Java Reference
In-Depth Information
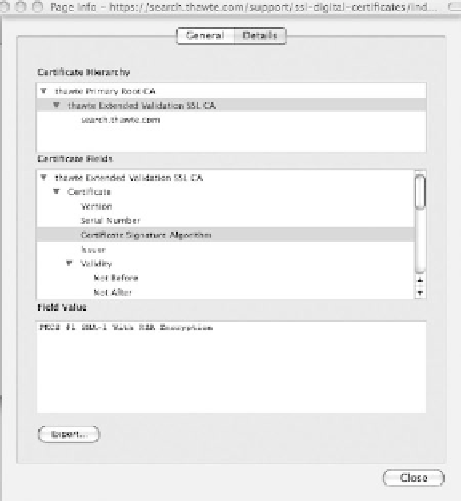
Figure 12.10
Screen capture of an SSL/tLS certiicate being viewed from the browser.
Web application vulnerability assessment tools automatically assess the strength of the SSL/
TLS certiicate being used to create encryption connections to the Web application, and if these
certiicates are found to be of a poor quality, they are highlighted as a potential security vulner-
ability in their assessment reports. SSL vulnerabilities are also highlighted by port scanning or
network vulnerability assessment tools like Nmap. Provided below is an extract of an Nmap port
scanning result containing details about a server supporting the nonsecure SSL v. 2.0.
443/tcp open ssl/http Microsoft IIS webserver 6.0
|_ html-title: 403 Forbidden
|_ sslv2: server still supports SSLv2
In several cases, the implementation of a strong SSL/TLS may also prove to be lawed. he
attacker may be able to force a user to submit sensitive information to the Web application over
an HTTP connection; that is, the Web application does not require the submission of sensitive
information over HTTPS only. he Web application should be conigured in such a manner that
sensitive information like credentials and credit card information may only be transmitted via
HTTPS with a POST request; if the Web application fails to do so, the tester has to bring the
vulnerability to the notice of the organization.
12.2.2.3 Testing for Authentication Schema
Implementation of an authentication system is an important requirement for security of the Web
application. Authentication is considered the perimeter security measure for a Web application,
which, if breached, can result in a compromise of the application and the sensitive information
Search WWH ::

Custom Search