Cryptography Reference
In-Depth Information
Input: Key-dependent scrambled permutation array S[0...N −1].
Output: Pseudo-random keystream bytes z.
Initialization:
i = j = 0;
Output Keystream Generation Loop:
i = i + 1;
j = j + S[i];
Swap(S[i], S[j]);
t = S[i] + S[j];
Output z = S[t];
Algorithm 2.4.2: RC4 PRGA
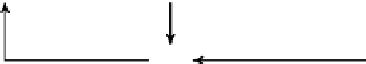
outputs the value of S at index S[i] + S[j] as the value of z. Figure 2.2 gives
a pictorial representation of one keystream byte generation.
The n-bit keystream output z is XOR-ed with the next n bits of the
message to generate the next n bits of the ciphertext at the sender end. Again,
z is bitwise XOR-ed with the ciphertext byte to get back the message at the
receiver end.
0
S[i] + S[j]
i
j
255
SWAP
Z
⊞
(after SWAP)
FIGURE 2.2: Output byte generation in RC4 PRGA.
Any addition, used in the RC4 description or in addition of key and per-
mutation bytes in this topic, is in general addition modulo N unless specified
otherwise.
A simple implementation of RC4 in C is given in Appendix A.
Two decades have elapsed since the inception of RC4. A variety of other
stream ciphers have been discovered after RC4, yet it is the most popular and
frequently used stream cipher algorithm due to its simplicity, ease of imple-
mentation, byte-oriented structure, speed and e
ciency. On the contrary, the
eSTREAM candidates have much complicated structures in general and they
work on word (32 bits) oriented manner. Even after many years of crypt-
analysis, the strengths and weaknesses of RC4 are of great interest to the
community.