Java Reference
In-Depth Information
In the current context, however, we are more interested in the second
use of public-private key pairs: enabling authentication using digital
signatures. A digital signature is an electronic analogy of a conventional
signature. It authenticates the source of the document and verifies that
the document has not been tampered with in transit. Signing a document
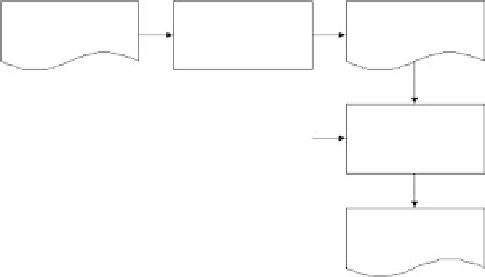
is a two-stage process: a message digest is created that is a unique
representation of the contents of the document; the message digest is then
encrypted using the private key of the sender (see Figure 2.11).
Hash function
(MD5)
Message
Message digest
RSA
cryptographic
process
Sender's
Digital
signature
Figure 2.11
Encryption process in a nutshell
The receiver of the document then uses the public key of the sender
to decrypt the message digest, creates a digest of the received contents,
and checks that it matches the decrypted digest that accompanied the
document. Hence, a digital signature is used to verify that a document was
sent by the holder of the private key, not some third party masquerading
as the sender, and that the contents have not been tampered with in
transit. This raises the issue of key management and how the receiver of
a public key can verify the source of the public key. For instance, if I
receive a digitally signed JAR file, I need the public key of the signer to
verify the signature, but how do I verify the source of the public key? The
public key itself is just a series of numbers, with no clue as to the identity
of the owner. I need to have confidence that a public key purporting
to belong to a legitimate organization does in fact originate from that
organization and has not been distributed by an impostor, enabling the
impostor to masquerade as the legitimate organization, signing files using
the private key of a bogus key pair. The solution is to distribute the public
key in the form of a certificate from a trusted certificate authority (CA).
A certificate authority distributes a certificate that contains details of a
person's or organization's identity, the public key belonging to that person
or organization, and the identity of the issuing CA. The CA vouches that
the public key contained in the certificate does indeed belong to the
person or organization identified on the certificate. To verify that the