Information Technology Reference
In-Depth Information
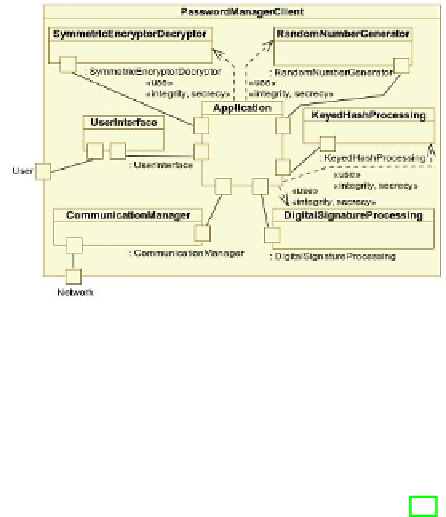
Fig. 4.
Structural View of Password Manager Client
the complete development life-cycle for both case studies, i.e., from requirements
engineering to architectural and fine-grained design to the implementation and
testing of the programs. Moreover, we created all development artifacts as advo-
cated by SEPP. While we present in this paper only a small part of the password
manager case study, the complete results are contained in [14] and partly in a
technical report about UMLsec4UML2 [15].
Security requirements analysis of the password manager following SEPP as
outlined in Sect. 2 leads to the elicitation and analysis of 13 different security
requirements, e.g., about the confidentiality and integrity of the different user-
names and passwords. Due to partly overlapping security requirements, only 11
different CSPF instances are developed. Consequently, 11 different GSAs are in-
stantiated and combined yielding a global secure software architecture. Figure 4
partly shows the structural view of global secure software architecture of the
password manager client expressed using a composite structure diagram. There,
instances of GSCs for encryption/ decryption, keyed hash processing, digital sig-
nature processing, generation of random numbers, as well as instances of GNCs
for the user interface and network communication work together, coordinated
by the application layer GNC instance, in order to ensure secure communi-
cation between the password manager client and server over the Internet. The
global architecture consisting of instances of GSCs and GNCs significantly helped
us to proceed with the development phases to follow. We identified adequate
frameworks, off-the-shelf components, and API modules based on the generated
artifacts, i.e., the components, the explicit interface descriptions, the protocol
descriptions, and the UMLsec4UML2 security annotations. Consequently, the
programming phase had to cover creating the glue code to connect the exist-
ing components and modules only. In summary, the case studies show that using
patterns to bridge the gap between security requirements analysis and secure ar-
chitectural design constitutes a feasible and promising contribution to the field
of secure software engineering.