Java Reference
In-Depth Information
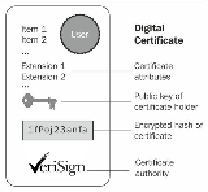
Public key certificates are commonly used to secure the interaction with websites. By de-
fault, the web browser ships with a set of predefined CAs; they are used to verify that the
public certificate served to a browser when you enter a secure site has actually been issued
by the owner of the website. In short, if you connect your browser to
ht-
tps://www.abc.com
and your browser doesn't give any certificate warning, you can
safely interact with the entity in charge of the site, that is, unless the site or your browser
has been hacked. However, this is another story.
Note
Simple authentication and client authentication
In the previous example, we depicted a simple authentication, (also called server authen-
tication). In this scenario, the only party that needs to prove its identity is the server.
SSL, however, is able to perform mutual authentication (also called client or two-way au-
thentication); here too, the server requests a client certificate during the SSL handshake
over the network.
Client authentication requires a client certificate in the x.509 format from a CA. The x.509
format is an industry-standard format for SSL certificates. In the next section, we will ex-
plore which tools are available to generate digital certificates, and how to get your certi-
ficates signed by a CA.