Information Technology Reference
In-Depth Information
This process will result in the disruption of data packet delivery to the sink node.
Ideally, a given cache entry needs to be wiped out before the first data packet from
the source node arrives at the target node. Otherwise the attack may succeed but may
not be able to completely suppress the data flow. Though mechanistically different,
the effect of this attack is analogous to that of '
DNS cache-poisoning
'
(http://en.wikipedia.org/wiki/DNS_cache_poisoning). However, we cannot use the
same methods of protection against
DNS cache-poisoning
(i.e., randomised ports,
restricted relaying, etc.) since these are aimed at the control plane and the
Interest
Cache Poisoning Attack
is performed on the data plane.
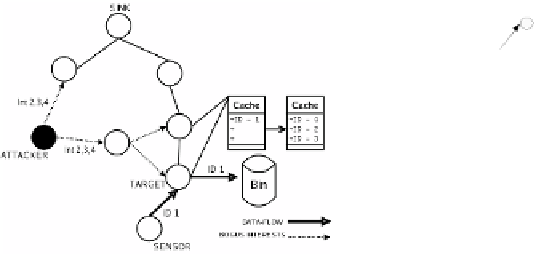
(a) Interest Cache Poisoning Attack Overview
(b) Bogus interest packet propagation
Fig. 2.
Interest Cache Poisoning Attack
Fig. 2 (a) shows the impact of the attack. The attacker sends out the bogus packets
and fills up the cache of the nodes on the data path. The bogus interests will replace
the original interest with ID 1. When the requested data with ID 1 arrives later, the
target node will just drop it. This is because there is no matching entry in the cache.
As shown in Fig. 2 (b), the attack will even be successful if the attacker is not next to
the target node. The attack exploits the flooding behaviour of Directed Diffusion.
Whenever a node receives a new interest packet it will rebroadcast it to all its
neighbours. Hence, the bogus interest packets are spread and affect the caches of
many nodes, eventually the cache of a target node. As a result, the impact of bogus
packets can propagate over an entire network and disrupt multiple paths of data
packet delivery.
5 Using the DC Algorithm to Detect Interest Cache Poisoning
Sensor networks using Directed Diffusion share a surprising number of similarities
with biological tissue, including susceptibility to poison. Here we propose a security
solution for sensor networks utilising Directed Diffusion with the aim of detecting
cache poisoning attacks. The mechanism incorporates an immune algorithm inspired
by the responsiveness of DCs in the human immune system to danger signals.