Hardware Reference
In-Depth Information
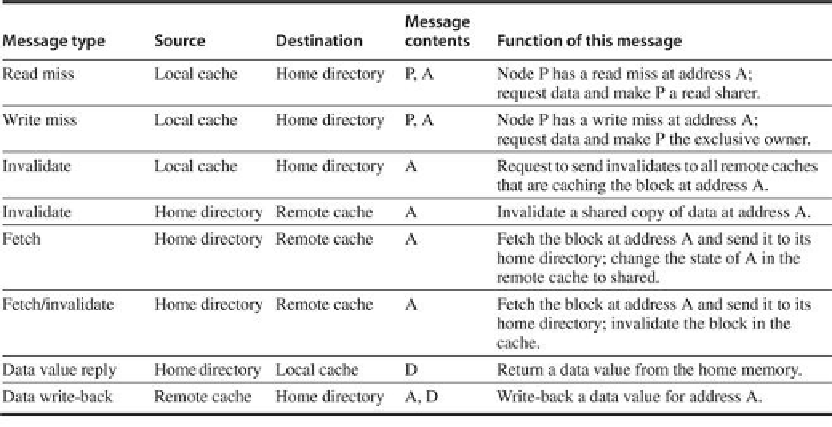
FIGURE 5.21
The possible messages sent among nodes to maintain coherence, along
with the source and destination node, the contents (where P = requesting node num-
ber, A = requested address, and D = data contents), and the function of the message
.
The first three messages are requests sent by the local node to the home. The fourth through
sixth messages are messages sent to a remote node by the home when the home needs the
data to satisfy a read or write miss request. Data value replies are used to send a value from
the home node back to the requesting node. Data value write-backs occur for two reasons:
when a block is replaced in a cache and must be written back to its home memory, and also in
reply to fetch or fetch/invalidate messages from the home. Writing back the data value
whenever the block becomes shared simplifies the number of states in the protocol, since any
dirty block must be exclusive and any shared block is always available in the home memory.
A remote node is the node that has a copy of a cache block, whether exclusive (in which
case it is the only copy) or shared. A remote node may be the same as either the local node or
the home node. In such cases, the basic protocol does not change, but interprocessor messages
may be replaced with intraprocessor messages.
In this section, we assume a simple model of memory consistency. To minimize the type of
messages and the complexity of the protocol, we make an assumption that messages will be
received and acted upon in the same order they are sent. This assumption may not be true in
practice and can result in additional complications, some of which we address in
Section 5.6
when we discuss mem-ory consistency models. In this section, we use this assumption to en-
sure that invalidates sent by a node are honored before new messages are transmitted, just as
we assumed in the discussion of implementing snooping protocols. As we did in the snooping
case, we omit some details necessary to implement the coherence protocol. In particular, the
serialization of writes and knowing that the invalidates for a write have completed are not as
simple as in the broadcast-based snooping mechanism. Instead, explicit acknowledgments are
required in response to write misses and invalidate requests. We discuss these issues in more
detail in Appendix I.
Search WWH ::

Custom Search