Cryptography Reference
In-Depth Information
of the attack and a few improvements we introduce to make return-oriented
programming more effective in our attack.
3.1 Attack Intuition
As many memory pages are made non-writable or non-executable in an address
space randomization system, our attack tries to use existing code in the system
to perform arbitrary computation. A typical way of performing such an attack
is to use return-to-libc attacks to transfer control to system function
.
Recall that we assume that the first step of the attack to subvert the control
flow of the program, see Section 2, has been done. Therefore, the most important
next step is to locate the address of a system call in existing code (e.g., in libc)
and then transfer control over there.
execve()
Randomizing base address of the library and order of library functions.
Ran-
domizing the base address of libc and the order of libc functions are definitely
effective in making our attack more dicult, since the address of these function
has been randomized and cannot be pre-computed in our attack.
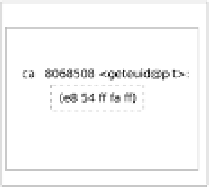
Randomizing entries in PLT and GOT.
PLT (procedure linkage table) and GOT
(global offset table) play crucial roles in resolution of library functions, and
therefore is a potential target of our attack. As shown in Figure 1, GOT stores the
address of libc functions, while PLT contains entries that jump to the addresses
stored in GOT.
The dependency between randomizing PLT/GOT and randomizing library
base address and functions was well documented — if an attacker knows the
location and offsets of PLT, then the address of libc functions can be found even
if the base address of libc and order of libc functions are randomized [4].
We have seen the dependency between randomizing libc and randomizing
PLT/GOT because addresses of libc functions are used in PLT/GOT. By the
same token, entries of PLT/GOT are used by other parts of the program, in
particular, by
instructions in the code segment. If an attack can locate
call
Fig. 1.
PLT and GOT in a dynamically linked ELF executable






























Search WWH ::

Custom Search