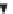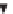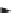Java Reference
In-Depth Information
certificate was issued by the CA, the certificate is digitally signed by the
CA using its private key. The format of certificates used in X509.PKI is
known as the X509 format.
Of course, this raises the question of how the recipient of the certificate
verifies the digital signature contained therein. This is resolved using root
certificates or root keys. The root certificate contains details of the identity
of the CA and the public key of the CA (the root key) and is signed by the
CA itself (self-signed). For mobile phones that support one or more trusted
protection domains, one or more certificates ship with the device, placed
on the phone by the manufacturer or embedded in the WIM/SIM card by
the network operator. Each certificate is associated with a trusted protec-
tion domain, so that a signed MIDlet that is authenticated against a cer-
tificate is bound to the protection domain associated with that certificate.
2.5.2 Certification Paths
In practice, the authentication of a signed file using the root certificate
may be more complex than the simplified approach described above.
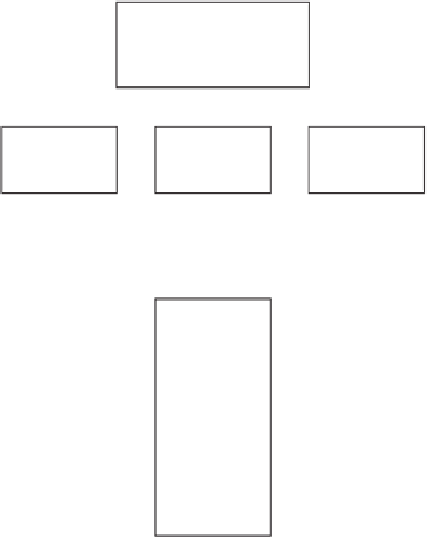
The PKI allows for a hierarchy of certificate authorities (see Figure 2.12)
Root CA
(Trust Anchor)
Operator 1
CA
Operator 2
CA
Manufacturer
1 CA
ISV 1
ISV 2
ISV 3
ISV 4
ISV 5
ISV 6
Trust Anchor's Certificate
Figure 2.12
Applications from a variety of independent software vendors (ISVs) signed by
various CAs and authenticated by a single trust root