Information Technology Reference
In-Depth Information
Ta b l e 1
A purchase protocol expressed in terms of commitments
Domain-specific message
Commitment-oriented message
Offer
(
E,A,
$12,
BNW
)
Create
(
E, A,
$12,
BNW
)
Accept
(
A,E,BNW,
$12)
Create
(
A, E, BNW
, $12)
Reject
(
E,A
, $12,
BNW
)
Release(E, A,
$12,
BNW
)
Deliver
(
E,A,BNW
)
Declare
(
E, A, BNW
)
Pay
(
A,E,
$12)
Declare
(
A, E,
$12)
Table
1
shows an alternative purchase protocol specified in terms of com-
mitments. The semantics of domain-specific messages are explained in terms of
commitment operations. For example, an
Offer
message is interpreted as a
Create
operation, whereas a
Reject
message releases the debtor from the commitment.
Let us walk through the interaction of Fig.
2,
which shows a possible enactment
upon receiving the message Alice infers
c
B
. Upon sending
Declare
($12), Alice
infers that $12 holds. Consequently, she infers that
c
B
is detached, yielding
c
UB
.
When EBook receives
Declare
($12), it infers
c
UB
. EBook finally sends
Declare
(BNW), thus concluding that its commitment is discharged. When Alice receives
Declare
(BNW), she draws the same inference.
Notice that Table
1
does not specify any ordering constraints on messages. In
effect,
each party can send messages in any order
. Figure
3
shows some additional
So when is an agent compliant with a protocol? The answer is simple: an agent
complies if its commitments are discharged, no matter if delegated or otherwise
Ta b l e 2
Commitments used
as running examples in this
chapter
Name
Commitment
c
A
C
(Alice, EBook, BNW, $12)
c
B
C
(EBook, Alice, $12, BNW)
c
UA
C
(Alice, EBook,
T
, $12)
c
UB
C
(EBook, Alice,
T
,BNW)
Fig. 2
An enactment of the
protocol of Table
1
in terms
of (
a
) domain-specific
messages and (
b
)
commitments. We show only
the strongest commitments at
each point. For example,
because
c
UB
is stronger than
c
B
,
c
UB
is sufficient





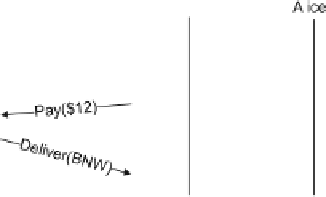

















Search WWH ::

Custom Search