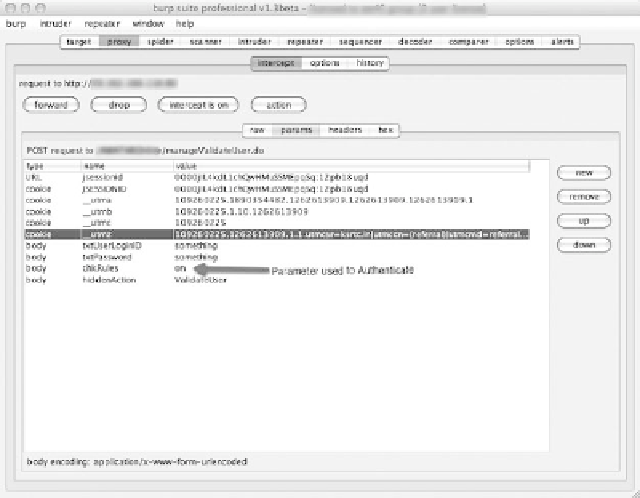
Parameter modiication—
Another law that is quite common in several authentication sys-
tems is parameter modiication, also known as parameter tampering. In certain authentica-
tion mechanisms there are certain parameters that are passed along with the user credentials
for authentication to the Web applications. For instance, some Web applications pass a
parameter like “authenticated” or “validated,” which may be set to “yes” with a Web applica-
tion proxy or by directly setting the parameter in the URL. his causes the authentication
to take place, regardless of the invalid passed-on credentials. Figure 12.11 highlights the
use of a Web application proxy in tampering with the HTTP request by tampering with a
parameter to bypass its authentication system.
12.2.2.4 Testing for Logout and Other Functionality
Ideally, the user's session should be invalidated or destroyed once the user has logged out of
the application. he user should not be able to reuse the session once he/she has logged out of
Figure 12.11
tampering with parameters to bypass the Web application authentication
system.
Search WWH ::

Custom Search