Information Technology Reference
In-Depth Information
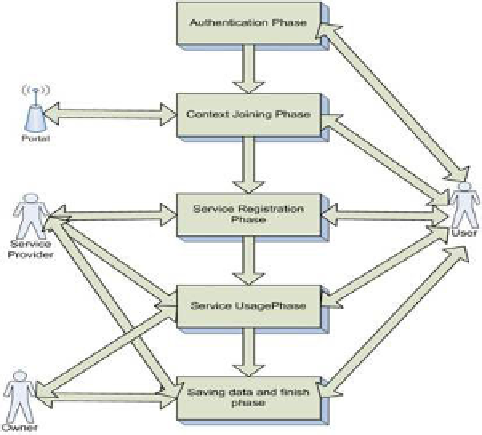
To start using a service, user sends requested service privacy level to the ser-
vice provider. Service provider has preferred identity, location, and time privacy
for each service that it provides in service provider privacy policy file.
Fig. 1.
Model phases
In service registration phase, if service provider would be able to provide user
requested privacy level, then it sends service usage key to the user otherwise user
will not be able to use that service. The agreed privacy policy would be written
in user privacy policy and service provider privacy policy files that consist of the
agreed ID, location, and time privacy.
There is an information space tag for each content part of a service on the
service provider, each of which defines time and location privacy of related con-
tent part. In service usage phase, service provider should get assurance that user
provides requested content privacy level before sending content to the user.
When user finishes using a part of the content or tries to save the content,
system first applies content privacy policy on the saved content part, so that in
future access to the content, user needs to provide required privacy level.
3 Results and Discussion
In this part we measure the UPM unobtrusiveness of privacy policies level and
show that the model unobtrusiveness is less than 10%. Then we discuss the UPM
expressiveness of privacy policies and show the models privacy policies' ability
to support mandatory and discretionary rules, reflecting context sensitive in-
formation, handling uncertain situations, and resolving conflict situations. We
Search WWH ::

Custom Search