Information Technology Reference
In-Depth Information
(a)
(b)
Fig. 1.
Schematics of QCA cell and wire: (a) Binary QCA cells, (b) A QCA wire
composed of coupled cells.
a power analysis attack [
25
-
27
], which can extract the secret key of an electronic
security device by measuring the power consumption of the device while it is
performing cryptographic operations. The power consumption of a CMOS device
is highly dependant on processed data. As QCA is a field coupled computing
paradigm which only involves changing the position of electrons in the cells, its
power consumption is ultra-low. Therefore, it is interesting and appropriate to
ask if QCA cryptographic circuits are immune to power analysis attack.
The power dissipation of QCA circuits has been studied. A quantum mechan-
ical power model based on the density matrix formalism was proposed by Timler
and Lent [
22
,
28
]. This model can estimate the power dissipation of QCA circuits
quite accurately, however, it is computationally expensive to use for large scale
designs. The energy dissipated in a 2-cell chain was investigated using an RC
model by Bond and Macucci [
29
]. Based on the work by Timler and Lent [
22
],
a upper bound power model to compute the upper bound of the power con-
sumed in QCA circuits was proposed by Srivastava
et al.
[
30
]. This power model
can provide a tight upper bound of the power consumption in QCA circuits for
quasi-adiabatic (smooth) switching. The lower bound power dissipation for QCA
circuits was also studied by Lent
et al.
[
31
]. The lower bound power dissipation
was studied by applying a Bennett clock to logically reversible QCA circuits.
Both the best case and the worst case scenarios for an attacker are considered
to evaluate the security of QCA cryptographic circuits in terms of power analy-
sis attacks. Power dissipation during quasi-adiabatic switching is very low [
22
].
However, a more realistic scenario of switching is more abrupt and hence will
introduce more power dissipation. Generally, the greater the power dissipation,
the easier it is to perform a power analysis attack [
25
,
32
]. The best case sce-
nario for attackers involves upper bound power dissipation with non-adiabatic
clocking. Therefore, the upper bound power model [
30
] can be used to assess
the performance of QCA cryptographic circuits under power analysis attack.
To fully address the security issues related to power analysis attack, the worst












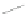


























































Search WWH ::

Custom Search