Java Reference
In-Depth Information
For this reason, a mission-critical enterprise system usually relies on the asymmetric en-
cryption algorithms, which tend to be easier to employ, manage, and are ultimately more
secure.
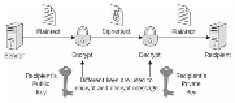
Asymmetric cryptography, also known as
public-key cryptography
, is based on the
concept that the key used to encrypt is not the same as the key that is used to decrypt the
message. In practice, each user holds a couple of keys: the public key that is distributed to
other parties and the private key that is kept as a secret. Each message is encrypted with
the recipient's public key and can only be decrypted (by the recipient) with his private key,
as shown in the following diagram:
Using asymmetric encryption, you can be sure that your message cannot be disclosed to a
third party. However, there is still one vulnerability.
Suppose you want to exchange some valuable information with a business partner and to
that end are requesting his public key by telephone or email. A fraudulent user intercepts
your e-mail or simply listens to your conversation and quickly sends you a fake mail with
his public key. Now, even if your data transmission is secured, it will be directed to the
wrong person!
In order to solve this issue, we need a document to verify that the public key belongs to a
particular individual. This document is called a
digital certificate
or public-key certific-
ate. A digital certificate consists of a formatted block of data that contains the name of the
certificate holder (which may be either a user or system name) and the holder's public key,
along with the digital signature of a
Certification Authority
(
CA
) for authentication. The
CA attests that the sender's name is the one associated with the public key in the docu-
ment.